Network security statistics show that the human factor accounts for ~80% of breaches. Protecting your organization’s data entails more than merely preventing the cyber attack vectors. It is also important to minimize the exposure of sensitive information within the company’s own network.
Data Security Posture Management (DSPM) is essential for strengthening an organization’s cyber security posture in the face of data breaches. DSPM vendors and network security software may identify and categorize structured and unstructured data across several cloud service platforms, providing network insight into sensitive data and user access levels.
This article gathers the top 6 real-world DSPM use cases, highlighting how security teams can use them to discover security and privacy issues across business processes.
1. Data discovery
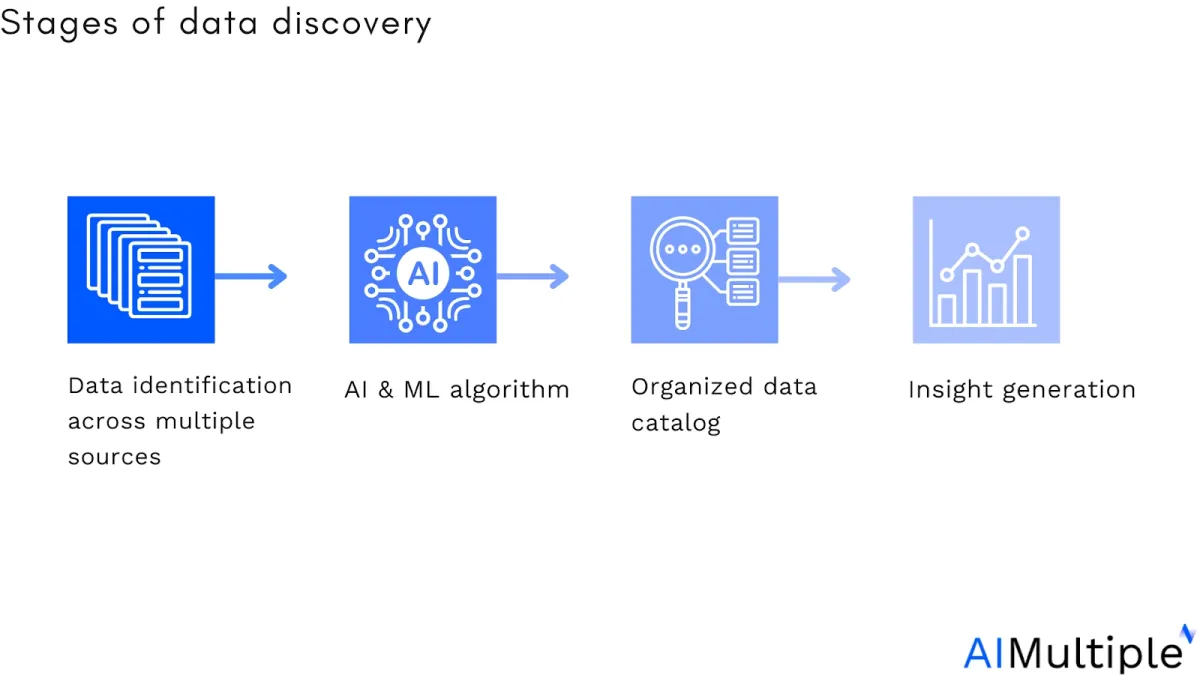
Organizations can use DSPM solutions to enable network visibility into their cloud data inventory, which includes numerous services that contain sensitive data across IaaS, PaaS, and DBaaS setups. This could include cloud warehouses such as Google BigQuery, or Snowflake; databases on virtual machines; and object storage such as Google Cloud Storage.
For example, DSPM companies can detect shadow data assets, such as unsupervised databases residing across their environments.
