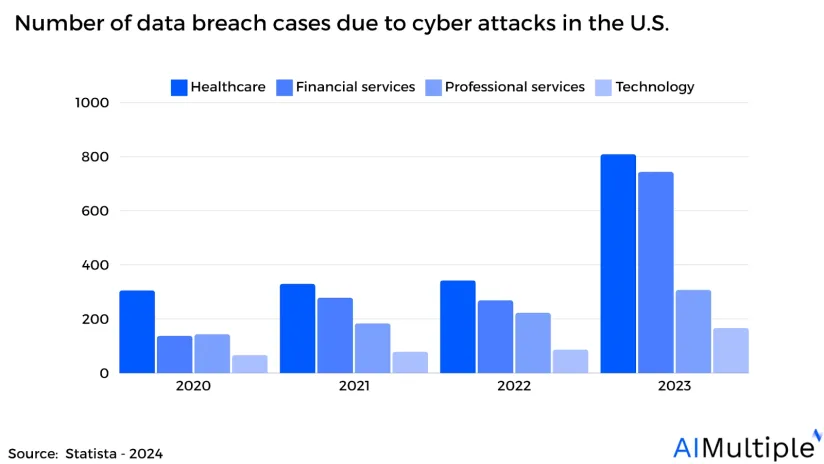
Network security statistics show that the total amount of data breaches has more than doubled in the last three years rising to 1,300+ cases from ~600. Network segmentation tools can help organizations build a finer-grained network to prevent breaches. Here are the top 7 real-life network segmentation use cases and examples:
1. Demilitarized zone (DMZ) segmentation
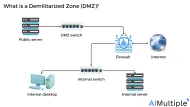
Organizations that frequently use Internet-facing servers (e.g. web servers, proxy servers) can limit damage from data breaches by maintaining their servers in a separate DMZ. The logic behind DMZ network security is isolating internet-facing servers from internal company resources.
Example
In Figure 1, a single firewall with two DMZ (demilitarized) zones and one internal zone is illustrated. The red arrows in the figure above represent the allowed direction of data traffic.
Figure 1: Illustration of DMZ segmentation
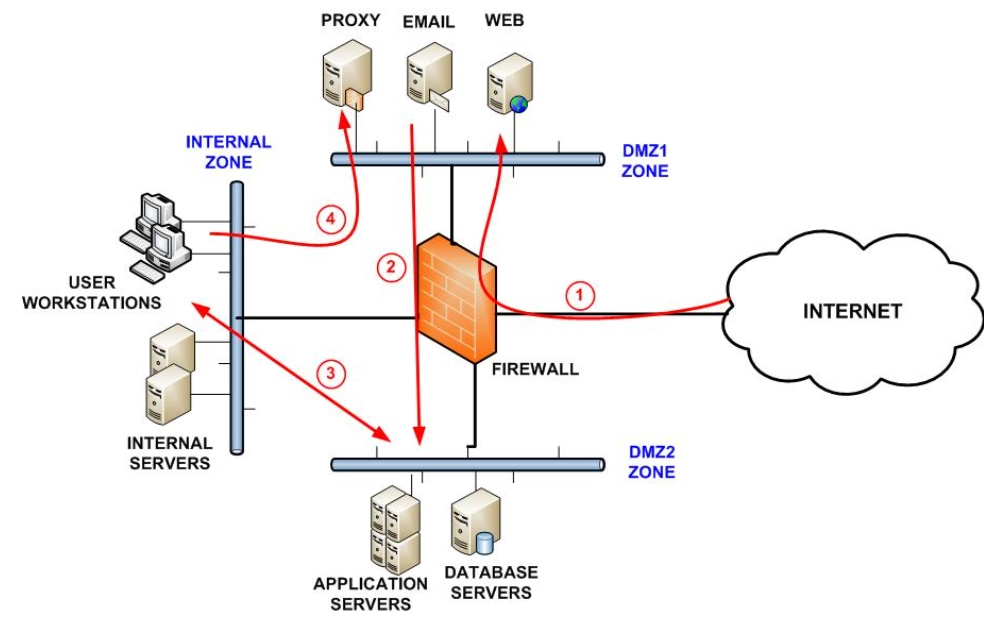
Source: WebTitan1
Real-life case study
A major chemical industrial organization with several important sites identified deficiencies in its industrial controls.
