Based on their categories and GitHub stars here are the leading examples of open-source incident response tools that can help you automate the process of detecting and resolving security breaches:
- Incident response tools:
- Snort3: Network-based intrusion detection system (IDS)
- OSSEC: Host-based intrusion detection system (IDS)
- OpenVAS: Vulnerability scanner
- Nmap: Network mapping tool
- Pure incident response tools:
- TheHive: Incident response platform
- Velociraptor: Digital forensics and incident response (DFIR) tool
See the explanation of incident response tools and pure incident response tools.
Incident response tools
| Tool | Category | # of stars on GitHub | # of GitHub contributors |
|---|---|---|---|
| Graylog | SIEM | 7.4k | 100+ |
| Wazuh | SIEM, XDR | 11k | 250+ |
| Azure Sentinel | SIEM, SOAR | 4.6k | 700+ |
| Snort3 | Intrusion detection system (IDS) | 2.6k | 30+ |
| OSSEC | Intrusion detection system (IDS) | 4.3k | 100+ |
| Ntop | NetFlow analyzer | 6.3k | 100+ |
| NfSen | NetFlow analyzer | 0.2k | 10 |
| OpenVAS | Vulnerability scanner | 3.4k | 50 |
| amass | Network mapping | 12k | 70 |
| Nmap | Network mapping | 10.2k | 8 |
| n8n | SOAR, workflow automation | 48.6k | 400+ |
See the explanation of categories.
Pure incident response tools
| Tool | Category | # of stars on GitHub | # of GitHub contributers |
|---|---|---|---|
| TheHive | Incident response platform | 3.4k | 10+ |
| IRIS | Incident response platform | 1.1k | 30+ |
FIR | Incident response platform | 1.7k | 20+ |
| velociraptor | Digital forensics and incident response (DFIR) | 3k | 100+ |
| GRR Rapid Response | Digital forensics and incident response (DFIR) | 4.8k | 40+ |
Tool selection criteria:
- Number of reviews: 200+ GitHub stars.
- Update release: At least one update was released last week.
Examples of incident response tools
Graylog
Graylog (SIEM) system provides a log analytics platform for collecting, analyzing, and alerting machine-generated data. It is specifically built to collect data from various sources, allowing you to centralize and monitor your log data. Graylog can perform a variety of cyber security tasks, including:
- Data aggregation
- Correlation and security event tracking
- Forensic analysis
- Incident detection and response
- Real-time event response and alerting console
- User and entity behavior analytics (UEBA)
- IT compliance management
Wazuh
Wazuh is an SIEM and XDR solution for endpoint and cloud workload protection. It includes an endpoint security agent deployed on the monitored systems and a management server that collects and analyzes data collected.
Wazuh’s capabilities:
- Intrusion detection
- Log data analysis
- File integrity monitoring
- Cloud and container security
Wazuh can integrate with the Elastic Stack, offering a search engine tool to assist users in navigating their security alerts.
Azure Sentinel
Azure Sentinel, formerly Microsoft Sentinel, is a SIEM and SOAR solution that operates in the Azure cloud. Azure Sentinel may be used for security event analysis in cloud and on-premises systems. Common usage scenarios include:
- Visualization of log data
- Anomaly detection and alerting
- Investigation of security incidents.
- Threat hunting
- Automated responses to security incidents
Snort3
Snort3 is a network-based intrusion detection and prevention system (IDS/IPS) that monitors network traffic in real-time and logs data packets. It identifies potentially malicious activity using a rule-based language that combines anomaly detection, protocol analysis, and signature inspection techniques.
Snort3 allows network administrators to detect denial-of-service (DoS) and distributed DoS (DDoS) assaults, Common Gateway Interface (CGI) attacks, and stealth port scans.
Key capabilities:
- Real-time traffic monitoring
- Packet logging
- TCP/IP stack protocol analysis
- Operating System (OS) fingerprinting
OSSEC
OSSEC is a host-based intrusion detection platform that monitors and manages your systems. The solution offers three versions:
- Free: The free version includes 100s of open-source security rules.
- OSSEC+: This version starts at $55 per endpoint per year and offers hundreds of extra rules, threat intelligence integration, machine learning capabilities, and add-ons.