Figure 1: Shadow IT discovery
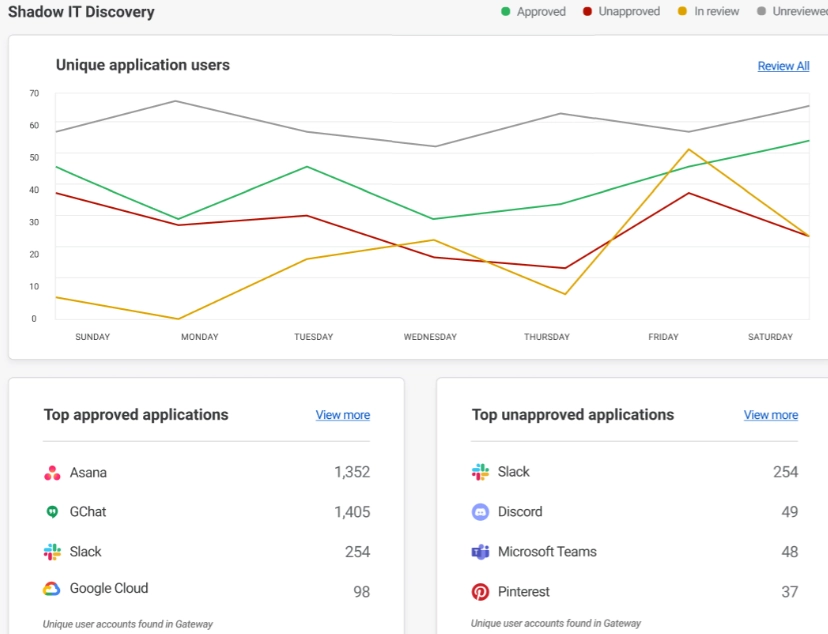
Source: Cloudflare1
Real-life case study
Uniper is an energy transition company, headquartered in Germany and operating in over 40 countries. Uniper provides energy supply for more than 1,000 wholesale and industrial customers.
Challenges
- Insufficient data discovery: Uniper required an easy approach to make data discoverable and available to anyone, whether at their workstation or on mobile devices.
- Slow data access: Uniper employees had to make critical judgments quickly in a complicated, high-stakes, and rapidly changing operating environment. However, the time spent searching for and accessing data slowed decision-making.
- Lack of continuous data flow: Uniper engineers needed to retrieve data flows from power plant setups to maintain quality controls, however, they were limited to data from a single plant database. Engineers lacked a centralized data set that is constantly upgrading.
Solutions and outcome
Uniper signed Cognizat, a network security software company to improve the speed and quality of decision-making by making business data easily discoverable. Cognizant used the DSPM solution to create a data search engine.
- Improved data discovery: Uniper and Cognizant collaborated to identify data owners and create an inventory of shareable data throughout the enterprise. This helped to classify and share datasets, improving data discovery.
- Fast data access: Before the DSPM implementation Uniper spent 70% of their decision-making time seeking information. The new platform provided faster results from a larger collection of shared datasets and sources and the search time has been decreased to 10%.
- Automated data labeling: Uniper added automated features to increase platform value and usage. The features included AI/ML-driven recommendations for relevant data sources and a rating system to help users choose the best datasets from search results.2
Read more: AI-SPM (AI-Security Posture Management)
2. Data classification
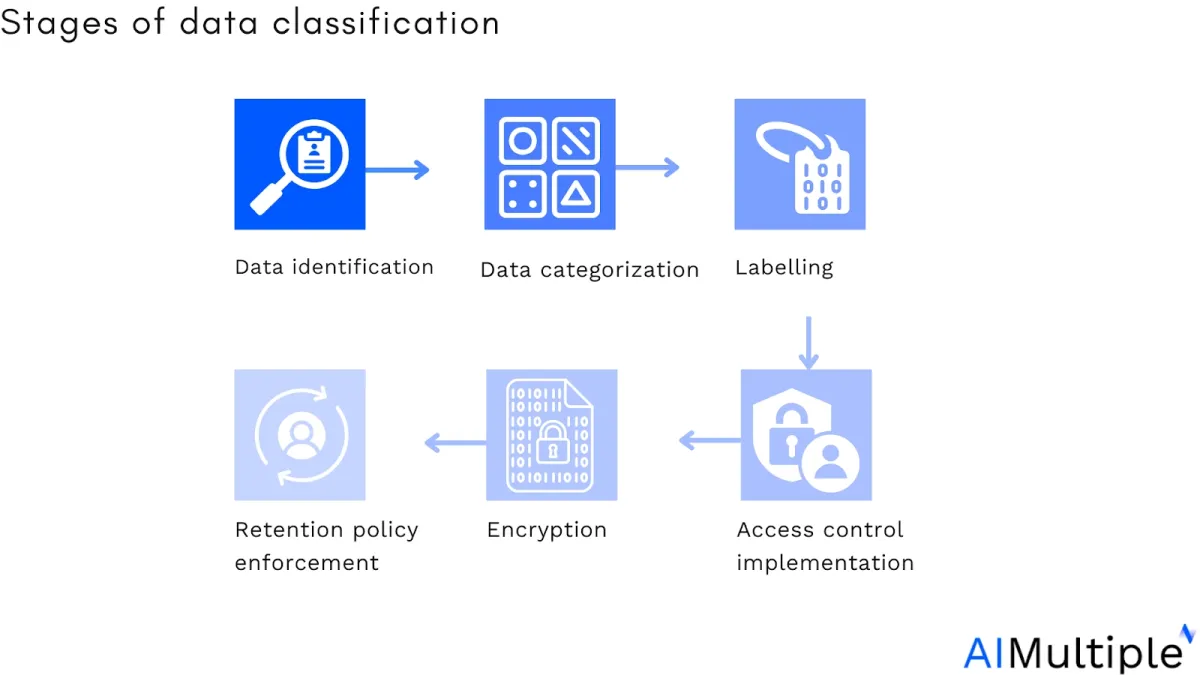
Organizations can manage all of their structured and unstructured data by using DSPM products. DSPM can identify and classify data by scanning the whole network to discover data locations, including the cloud, physical endpoints, employees’ devices, and elsewhere.