Challenge
The chemical organizations required tight controls due to the use of hazardous chemicals.
OT isolation from the Internet: The primary problem was minimizing risks related to their industrial infrastructure due to insufficient segmentation between IT and OT networks, OT isolation from the Internet, and lack of network and mandatory access control.
Solution
The company used a DMZ security approach with zero trust reference architecture to set up remote access servers.
The company allowed data to flow from OT to IT networks while preventing information from being sent from IT to OT networks.2
Read more: SDP software, network security audit tools, NCCM software.
2. Firewall segmentation
Companies can use an internal segmentation firewall (ISFW*) to protect network segments against malicious code.
Example
Figure 2 illustrates a medium-sized corporate network that uses an edge firewall to segment Internet and VPN connections.
Figure 2: Internal segmentation firewall (ISFW) reference architecture
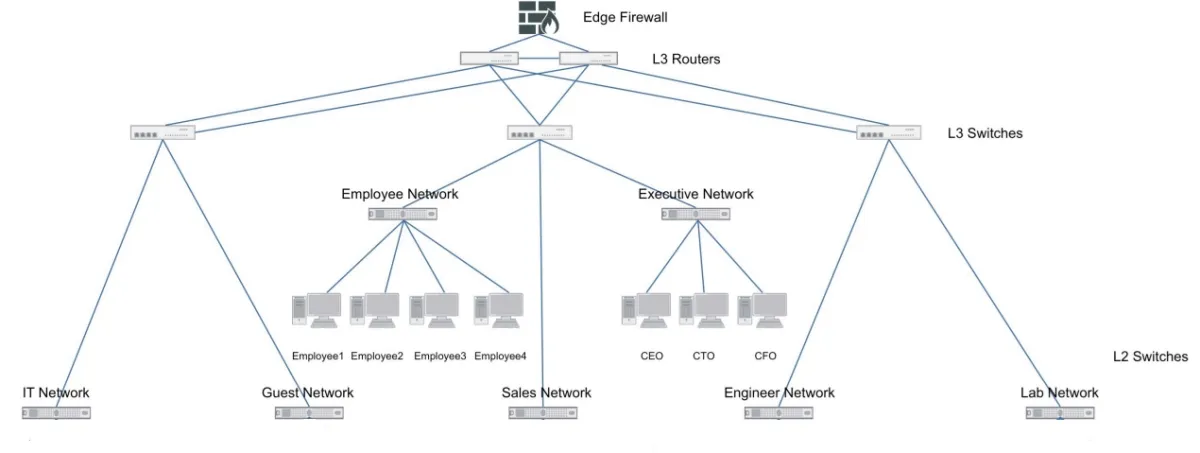
Source: Fortinet3
- The first L3 switch serves the “IT and guest” networks.
- The second switch connects the “employee, sales, and executive” networks.
- The third L3 switch connects the “engineering and lab” networks.
With ISFW Administrators can segment data flow by department (e.g., HR, sales), or by function (e.g. engineering, lab).
Consider ISFW #2 which oversees the Employee, Sales, and Executive networks. In this case, ISFW #2 secures the Employee, Sales, and Executive networks using five ISFW segments.
Thus, if a salesperson brings in a laptop from an outside network location, the ISFW segment can detect possible dangers, manage access to vital resources, and address any issues.