- Atomic OSSEC: This version combines thousands of additional complex OSSEC rules with ModSecurity web application firewall rules into a single extended detection and response (XDR) system.
ntop
NTOP is much more of a general network usage analyzer with a NetFlow plugin that gives network visibility by gathering traffic information from NetFlow exporters, firewall logs, and intrusion detection systems. ntop can:
- Sort network traffic based on several features, including IP address, port, and Layer-7 (L7) application protocols.
- Show real-time network traffic and active hosts.
- Monitor and report on network and application latencies, Round Trip Time (RTT), TCP statistics (out-of-order packets, packet loss), and bytes and packets transmitted.
- Discover Layer-7 application protocols (Facebook, YouTube, BitTorrent, etc) using ntop Deep Packet Inspection.
NfSen
NFSEN collects NetFlow flows using the nfdump tools. NfSen allows you to:
- Display netflow data as flows, packets, and bytes.
- Navigate the netflow data.
- Process the netflow data within the time constraints.
- Create your plugins to process NetFlow data at regular intervals.
OpenVAS
OpenVAS is a vulnerability scanner developed by Greenbone Networks. Provides a set of tools for vulnerability management, offering features like customizable scanning policies, detailed reporting, and support for multiple protocols.
Amass
The OWASP Amass Project is developed in ‘go coding language’, which is much quicker than Python, and it uses open-source information-collecting techniques to map network attack surfaces and find external assets.
The amass engine also supports scripting. Amass allows you to undertake in-depth DNS, Autonomous System Number (ASN), and other assets controlled by a company.
Nmap
Nmap is an open-source Linux command-line utility that scans a network for IP addresses and ports and detects installed applications.
Nmap enables network administrators to discover which devices are running on their network, identify open ports and services, and detect vulnerabilities. It offers several features that make it invaluable for penetration testing, network monitoring, and vulnerability scanning:
- Device discovery: Nmap can detect devices across single or multiple networks, including servers, routers, switches, and mobile devices.
- Service identification: It can identify services running on a system (e.g., web servers, DNS servers).
- Operating system detection: Nmap can provide detailed information about the OS running on a device, including OS versions.
N8n
n8n is a workflow automation application that uses a fair-code distribution paradigm. This means that the source code is open for review, and users can also self-host the platform.
Key points to consider:
- Connectors: n8n offers over 400 connectors including Google Sheets, Slack, MySQL, and HubSpot.
- AI capabilities: N8n’s AI capabilities enable users to create autonomous, multi-step agents that interact with their data and tools. This includes evaluating data with AI models and improving workflows through intelligent decision-making.
- Customizability: n8n provides an environment where users can code in JavaScript or Python, utilize external libraries, and import cURL requests.
- Self-hosting option: For enterprises worried about data privacy and security, n8n provides self-hosting options.
Examples of pure incident management and response tools
TheHive
TheHive Project is a publicly available security incident response platform that helps security analysts working in SOCs, and CSIRTs, track, investigate, and respond to recognized security events.
TheHive Project has three basic functions:
- Collaborate: Multiple analysts from the same organization can work on the same case simultaneously.
- Elaborate: Each case’s details can be divided into associated tasks generated from scratch or using a template engine.
- Act: Analysts can add tags to their cases to identify IOCs.
IRIS
IRIS is a collaborative platform for incident response analysts that allows them to exchange technical investigation results. Some features include:
- Alerts: IRIS can receive alerts from SIEM and other sources.
- Integrations: IRIS can be extended with customized modules. By default, it comes with VirusTotal, malware information sharing platform (MISP), WebHooks, and IntelOwl.
FIR
FIR (Fast Incident Response) is a cybersecurity incident management software built for tracking, and reporting cybersecurity incidents, it is mostly used by (CSIRTs, CERTs, SOCs, etc.).
Velociraptor
Velociraptor is an endpoint monitoring, digital forensics, and cyber response tool.
Key features:
- Artifact collection: Velociraptor can collect various artifacts (e.g. logs) from endpoints, such as files, registry information, and network data.
- Evidence analysis: Velociraptor’s evidence analysis capabilities help investigators detect potential security threats.