For example, organizations may categorize data based on its types as accounting information, marketing information, and intellectual property. Other businesses may categorize data according to applicable standards, such as the Health Insurance Portability and Accountability Act (HIPAA).
Additionally, organizations can leverage AI data classification by combining data classification software with DSPM vendors with automation capabilities that employ machine learning, AI, and pattern recognition to evaluate structured and unstructured data and decide what type of data it is and if it is sensitive.
Figure 2: Data classification template
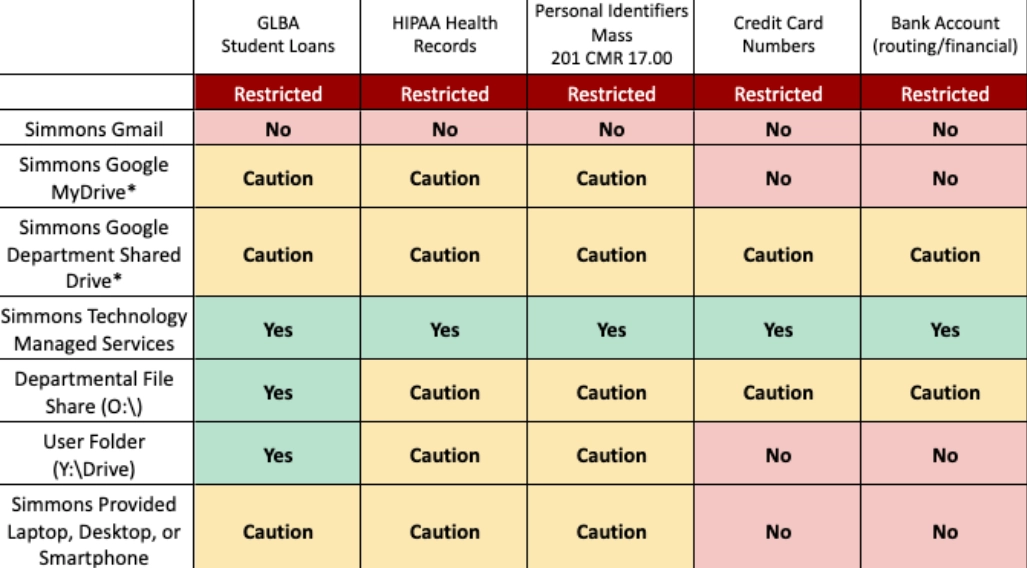
Source: Simmons University3
- Yes – use permitted.
- Caution – this service with the regulated data type is permitted with caution and, where necessary, approval.
- No – use prohibited.
Real-life case study
First National Bank is a financial service organization based in St. Peter, Minnesota, with branches in Gaylord, Belle Plaine, and Mankato. The bank secured its sensitive data and rebuilt its Active Directory in three weeks using an IT audit solution.
Challenges
- Data classification: First National Bank classified its data to verify sensitive financial information, such as income verification, Social Security numbers, and job history.
- Complex Active Directory data flow: Rebuild Active Directory to minimize complexity and increase security.
Solutions and outcome
The Bank implemented a network security solution to secure its sensitive data.
- Data security posture management (DSPM): First National Bank discovered, classified, and protected sensitive data. For example, the solution ensured that data is stored only in secure areas and that only authorized users have access to it. The Bank gained insight into where data is stored and what information is encrypted, relocated, or cleaned.