Figure 3: ISFW #2 connecting the employee, sales, and executive networks
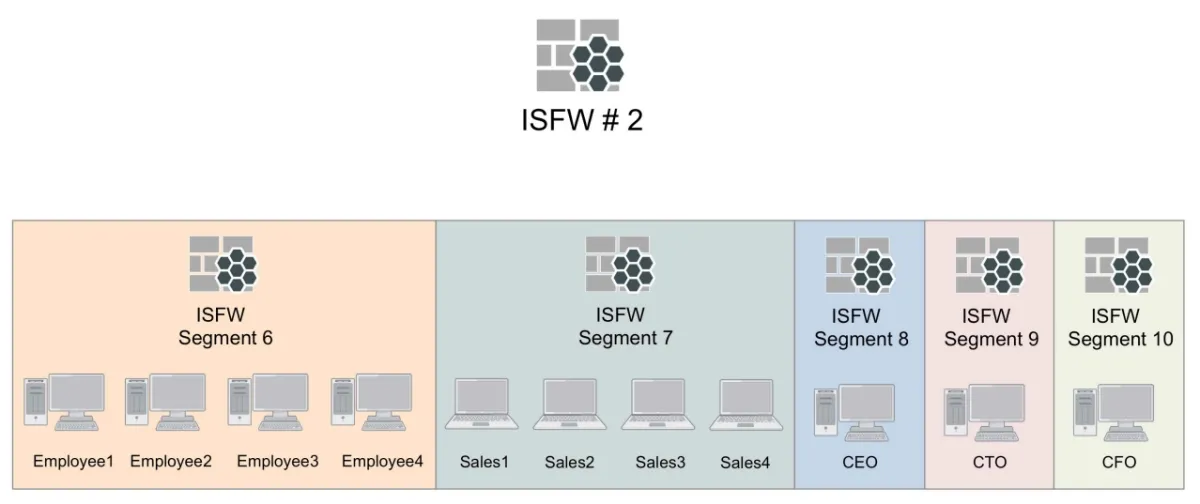
Source: Fortinet4
Case study
A manufacturing company is expected to move from an open, flat network to a best-practice segmented architecture across several regions.
Challenge
The traditional firewalls did not provide granular peer-to-peer connections between network elements. As a result, the company’s networks were exposed to pass-the-hash attacks and ransomware through lateral movement across endpoints.
Solution
The company deployed internal firewall segmentation approximately at 2,000 workstations.
Enhanced visibility: The company’s infrastructure architect stated that network visibility has improved by 1,000% and now covers PC-to-PC conversations. This helped the company to delve down into the activities of a single machine while analyzing application-level activity.5
Read more: Firewall assessment, attack surface management (ASM) software.
3. SDN segmentation
Cloud-native organizations can use a virtual architecture SDN segmentation solution to divide a network into many parts, each serving as its subnetwork to create barriers between OT and IT networks.
Example
Figure 4 illustrates one possible SDN segmentation approach that a manufacturing network can employ. This segmentation method creates four virtual networks: Building, Enterprise, IDMZ, and Factory. Intercommunications are only allowed through the firewall across these four networks.
For example, the Enterprise VN has customizable groups set up for various categories of users (PL, EM, AC, CO, SU, HR). Each group’s access to resources in the data center or elsewhere is limited.
Figure 4: SDN segmentation in manufacturing
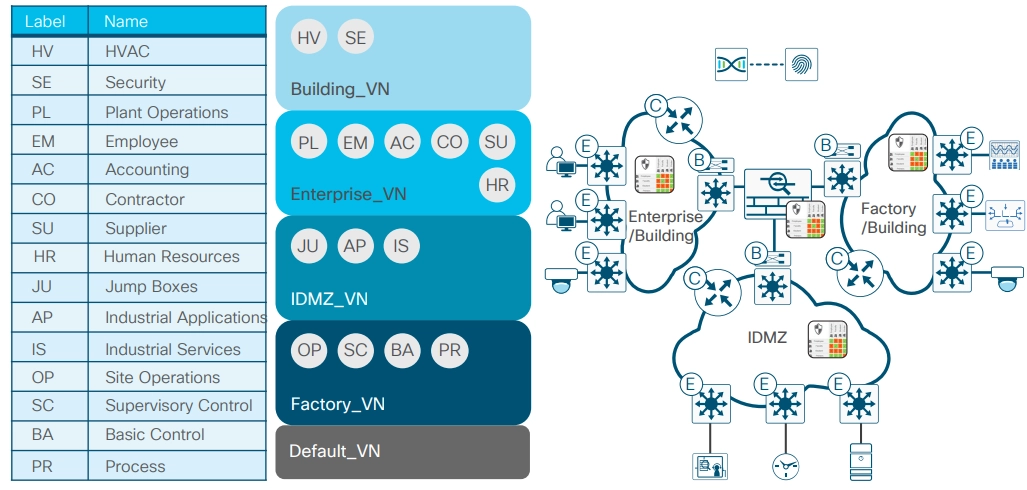
Source: Cisco6
Case study
The County Drain Commissioner Division of Water and Waste Services (GCDCWWS) required access to SCADA and business system data while maintaining privacy between the water treatment facility.