- Incident response automation: Velociraptor uses pre-configured workflows to detect, investigate automatically, and remediate incidents.
- Integrations: SIEMs, EDRs, and threat intelligence platforms.
GRR Rapid Response
GRR Rapid Response developed by Google is a platform that remotely gathers and analyzes data from compromised computers.
GRR’s key roles in incident response are:
- Data collection
- Live memory analysis:
- Remote command execution:
- Forensic artifacts analysis of files, data stored in the Windows Registry network traffic, system logs, cookies, etc.
Types of incident management tools
Incident response tools are primarily administrative and focus on helping security teams ensure that incidents are tracked, escalated, and managed.
Pure incident response solutions are more actionable, enabling detailed investigation, remediation, and real-time response to security incidents.
Here’s a breakdown of the differences:
1. Incident management and response tools
Scope:
- Incident management tools focus more on the administrative and operational side of incident response.
- They are primarily used for organizing, managing, and tracking incidents, rather than resolving or investigating them in depth.
- They focus on offering visibility and coordination across teams involved in the response process.
Some of these systems provide additional automation and orchestration features, such as SOAR capabilities, which enable automated responses to specific issues.
Key functions:
- Incident tracking and documentation:
- Alerting and escalation
- Collaboration and case management
- Automation of workflows, SOAR
2. Pure incident response tools
Scope:
- Pure incident response solutions provide a hands-on focus on managing and mitigating attacks in real-time.
- They are more tactical and focused on active response, and forensic investigations to enable SecOps to observe how the breach occurred.
- These solutions are incident-specific, focusing on analysis, and recovery during and after an attack.
Key functions:
- Incident tracking and documentation
- Root cause analysis and remediation
- Threat intelligence integration
- Evidence documentation
Explanation for categories
Incident response tools’ categories:
- Security information and event management (SIEM) systems collect and analyze log data from several sources to provide real-time monitoring and incident response.
- Extended detection and response (XDR) tools enhance SIEM with detection and response across multiple security layers.
- Security orchestration, automation, and response (SOAR) software automates security workflows to improve response time and reduce manual effort.
- Intrusion detection systems (IDS) detect suspicious activities but do not actively respond.
- NetFlow analyzers provide insights into network traffic for anomaly detection.
- Vulnerability scanners are automated tools that scan web applications to search for security vulnerabilities.
- Network mapping tools help visualize and understand network infrastructures.
- Antimalware software offers endpoint protection against malicious software.
Pure incident response tools’ categories:
- Threat intelligence software read raw data on existing and developing threats from various sources, providing context for ongoing incidents.
- Incident response platforms (IRPs) help security teams manage and track incidents as they are discovered, leveraging threat intelligence and responding to detected threats using workflows and collaboration tools.
- Digital forensics and incident response (DFIR) tools are often used in the post-incident phase to conduct in-depth investigations, gather evidence, and determine how an attack was carried out.
Other incident response technologies
- Attack surface management (ASM) solutions automate the continuous detection, analysis, remediation, and monitoring of vulnerabilities. ASM can identify previously unknown network assets and map their relationships.
- Endpoint detection and response (EDR) technologies are designed to automatically defend end users, endpoints, and organizational IT assets from cyber threats that bypass other standard endpoint security measures.
- User and entity behavior analytics (UEBA) is a cybersecurity solution that employs algorithms and machine learning to detect anomalies in users, routers, servers, and endpoint trends.
What is an incident response tool?
Incident response tools are software applications or platforms that help security teams detect, manage, and resolve cybersecurity incidents.
To be eligible for inclusion in the incident response category, a solution needs to:
- Automate or guide users through the remediation procedure.
- Monitor for irregularities in an IT system.
- Notify users of unusual activities.
- Automate or guide users through the remediation procedure.
- Collect incident data for reporting.
What to look for when choosing an open-source incident response tool?
Check the tool’s core functionality and use case fit: Determine the precise use cases and criteria for your incident response process. For example:
- What types of incidents do you respond to? (e.g., malware, phishing, DDoS, insider threats)
- Do you need real-time response or post-incident analysis?
