With around 22 million U.S. adults (~14% of the total employed population) working from home full-time,1 secure remote access is critical. Zero-trust network access (ZTNA) solutions address this need by ensuring only authenticated and authorized users access sensitive resources.
See top ZTNA solutions with their features such as authentication methods, and user experience:
Comparison of top 10 ZTNA solutions
| Tools | User Rating* | Employee Size** | Free Version*** | Pricing**** | Category |
|---|---|---|---|---|---|
| Palo Alto Prisma Access | 4.3 out of 21 reviews | 16,348 | ❌ | N/A | specialized product |
| Fortinet FortiClient | 4.3 out of 485 reviews | ❌ | N/A | unified platform | |
| Zscaler Private Access | 4.4 out of 53 reviews | 1 | ❌ | N/A | unified platform |
| Cloudflare SASE Platform | 4.6 out of 778 reviews | 4,773 | ✅ | $7 per user per month | unified platform |
| Forcepoint One | 4.4 out of 41 reviews | 1,939 | ❌ | N/A | unified platform |
| Absolute Secure Access | 4.6 out of 334 reviews | 1,050 | ❌ | N/A | unified platform |
| Twingate | 4.8 out of 70 reviews | 78 | ✅ | $5 per user per month | specialized product |
| Ivanti Neurons | 4.5 out of 38 reviews | 8 | ❌ | N/A | specialized product |
| Nord Layer ZTNA | 4.3 out of 104 reviews | 4 | ❌ | $11 per user per month | unified platform |
| Google BeyondCorp Enterprise | 4.3 out of 2 reviews | Not publicly available | ✅ | $6 per user per month | specialized product |
*Based on data from B2B review leading platforms
**Based on data from LinkedIn
***Proof of Concept (POC) option may be available for each product upon request by contacting the vendor.
****Price of the basic option
Ranking: Products are ranked based on their total number of employees except for the sponsored products ranked at the top. Sponsored products can be identified by their links.
Inclusion: Cybersecurity products uses zero trust network access principles are included in the list. The products with zero user review in B2B review platforms are excluded.
1. Palo Alto Networks Prisma Access
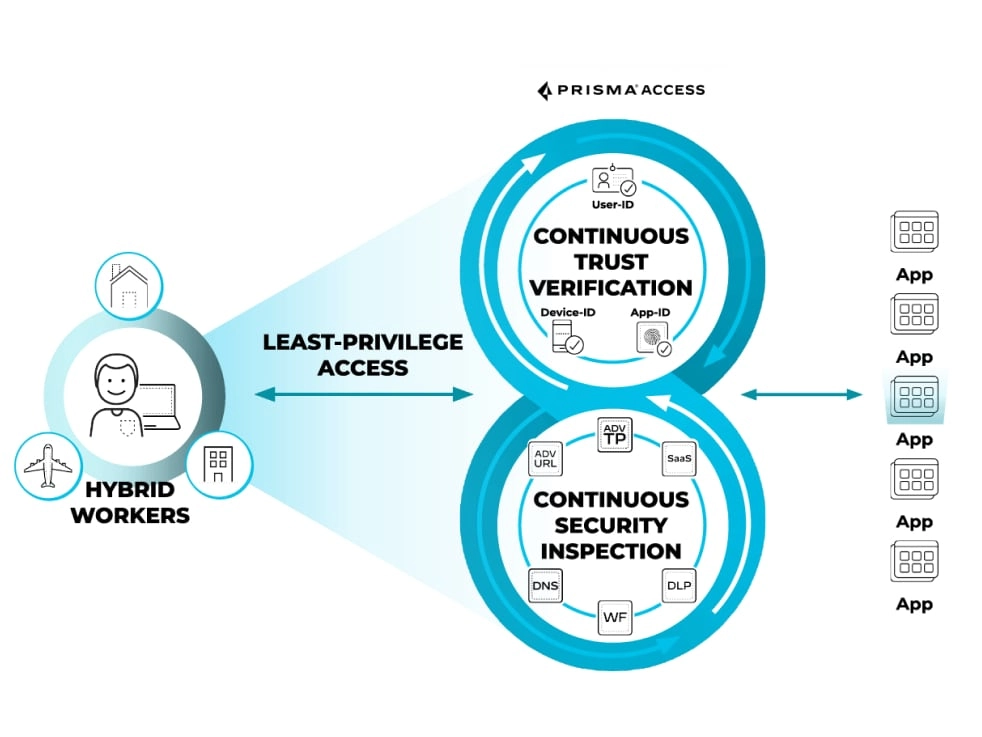
Resource: Palo Alto Network2
Palo Alto Networks offers a cloud-delivered ZTNA solution through its Prisma Access platform. Key features include:
- Secure web gateway (SWG): This feature provides secure access to the web by filtering and monitoring web traffic for potential threats such as malware, phishing attacks, and inappropriate content.