- Faster detection of suspicious activity: First National Bank detected suspicious behavior in all business-essential IT systems daily by receiving activity reports and notifications based on data types. For example, the new solution sent access notifications to the IT risk management and executives when a user applied modifications to highly sensitive financial files.4
3. Data loss prevention (DLP)
Organizations can use DSPM for data loss prevention (DLP) to prevent unauthorized access, data leakage, theft, and malicious processing of sensitive data. Administrators can set DLP policies that specify how users should handle corporate data.
For example, your organization’s internal auditors can keep track of a list of credit card numbers based on data types (e.g. credit card numbers) assigned by their DSPM solution.
Furthermore, if one of the users attempts to send credit card numbers in an email to external parties, the DLP software can block the e-mail transaction.
Note: Organizations who expect to enforce more detailed DLP policies can use identity and access management (IAM), which includes role-based access control (RBAC) regulations, that can limit data access to the appropriate individuals.
Read more: Open source RBAC tools, RBAC examples, RBAC use cases.
Real-life case study
Alloy is a major cybersecurity risk management and compliance solution for banks and fintech. The company required a data loss prevention (DLP) solution to prevent the theft of sensitive data such as social security numbers, tax IDs, and other client information.
Challenges
- Ineffective insider threat management: Alloy’s legacy systems were inefficient in preventing insider attacks and accidental loss via endpoints and USB drives.
- Lack of network visibility: Alloy lacked visibility into data transfer activities such as email, printing, and portable media, and expected to improve its data security at the endpoints.
- Low user activity transparency: Alloy required a system that provides transparency into user actions. This includes gaining insight or notifications when users:
- Access a database they have never used before and download sensitive data.
- Download large amounts of data.
- Login critical systems or applications.
Solutions and outcome
Alloy employed an approach that included setting policies to improve visibility into user actions, monitor data transfers, and detect specific keywords and sensitive information. The company also adopted security measures such as USB port blocking to prevent data exfiltration.
- Scanned data in motion: Alloy gained detailed control via content and context inspection. For example, administrators could monitor the files exchanged with coworkers, data uploaded to cloud apps, and data delivered to business partners on a single interface screen.
- USB and peripheral port control: Alloy scanned data in motion with the new implementation this allowed the company to become aware of infected devices. Thus, Alloy could lock down these equipment based on vendor ID, product ID, serial number, and more. For example, the software switches off USB device power when a device gets infected with malicious data, then sends a signal to the device indicating that the infected hardware is disconnected.5
Read more: DLP software.
4. Data maps and pipelines
Organizations can leverage DSPM systems to generate data maps by identifying data sources while assessing the data pipelines. They can detect and identify shadow data repositories and unprotected data pipelines. They can also detect misconfigurations that may expose data to public or unsuitable destinations, or allow third-party access.
Real-life case study
A healthcare-focused cloud services company constantly collects data from its customers, and this data flow is an important component of the onboarding process for new customers.
Challenges
- Data is distributed in multiple forms: Their consumer data was in multiple formats and contained discrepancies. Sometimes consumer data was missing or poorly formatted. Some clients manually entered their information using varying standards. Duplicate records existed.
- Over-hiring employees and excessive software implementation: The company addressed the “distributed data” issue by recruiting more employees to process customer information using various programs such as Microsoft Excel. However, this did not resolve their issue. Despite rising prices, data quality issues persisted. Even with more people, the data flow slowed new customer onboarding.
Solutions and outcome
The company officials implemented an automated solution to assess their data workflow, data quality issues, and sample data input procedure.
- Streamlined data pipelines: The company designed the new implementation in 4 weeks and cut customer data preparation time by 75% in 6 months.
- Data scans and categorization: The application scanned a set of Excel and delimited text files provided by the company and determined their structure. For example, if the majority of the data in a column appears to be an email address, the software applies an “email” filter.
- Data identification and mapping: An Excel spreadsheet created to define business rules. The program read the source data and corrected common data quality issues that it identified. For example, if a numeric column in the file contains a string the software turns coded cells in red to indicate unrecognized data quality problems.6
5. Data security policy enforcement
DSPM solutions will alert you and flag security violations for remediation based on data location, movement, or type. DSPM allows organizations to:
- Data monitoring: Monitor security posture drift against prebuilt policies aligned with best practices, governance structures, and privacy laws.
- Network security policy management: Customize existing policies or develop your own to meet specific corporate needs.
- Incident response automation: Integrate with your current ticketing and workflow applications and receive violation notifications and remedy guidance.
With automated data security policy implementation, organizations can target violations such as:
- Overexposed data — public reader access, excessive user access, third-party access, and underused internal access. Read more: Third party risk management.