Challenge
GCDCWWS needed a system that optimized access, visibility, and inspection across 150 separated water and wastewater pumping and storage facilities
Solution
GCDCWWS enhanced its security approach by using an OT network controller (an OT-SDN software platform).
Rule-based, zero-trust OT segmentation: The OT-SDN software platform allowed centralized management of the industrial control network and adhered to rule-based, zero-trust OT segmentation. This ensured that networked devices (e.g. pumps, gauges, water, and wastewater pumping) could not connect without explicit permission.7
Read more: Microsegmentation use cases.
4. Segmenting IoT over wireless networks
Organizations with large numbers of employees, partners, and third-party device users, may be required to welcome external home/IoT or guest devices. These organizations can implement IoT segmentation to:
- Control communication routes between IoT and the internet.
- Manage the Internet and IoT connection channels.
Example
Administrators may set up a distinct subnetwork for devices in an institution, restricting access to important data and resources.
Table 1 describes several users and devices, and how we will allow access to each. Internal users utilize Active Directory (AD) credentials to access the Eduroam (a shared wireless network) 802.1X WLAN.
Table 1: Device types and authentication methods
| WLAN | Eduroam | Home/IoT network | Guest network |
|---|---|---|---|
| Authentication Methods | 802.1X or EAP-TLS | MAC authentication with device registration | Self-registration with MAC caching |
| Users | Internal AD users and external Eduroam members | External home and IoT device users | Guests with no AD account |
| SSID Type | WPA2-AES | Open | Open |
Source: Aruba Networks8
- Internal AD users and external Eduroam members can connect with an EAP-TLS certificate by enrolling in a cloud public key infrastructure (PKI).
- External home and IoT device users who do not support 802.1X or MAC authentication are enforced or registered to connect accounts to registered devices.
- Guests with no AD account from other countries can use their Eduroam credentials to access institutions’ WLANs.
5. VLAN segmentation
Administrators may conceptually divide a local area network (LAN) into numerous broadcast domains by using a virtual local area network (VLAN) segmentation.
Example
Example: The example below shows a VLAN setup for segmenting imaging modalities and diagnostic equipment on a medical network for a medium healthcare organization.
- A network administrator can set up a connection between MAC addresses “00:B0:D0:63:C2:26” and VLAN IDs “imaging modalities 1”.
- If switches “switch 4 or switch 3” receive a tagged VLAN number from “imaging modalities 1”, the VLAN tag is added to the MAC address and then sent across the selected VLAN.
- Thus, receiving and forwarding incoming data from “imaging modalities 1” into a network will be based on media access control (MAC)-to-VLAN connection.
Table 2: Sample VLAN setup for imaging-connected diagnostic equipment
| VLAN name | VLAN numbers | MAC adresses | Switches | Switch port numbers |
|---|---|---|---|---|
| Imaging modalities 1 | 10 | 00:B0:D0:63:C2:26 | Switch 4 Switch 3 | Fa0/19 Fa0/14 |
| Imaging modalities 2 | 20 | 00:C1:D4:33:D6:35 | Switch 2 Switch 1 | Fa0/9 Fa0/4 |
| Clinical application | 30 | 00:1B:44:11:3A:B7 | Switch 4 Switch 3 | Fa0/17 Fa0/13 |
| RIS | 40 | 00:D1:45:6W:A0:F7 | Switch 2 | Fa0/9 |
| PACS | 50 | 00:B9:83:53:F3:B0 | Switch 2 | Fa0/8 |
| VNA | 60 | 00:22:16:00:G2:C5 | Switch 4 | Fa0/3 |
| Image viewer 1 | 70 | 00:D2:55:13:B9:D2 | Switch 4 Switch 3 | Fa0/18 Fa0/12 |
See the explanation of virtual local area network (VLAN) configurations in Table 2.