- Cloud access security broker (CASB): CASB functionality provides visibility into cloud usage, enforces security policies, detects and responds to cloud-related threats, and ensures data protection and compliance across cloud environments.
- Firewall as a service (FWaaS): Secure your remote locations against sophisticated threats with a wide range of security services, including Advanced Threat Prevention, URL Filtering, DNS Security, and sandboxing.
Differentiating feature(s):
- ZTNA 2.0: It addresses the increased attack surface from hybrid work and direct-to-app architectures by overcoming the operational complexity, coarse-grained access controls, implicit trust, and limited app/data protection of ZTNA 1.0 solutions.
- Autonomous digital experience management (ADEM): It offers comprehensive visibility and insights into network traffic while providing autonomous remediation capabilities, including end-user self-service options.
Use cases
Hybrid workforce security: Secures remote and on-site employees with consistent security and defined access control policies.
Application and data protection: Protects all application traffic and data, reducing the risk of breaches.
Cloud and SaaS security: Enhances visibility and control over internet and SaaS app traffic, integrating advanced threat prevention capabilities.
2. Fortinet FortiClient
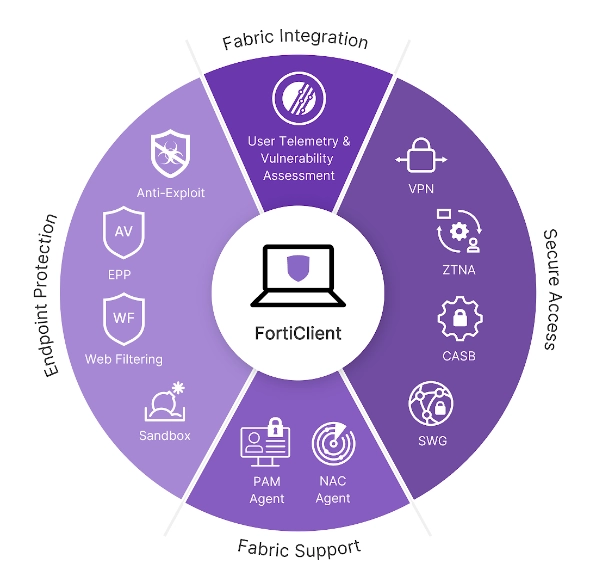
Source: Fortinet3
FortiClient’s approach focuses on providing a ZTNA solution that integrates seamlessly with existing security infrastructures. The product features include:
- Zero trust agent with MFA: It supports ZTNA tunnels, single sign-on (SSO), and device posture checks, incorporating multi-factor authentication (MFA) for enhanced security.
- Central management via EMS or FortiClient Cloud: Admins can remotely deploy and manage endpoint software, ensuring real-time endpoint status and streamlined upgrades.
- Central logging and reporting: Centralized logging through FortiSIEM or other SIEM products simplifies compliance reporting and security analysis.
- Split-tunneling: Supported on ZTNA and VPN tunnels, split-tunneling enhances user experience by routing traffic.
- Web Filtering: Monitors web activities and enforces security policies with extensive category support and consistent enforcement.
Use cases
Endpoint visibility and compliance control: Ensures visibility and compliance across the Security Fabric, integrating endpoint and network security with automation.
Advanced endpoint protection: Utilizes machine learning anti-malware and behavior-based anti-exploit techniques, alongside app firewall and web content filtering.
Sandbox integration: Native integration with FortiSandbox enables the blocking of unknown files and real-time analysis.