- Unprotected data — missing encryption at rest, masking, encryption in transit, unencrypted credentials, and activity logging.
- Misplaced data — European Union citizen data outside of GDPR countries, and personal, healthcare, and banking information in less secure settings (e.g. development, test, and staging).
- Redundant data — failed backups and sensitive data in dismissed assets.
Real-life case study
A telecommunication company offers cloud-based call tracking and analytics solutions.
Challenges
- Lack of multi-cloud security: The customer’s multi-cloud design includes Microsoft Azure and Amazon Web Services (AWS) to improve overall security. Their cloud workloads and sensitive data are prone to misconfiguration and being shared by other organizations.
- Lack of automated data security policies: Initially, the company used a single AWS account and followed naming and tagging guidelines to distinguish production and development workloads, however, as their network grew they failed to divide their environments.
- SOC 2 network audit: The company needed to prepare for the SOC 2 audit. Thus, the company needed to provide regular data reporting of operations to the IT advisory committee.
Solutions and outcome
The company applied a new architecture that could execute vulnerability management and policy automation across multi-cloud and multi-account environments. The company claimed that its internal security score has increased from ~15% to ~50%. The following outcomes have been achieved.
- Automated data security policy implementation: The company used the AWS Control Tower tool to create several organization units (OUs) and AWS accounts, each with a distinct purpose. This helped pre-configure data security policies to ensure secure account setup and maintenance on organizational units.
- Vulnerability monitoring: The company used AWS Inspector, an automated vulnerability monitoring tool, to scan its cloud workloads continuously. This approach helped to detect and address any vulnerabilities.7
Read more: Network security policy management tools.
6. Data-centric environment segmentation
Organizations segment their network environment to control traffic flows between the subnets, however, network segmentation cannot be manually implemented and enforced in dynamic cloud systems. DSPM assists organizations in segmenting cloud environments and implementing location restrictions to meet security and regulatory needs.
Real-life case study
Careem is a transportation and delivery services application with operations in more than 70 cities, covering 10 countries. Careem replaced its existing security architecture, which includes more than 50 firewalls and dozens of virtual private network (VPN) equipment, with a zero-trust approach.
Challenges
- Low granularity across internal apps: Careem needed a solution with granular segmentation features in its new system to securely allow acquired employees quick access to internal apps while also providing existing Careem colleagues secure access to acquired corporate assets.
- Lack of customized access controls: The company needed conditional access control to applications based on dynamic data security posture evaluations of endpoint devices.
Solutions and outcome
Careem removed VPN-related hassles and expenditures by implementing a zero-trust approach. The company claimed that their net promoter score (NPS) among our colleagues and service representatives has increased by 70%.
- Improved cloud workload security posture: Careen expanded its new network implementation by integrating A DSPM vendor into workload communications. This helped the company to correct misconfigurations, secure sensitive data, and enforce least-privileged access across Careem’s AWS environments.
- Automated access controls: Careem allocated user access controls based on data classification. This helped the company to configure who should have access to sensitive data and what level of access they should have. For example, unauthorized visitor devices are directed to the secure gateway. Similarly, unidentified devices are put into the “denylist” zone. Thus, Careem achieved significant resource savings by dividing its network, approximately 20,000 development hours annually.8
Read more: Network segmentation tools, examples of network segmentation.
Top 6 security risks that DSPM can mitigate
1. Shadow backups
Consider a database holding sensitive data that has been duplicated to an unencrypted Amazon cloud object storage that is not maintained by the core technical team.
DSPM can automatically analyze all Amazon cloud objects containing sensitive data, classify them (PII, PCI, HIPAA, etc.), assess the risk, and notify the security team.
2. High-risk data flows
Consider a sensitive data record acquired via a web app, saved in CosmosDB, backed up in Azure Blob Storage, and then enriched and connected to SQL Server for analytics.
In such a case, the organization will lack insight into each service’s security posture. For example, it could be difficult to observe who has access to sensitive data at each stage.
DSPM helps map the data flow between services and storage locations, highlighting who accessed to data, when data is accessed, etc.
3. Data leak caused by an unsupervised database
Assume that an operational database is replicated into a Windows virtual machine during a database migration. The security team may be unaware that this VM is running a database.
DSPM can identify that the VM is running across a database and can notify the security team in real-time so that the security team can take action to avoid exfiltration.
4. Snapshot leakage
Consider a company with an isolated and unused database that is currently being shared with an unknown user.