- Does the tool require integration with other security systems, such as threat intelligence tools?
Then, decide if you require an administrative and operational solution that handles, for example, SOAR workflow automation (e.g. Azure Sentinel), an incident-specific one that focuses on forensics and root cause investigation (e.g. velociraptor).
Customization and flexibility: Evaluate tools based on their customization options, you may require a tool that provides:
- Configurable workflows: The ability to customize workflows and processes to meet your organization’s specific incident response requirements.
- Broad integration options with SIEMs, threat intelligence platforms, and ticketing systems).
- Well-documented APIs enable you to combine the product with existing systems and automate specific activities.
Check the tool’s popularity: The amount of GitHub contributors and community members who react to user inquiries indicates the popularity of open-source technologies. The greater the community, the more support your organization is likely to receive.
Compare closed-source or paid solutions: Open-source solutions typically include restricted or add-on functionality; however, deploying a more personalized solution that provides more features (for example, the enterprise version adds: clustering, agent management, compliance reporting, vulnerability management) may be more efficient for your company.
Here’s a list of closed-source incident response tools, with some tools (e.g. Cynet) offering open-source options.
Data breach incident response plan: 5-step methodology
1. Preparation
Establish a solid foundation for incident response with policies, procedures, and a response team.
Key components:
- Incident response planning: Create comprehensive incident response policies outlining the scope, roles, responsibilities, and protocols.
- Incident response team: Form a team with representatives from IT, security, legal, HR, communications, and other relevant departments.
- Tools and resources: Ensure the availability of necessary tools and resources such as SIEM systems, forensic tools, and communication platforms.
- Communication plan: Develop internal and external communication plans to ensure clear and effective communication during an incident.
2. Identification & reporting
- Detect and confirm the occurrence of a security incident.
Key components:
- Monitoring systems: Implement continuous monitoring systems to detect unusual activities and potential security incidents.
- Incident reporting: Establish clear reporting channels for suspected incidents, ensuring timely notification to the IRT.
- Documentation: Keep detailed records of detection activities, including logs, alerts, and initial findings.
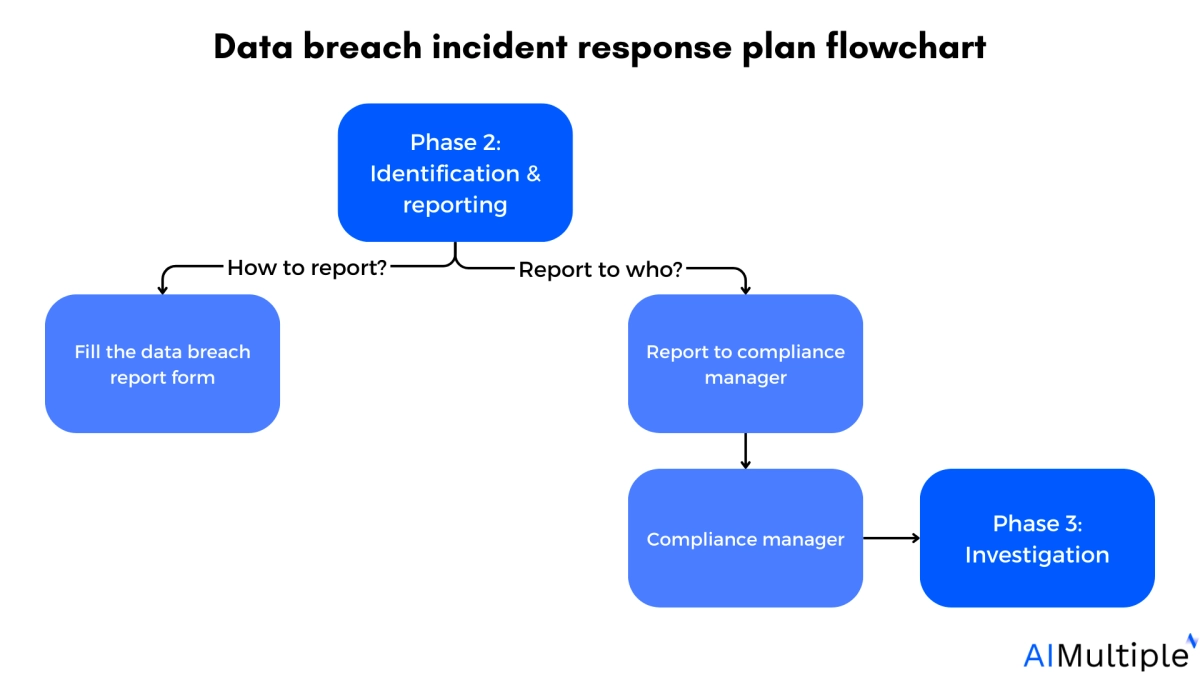
If any employee notices an incident or potential data breach, they need to report it immediately.