3. Zscaler Private Access
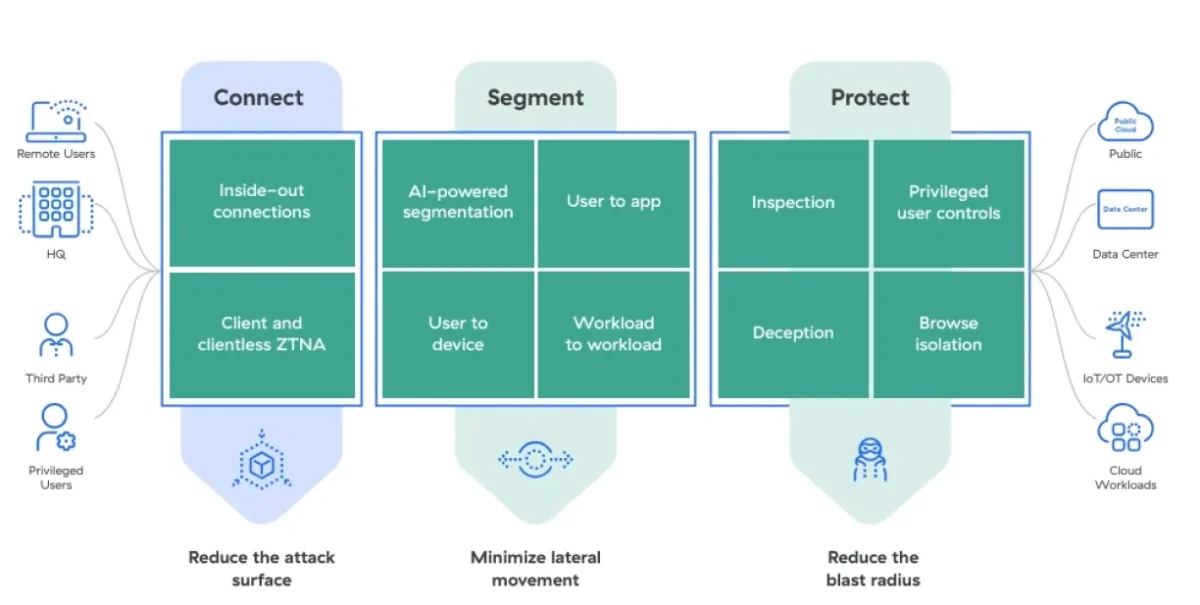
Source: Zscaler4
Zscaler Private Access (ZPA) offers a next-generation zero trust network access (ZTNA) platform. The product offers features such as:
- Least-privileged access: ZPA allows authorized users to connect only to approved resources, enhancing security by making apps invisible and inaccessible to attackers.
- Global edge presence: Offers unmatched security and user experience with 150+ cloud edge locations worldwide, ensuring scalability and performance without on-premises appliances.
- Unified ZTNA Platform: Securely connects users, workloads, and devices to private apps and services, providing comprehensive zero-trust capabilities.
Differentiating feature(s):
- Full inline inspection: Protects applications by identifying and stopping web attacks, preventing data theft with industry-leading DLP measures.
Use cases
Third-party access/VDI alternative: It isolates third-party users and unmanaged devices from the network, enhancing security and reducing management costs.
M&As and divestitures: ZPA accelerates network integration post-merger or divestiture, providing seamless access to private apps without VPNs. It streamlines access while eliminating the need for complex network convergence, saving time and resources.
Secure operator access for OT and IIoT: ZPA enables secure access to operational technology (OT) and industrial internet of things (IIoT) assets from remote locations. It offers clientless remote desktop access, ensuring security without compromising productivity.
Secure workload-to-workload connectivity: ZPA ensures secure communication between workloads across private, hybrid, and multi-cloud environments. It reduces operational complexity and enhances zero trust-based connectivity for workloads.
Zero trust branch connectivity: ZPA securely connects branches, factories, and data centers without VPN complexity, ensuring zero trust access based on business policies. It simplifies branch communications and policy management while enhancing security.