DSPM solutions can detect when an unused database is shared and notify security personnel.
5. Broad user access permissions
An administrator who gives permissions to a large range of users for a specific project might fail to remove them.
DSPM tools can identify any data stores containing client records and provide security teams the ability to identify who has access to them. Thus, security teams can observe that a database containing confidential data has been shared with an entire team or company in a workspace and determine whether these rights are required.
6. Sensitive information copied by an outsider
Consider a data engineering team utilizing AWS Glue (a data integration tool) to migrate sensitive data to a BigQuery database. The company also uses the same connection to move several customer records from BigQuery shared with outside vendors. In this situation, it might be difficult to follow data movement.
DSPM solutions can detect product data, vendor data, and who accesses each data store, allowing security teams to follow sensitive data movements.
4 key takeaways about DSPM solutions
1. Organizations will adopt DSPM solutions to address shadow data
By 2026, more than 20% of companies will have used DSPM technology due to the urgent need to discover previously unknown data repositories also referred to as “shadow data”.
DSPM vendors will become key players in detecting and mitigating the risk of shadow data. Gartner claimed that DSPM had less than 1% market penetration in 2022, and they expect it to rise to 20% over the next several years.9
2. Existing data security technology cannot meet cloud needs
Traditional data security solutions (e.g. cloud service providers or CSP-native tools) designed for steady slower on-premises systems can be insufficient to track these cloud deployments since these tools:
- can’t execute frequent reconfiguration
- only identify data in known repositories, leaving shadow data vulnerable.
3. DSPM vendors are critical for strong multi-cloud data security
By 2027, 75% of employees will acquire, change, or develop technology outside of IT’s visibility, up from ~40% in 2022. Shadow data is becoming more recognized as a risk by security specialists.10 The production of shadow data is unavoidable, companies need to build centralized visibility that allows security experts to view multi-cloud and create automated rules for data governance.
DSPM solutions provide a unified management console for assessing data risk across several cloud repositories. This central console is one of the most significant advantages of a DSPM solution. It gives a unified picture of your multi-cloud ecosystem.
These centralized data capabilities will enable security teams to detect and classify data, and then continually customize policies. This will ensure that organizations have precise data maps indicating who may access and utilize the data asset.
4. Data assets are a critical component of DSPM vendors
Compare DSPM solutions to determine their capacity based on your business’s needs. Ensure that the DSPM solution has several data discovery and classification features to secure complete protection.
When researching DSPM solutions, seek vendors that provide several data assets such as databases, pipelines, and files. data warehouses, lakes, and analytics pipelines. Also, verify that the DSPM tool supports multiple subsets of each integration, such as multiple self-hosted databases with distinct setups, and various file formats such as JSON or Office.
Key software to integrate with DSPM vendors
- NCCM software: Control and manage changes in network infrastructure.
- Network security policy management solutions (NSPM): Create, develop, and manage policies and procedures for protecting an organization’s network and data from restricted user access.
- Network security audit tools: Detect risk factors, vulnerabilities, and risky activities to help organizations reduce the effect of most cyber attack vectors.
- SDP software: Distribute access controls to internal applications based on a user’s identification.
- Open source RBAC tools: Assign user access roles and duties based on permission levels to avoid loose network access.
- Open source microsegmentation tools: Isolate a network into segments and implement security rules according to each section’s requirements.
- Network performance monitoring tools: Monitor and evaluate network performance to discover and fix problems such as excessive latency, lost connections, and poor performance.
Further reading
- Role-based Access Control (RBAC)
- Network Segmentation: 6 Benefits & 8 Best Practices
- 80+ Network Security Statistics
AIMultiple can assist your organization in finding the right vendor.
External Links
- 1. Introducing Shadow IT Discovery.
- 2. Uniper Data Discovery Solution | Cognizant.
- 3. Data Classification & Secure Storage Policy : Technology : Faculty & Staff : Simmons Internal.
- 4. Bank Secures Sensitive Data and Rebuilds its Active Directory.
- 5. Alloy Case Study | Endpoint Protector.
- 6. Data Pipeline Case Study - ServiceLaunch. ServiceLaunch, Inc.
- 7. Uplifting Multi-Cloud Security Posture | FPT Software.
- 8. Careem Case Study | Customer Stories | Zscaler.
- 9. 3 Exciting New Trends in the Gartner Emerging Technologies Hype Cycle.
- 10. Gartner Unveils Top Eight Cybersecurity Predictions for 2023-2024.



Comments
Your email address will not be published. All fields are required.