Disclaimer: The above VLAN segments are suggestions and not a complete list. Users can configure VLANs depending on their security needs.
6. VPN
Companies can set up a network with a VPN connection and only include work-related devices. This ensures that your professional communication remains secure and does not interfere with the functioning of other devices.
6.1. Remote access VPN
Virtual private networks (VPNs) can be used to segment networks by creating encrypted tunnels between network components. Remote access VPNs may be beneficial in a variety of contexts, including:
- Employees who work from home.
- People who desire to avoid geographic limitations, such as accessing Netflix content in another country.
Example
A remote user can use a VPN customer software to connect to the company headquarters in the San Jose network over a secure Internet tunnel connection.
In this example, the remote user will only have access to “hq-Sanjose” hardware and will be restricted to accessing the “corporate server” and “web server” hardware.
Figure 6: Remote access VPN scenario
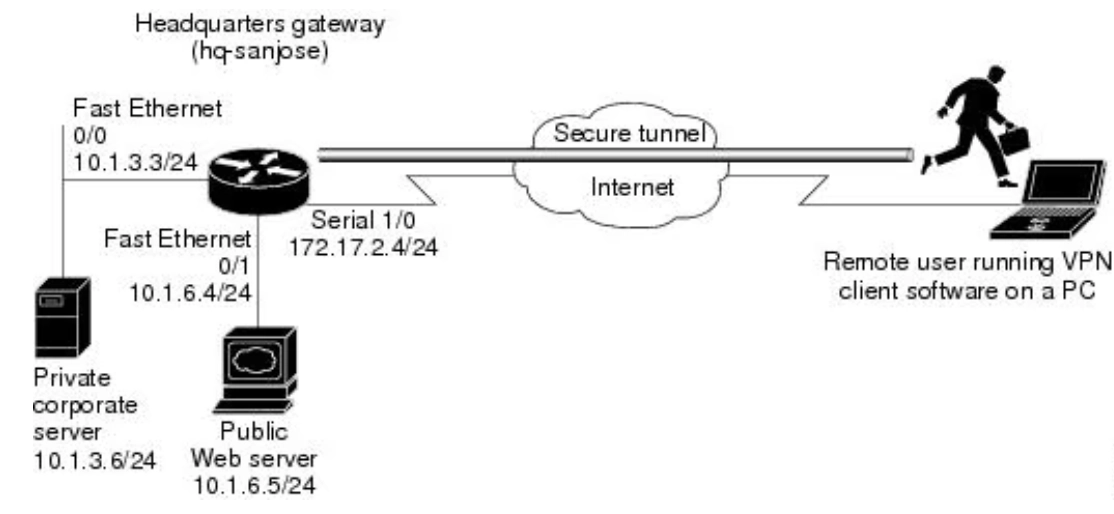
Source: CISCO9
Table 3: Lists the physical elements of the remote access VPN scenario
| HQ site hardware | HQ WAN IP address | HQ ethernet IP address | Remote user site hardware | Remote user WAN IP address |
|---|---|---|---|---|
| HQ-sanjose | Serial interface 1/0: 172.17.2.4 255.255.255.0 | Ethernet interface 0/0: 10.1.3.3 255.255.255.0 | PC running VPN client software | Dynamically assigned |
| Corporate server | — | 10.1.3.6 | — | — |
| Web server | — | 10.1.6.5 | — | — |
CISCO10
6.2. Site-to-site VPN
Companies can segment their network by using a site-to-site virtual private network (VPN) that creates links between multiple networks in which numerous offices collaborate.