4. Cloudflare SASE Platform
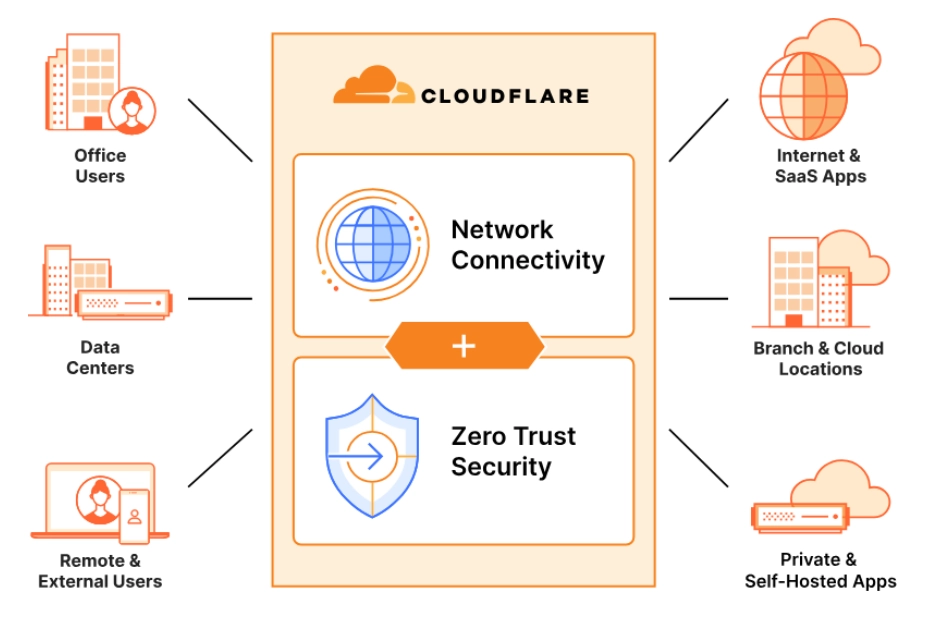
Source: Cloudflare5
Cloudflare’s Secure access service edge (SASE), zero-trust network access solution, is claimed to provide advanced security and connectivity features without the need to oversell the product. Here are some key aspects of Cloudflare’s ZTNA capabilities:
- Secure web gateway (SWG): Secures and inspects corporate internet traffic, protecting against phishing, ransomware, and other online threats.
- Magic WAN: Connects and secures branch offices, headquarters, data centers, cloud VPCs, and SD-WANs using Cloudflare’s network.
- Magic Firewall: Enforces consistent security policies across the WAN, without the need for backhauling traffic or creating choke points.
- Protection against email attacks: Cloudflare’s products include features to protect against email attacks such as phishing, business email compromise (BEC), and email supply chain attacks.
- Data loss prevention (DLP): Inspect HTTP/S traffic for sensitive data and prevent exfiltration with allow or block policies.
Differentiating feature(s):
- Remote browser isolation (RBI): Cloudflare’s RBI feature provides internet threat and data protection by running code away from endpoints, enhancing security without compromising performance.
Use cases
Granular control and data protection: The platform offers granular control over user access and helps in protecting sensitive data through advanced security features like DLP. Organizations can inspect HTTP/S traffic for sensitive data like personally identifiable information (PII) and prevent data exfiltration using allow or block policies.
Phishing and malware protection: Cloudflare’s secure web gateway (SWG) component can be utilized to inspect and secure corporate network traffic, protecting against phishing attacks, malware infections, ransomware, and other internet-borne threats. This helps in maintaining a secure browsing environment for employees and prevents data breaches.
Cloud and SaaS security: Secures access to cloud and SaaS applications, protecting data and controlling user permissions.
Network management. Simplifies the management of distributed networks by connecting and securing multiple locations through a single platform.
5. Forcepoint One
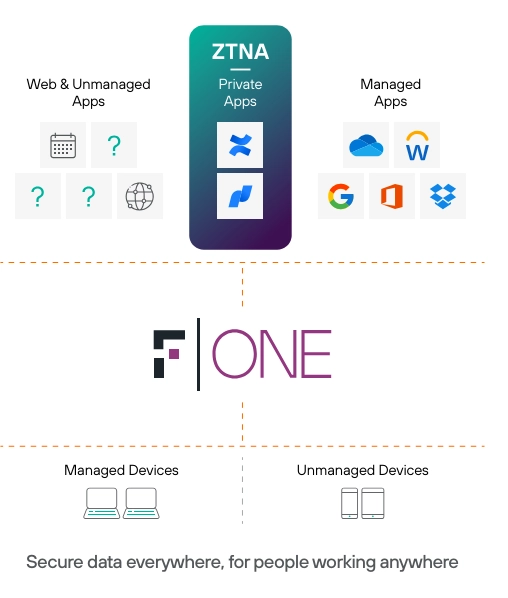
Source: Forcepoint6
Forcepoint ONE integrates Secure access service edge (SASE), ZTNA, CASB, SWG, and other Zero Trust, data security, and network security technologies into a comprehensive all-in-one platform. Key features of Forcepoint One include:
- Data loss prevention: Comprehensive DLP capabilities automatically enforce data protection policies for sensitive information in transit.
- Unified platform: Combines ZTNA, SASE, CASB, SWG, and other security technologies into a single, cloud-native platform for streamlined security management.
Use cases
Bring your own device (BYOD) environments: Provides secure access for employees using personal devices, maintaining strict control over data and applications without requiring software installations on endpoints.
Compliance: Meets compliance requirements with granular access controls and comprehensive activity monitoring, essential for industries with strict data protection regulations.
6. Absolute Secure Access
Absolute Secure Access is designed to deliver a security service edge (SSE) tailored for modern work models, including hybrid and mobile setups. Features of Absolute Secure Access include:
- Resilient Connectivity: Supports a mobile-first approach with robust VPN and Zero Trust Network Access (ZTNA) capabilities. Ensures seamless connectivity across public cloud, private data centers, and on-premises environments, regardless of network type (Wi-Fi, cellular).
- Dynamic Policy Enforcement: Enforces policies at the endpoint, ensuring consistent security measures irrespective of the user’s location or network, and enhancing data protection.
- Proactive Diagnostics: Provides real-time insights into network and device health, facilitating proactive troubleshooting and minimizing downtime.
- Single Platform: Integrates VPN, ZTNA, secure web gateway (SWG), and digital experience monitoring (DEM) functionalities into a unified solution, simplifying management and reducing operational complexity.
Differentiating feature(s):
- AI-Powered Proactive UEBA: Receive early security alerts driven by AI and machine learning, detecting suspicious behavior and anomalies using over 50 advanced detectors—before they escalate into threats.
Use cases
Operational efficiency: Improves IT and helpdesk effectiveness by providing detailed diagnostics and automating troubleshooting processes, thereby reducing response times and operational costs.
Anywhere workforce enablement: Ideal for organizations with remote, mobile, or field workers who require secure, reliable access to critical applications and resources. Ensures productivity by minimizing connectivity issues and optimizing network performance.
7. Twingate
Twingate’s zero trust network access (ZTNA) solution offers a modern approach to securing network access by replacing traditional virtual private networks (VPNs). Key features of Twingate’s solution include:
- Separation of Concerns: Twingate’s architecture ensures that no single component can independently authorize access. Multiple components verify each access request, adding layers of security.
- Four-Component Architecture:
- Controller: Central coordination hub, handling configuration, user authentication delegation, and issuing access control lists (ACLs).
- Client: Installed on user devices, it acts as a proxy for authentication and authorization, managing network requests and secure connections.
- Connector: Registers with the Controller, forwards authorized traffic, and ensures only authenticated users can access designated resources.
- Relay: Facilitates secure data flow between Clients and Connectors.
- Secure Traffic Encryption: Uses certificate-pinned TLS tunnels within the internal network to ensure all data transmissions are encrypted and secure, preventing unauthorized interception.
Use cases
Automated Management: Allows engineers and DevOps teams to manage and automate secure access to both on-premises and cloud infrastructure, streamlining workflows and enhancing security.
Regulatory Adherence: Helps organizations implement the necessary security controls to comply with regulations like CPRA, GDPR, PCI DSS, and SOC 2, ensuring adherence to industry standards.
Policy Enforcement: Organizations can set and enforce access policies based on device characteristics, ensuring only compliant devices can access sensitive resources.