A site-to-site VPN may provide all locations with complete access to the application as if it were hosted within their physical facility. For example, the Linux machine hosted on AWS Cloud can be linked to a local PC over a virtual private network at a distant office in Europe.
Figure 7: Site-to-site VPN
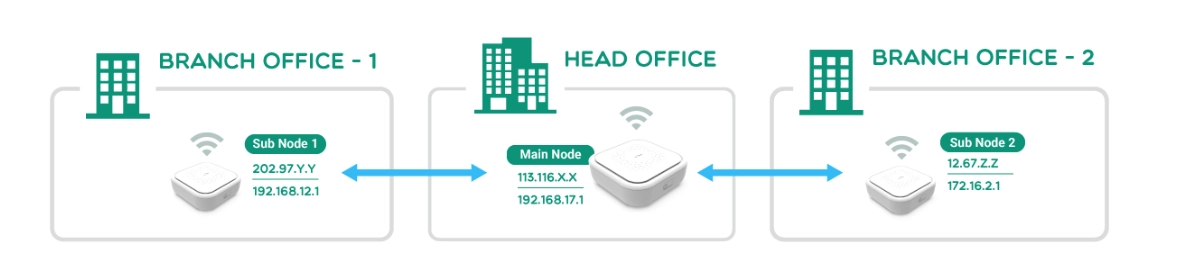
Source: GL-iNet11
Companies with multiple offices spread across wide geographical areas can leverage site-to-site VPNs. Site-to-site VPNs are typically used in the following scenarios:
- To connect two offices of the same firm to facilitate and secure file exchange.
- To connect several campuses within the same institution to improve resource sharing.
- To link numerous departments who are working together on a project.
7. PCI DSS compliance
Retail, banking, and healthcare organizations can then use host-based network segmentation to enforce the relevant firewall rules, limiting inbound and outgoing traffic to the PCI environment to only “allowed” or “legitimate” traffic.
Explanation of virtual local area network (VLAN) configurations
- Imaging modalities VLAN – These VLANs are logical groups of imaging diagnostic devices connected to your organization’s clinical network (e.g. X-ray, MRI, and ultrasound scanners)
- Radiology information system (RIS) VLAN – These VLANs secure RIS for the electronic management of imaging departments.
- Picture archiving and communication system (PACS) VLAN – These VLANs protect PACS images stored and produced by various medical hardware modalities, such as X-ray machines.
- Vendor neutral archives (VNA) VLAN – These VLANs store VNA components that maintain medical images in a common format.
- Viewer VLAN: These VLANs display all switch ports and their associated VLANs used to access images stored in PACS.
Further reading
- Top 10 Microsegmentation Tools
- Top 10 NCCM Software: Based on 4,000 Reviews
- Role-based access control (RBAC)
- Network Segmentation: 6 Benefits & 8 Best Practices
- 80+ Network Security Statistics
- Network Security Policy Management Solutions (NSPM)
AIMultiple can assist your organization in finding the right vendor.
External Links
- 1. Network Segmentation Best Practices to Improve Internal Network Security - SpamTitan Email Security.
- 2. ”Case Study – Zero Trust Architecture for Industrial Environment”. Deloitte. 2021. Retrieved May 14, 2024.
- 3. ”Internal Segmentation Firewall”. Fortinet. 2016. Retrieved May 14, 2024.
- 4. ”Internal Segmentation Firewall”. Fortinet. 2016. Retrieved May 14, 2024.
- 5. Manufacturing Company | Case Study | Akamai.
- 6. ”SD-Access Segmentation Design Guide”. Cisco. 2018. Retrieved May 14, 2024.
- 7. ”Veracity_Case Study Genesee”. VERACITY. 2018. Retrieved May 14, 2024.
- 8. Segmenting and Securing BYOD and IoT with Wireless Networks (Solution Guide) | Security .
- 9. Remote Access VPN Business Scenario - Cisco. Cisco
- 10. Remote Access VPN Business Scenario - Cisco. Cisco
- 11. What Is a Site-to-Site VPN - GL.iNet.


Comments
Your email address will not be published. All fields are required.