8. Ivanti Neurons
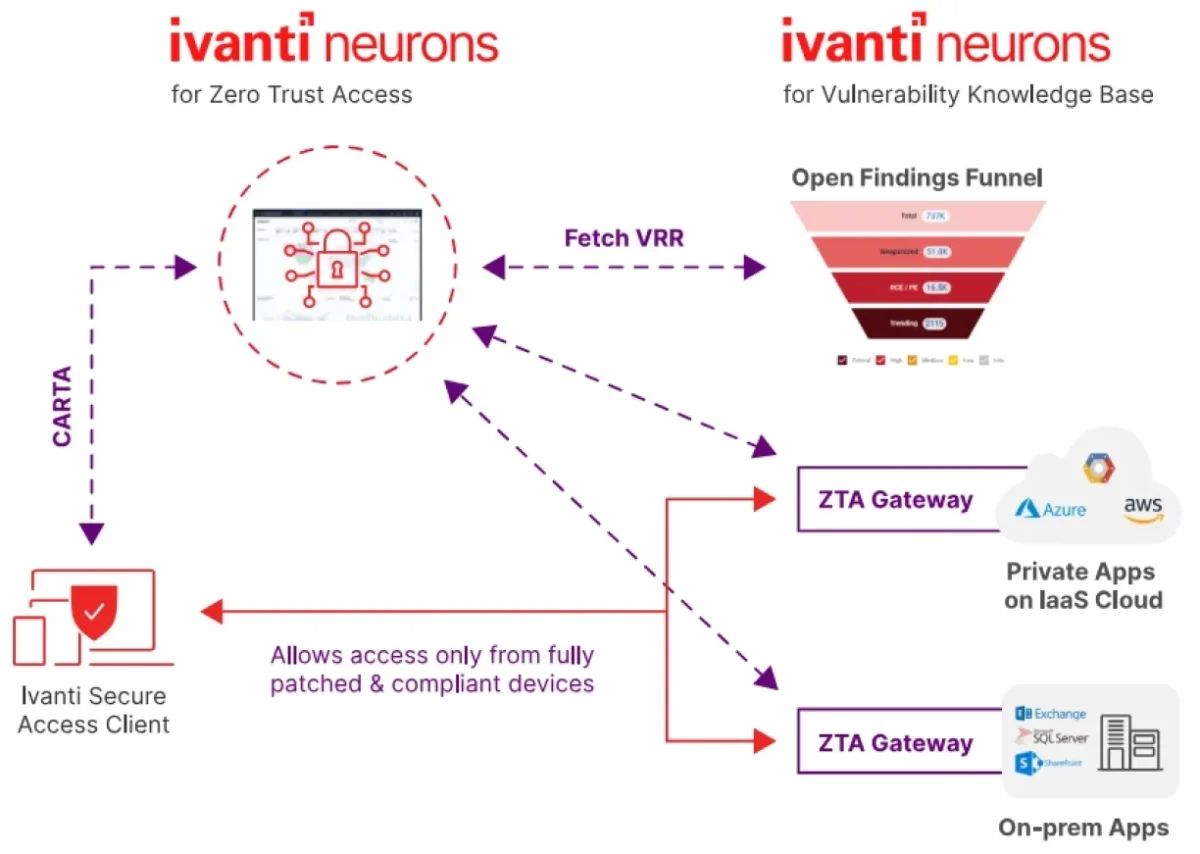
Resource: Invanti7
With Ivanti Neurons for zero trust access, organizations can implement a zero trust access security model, manage application access, and leverage analytics for proactive security measures. Key features of the product include:
- End-to-end access policy: Defines comprehensive access policies for all resources, bridging the gap between remote and on-premises users.
- Single-pane-of-glass visibility: Gain holistic visibility and compliance reporting across users, managed or unmanaged devices, applications, and infrastructure.
- Adaptive SSO: Integrates with SAML 2.0 for single sign-on (SSO) to supported applications, enhancing user experience.
- Intelligent traffic steering: Ensures optimal user experience with automated gateway selection for routing app traffic.
- Endpoint compliance: Authenticates users and devices against policies to minimize malware risks and ensure security.
- Application discovery: Gains insights into application usage and create ZTA security policies seamlessly without disrupting users.
- User behavior analytics: Leverages analytical data for risk reduction, anomaly detection, and optimizing user experience.
- DLP and AV: Prevents data loss and exfiltration by monitoring data communications and safeguarding end-user devices.
Use cases
Application access management: Empowers organizations to implement fine-grained access policies based on user’s identity, device, and location, facilitating efficient access management while maintaining security standards.
Analytics for proactive security: Utilizes advanced analytics for real-time anomaly detection, user and entity behavior analytics (UEBA), and vulnerability risk rating (VRR) insights to identify and respond swiftly to potential threats.
9. Nord Layer ZTNA
NordLayer is a security solution designed to implement zero-trust network access (ZTNA). Key features of Nord Layer ZTNA solution include:
- Identity and context-based access: ZTNA relies on verifying the identity and context of each access request. This involves multiple layers of verification, including identity, device health, and policy compliance before granting access.
- Network segmentation: Segments the network down to the application level (Layer 7), ensuring that each part of the network is protected individually. This minimizes the impact of potential breaches and restricts unauthorized lateral movement. It is an important criteria for PCI DSS certification.
- Compliance: Helps businesses comply with industry standards and regulations, safeguarding sensitive information.
Network segmentation tools allow for control over network segmentation, which is a cornerstone of Zero Trust security. By dividing the network into smaller, manageable segments, these tools help minimize the potential impact of a breach, preventing lateral movement within the network. This ensures that even if an attacker gains access, their ability to move across the network is severely restricted.
Use cases
Control Third-Party Access: Ensures that external partners, contractors, or vendors only access the necessary resources, minimizing their exposure to the broader network.
Regulatory Adherence: Implements detailed access controls, multilayered authentication, and comprehensive logging to meet regulatory requirements and support effective security audits.
Identify & Verify Users: Ensures high reliability in user identity verification through centralized management of certificates, Single Sign-On (SSO), and guest access.
10. Google BeyondCorp Enterprise
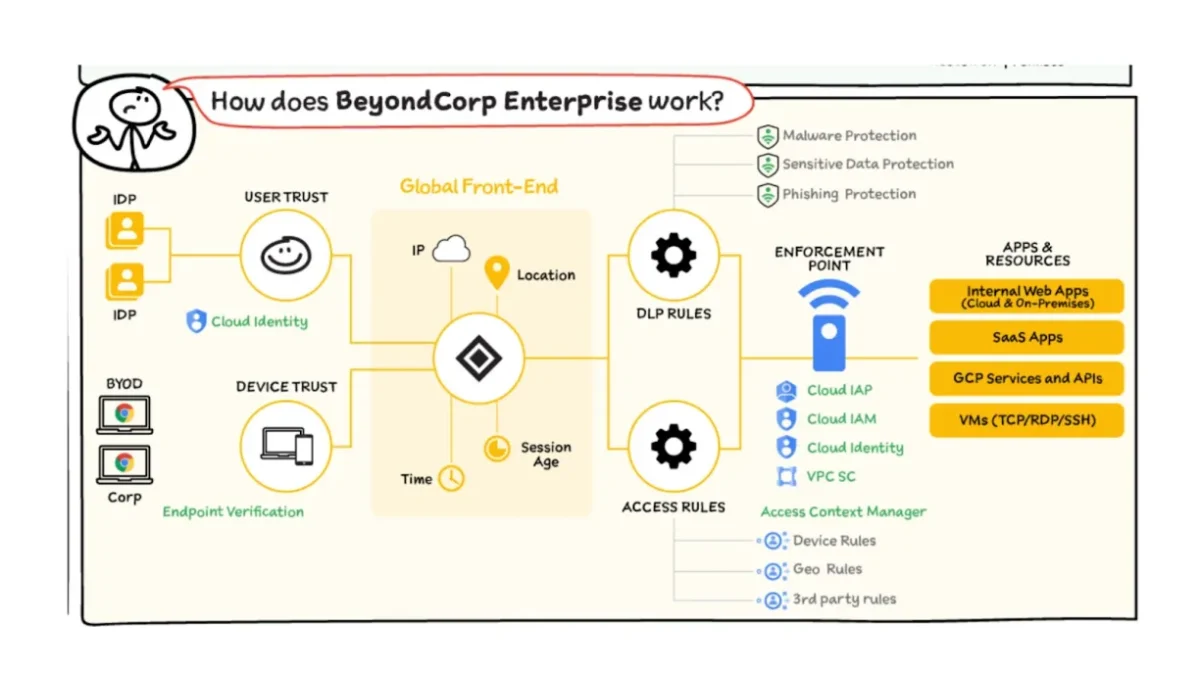
Source: Google Cloud8
Google BeyondCorp Enterprise offers a security solution based on zero trust network access (ZTNA) principles. It provides secure access to corporate services, mitigates data exfiltration risks, and ensures proactive threat detection and response without compromising user experience. Its features include:
- Network-agnostic access: Access to services is not determined by the user’s network location. Whether an employee is on a corporate network, a home network, or a public network, access controls are consistently applied.
- Context-aware access: Access decisions are based on a combination of user identity and the security posture of their device, taking into account factors such as device health, user role, and location.
- Authentication, Authorization, and Encryption: All access requests must be authenticated, authorized, and encrypted to ensure security and compliance.
- Data loss prevention: Prevents data loss and protect sensitive data.
Use cases
Integrated Threat and Data Protection: Offers built-in threat detection and data protection capabilities to safeguard sensitive information against cyber threats.
Third-Party Access: Manages secure access for contractors, partners, and other third parties needing to access company resources.
FAQs
What does ZTNA achieve?
ZTNA helps companies support flexible work without opening up their whole network. It connects each user only to what they need, no matter where they are. This makes it easier to manage access and reduce risk in a remote work setup.
How does ZTNA work?
With ZTNA, access is established after the user has been authenticated to the ZTNA service. The ZTNA service then provisions access to the application on the user’s behalf through a secure, encrypted tunnel. ZTNA solutions create individual user identity- and context-based boundaries around network assets or groups of assets.
Who needs ZTNA solutions?
ZTNA is essential for businesses with distributed workplaces and complex supply chains. It provides protection for various attack surfaces, including personal and corporate devices, on-premises and public cloud applications, and remote and on-site employees. ZTNA ensures that only authorized users and devices gain access to specific resources, reducing the risk of unauthorized access and data breaches.
It also enables productivity through remote and hybrid work models while ensuring secure connections and granular access controls based on identity and context. Additionally, ZTNA verifies the identities of third parties and their devices, preventing unauthorized access and mitigating risks associated with compromised devices and unauthorized users.
What are the differences between software-defined perimeters (SDPs) and ZTNA solutions?
SDP (software-defined perimeter) and ZTNA are security frameworks designed to provide secure access to network resources. While they share similarities, there are key differences.
SDP focuses on creating secure perimeters around individual resources, using authentication, encryption, and dynamic access policies to ensure only authorized users are granted access. ZTNA, however, treats all users requesting access as potentially malicious, requiring rigorous authentication and authorization checks before granting access.
SDP typically secures individual resources like applications or servers, while ZTNA secures an entire network, including all resources, devices, and users. Implementing SDP is more complex and resource-intensive, requiring management of individual perimeters. In contrast, ZTNA is more streamlined, allowing zero trust policies across the entire network via a single platform.
How is ZTNA 2.0 different than ZTNA 1.0?
ZTNA 2.0 improves on ZTNA 1.0 by offering continuous security inspection and trust verification, instead of one-time checks. It enables real least-privileged access at the app and sub-app level, secures all data and apps (including SaaS and legacy apps), and is designed for today’s remote and hybrid work environments. Unlike ZTNA 1.0, it adapts to changing risks and ensures ongoing protection.
Further Reading
- Zero Trust Network Access (ZTNA): Definition & Benefits
- 25+ Network Security Software Based on 10,000+ Reviews
- A Comprehensive Overview of Top 5 ZTNA Open Source Software
If you need further help in finding a vendor or have any questions, feel free to contact us:
External Links
- 1. 35% of workers who can work from home now do this all the time in U.S. | Pew Research Center. Pew Research Center
- 2. Start Building Your Zero Trust Architecture with ZTNA 2.0 - Palo Alto Networks Blog. Palo Alto Networks
- 3. FortiClient Unified Agent for ZTNA, Secure Remote Access and Endpoint Protection | Fortinet.
- 4. Zscaler Private Access. Zscaler. Accessed: 13/June/2024.
- 5. SSE & SASE | Converge Networking and Security.
- 6. Forcepoint ONE Zero Trust Network Access. Forcepoint. Accessed: 11/June/2024.
- 7. Ivanti Neurons for Zero Trust Access [Datasheet].
- 8. Zero Trust and BeyondCorp Google Cloud | Google Cloud Blog. Google Cloud


Comments
Your email address will not be published. All fields are required.