To report a potential incident, employees should:
- a) Fill out the data breach report.
- b) Send a copy to their area manager via email or in person.
- c) Ensure the incident is private excluding disclosures required by this plan.
After receiving an incident report, the area manager needs to immediately:
- a) Notify the manager of compliance with the incident and provide a copy of the completed report.
- b) Ensure the incident is private excluding for disclosures required by the plan.
3. Assessment
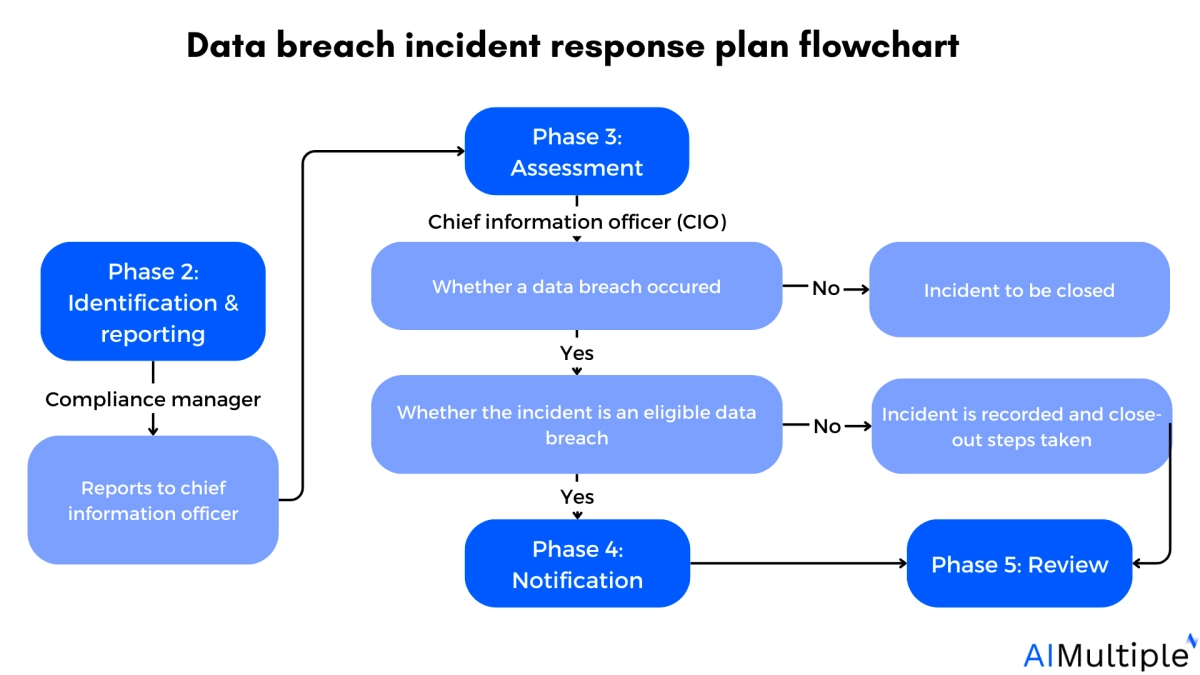
3.1 Decide whether the incident is a data breach
The chief information officer will review the initial findings and decide whether to establish the data breach incident response team and:
- a) Decide whether the incident is a data breach, if not the incident will not be addressed to the response team.
- b) Identifies a data breach and assesses the risk of substantial harm using the company’s risk matrix assessment system.
Figure: Risk matrix assessment system
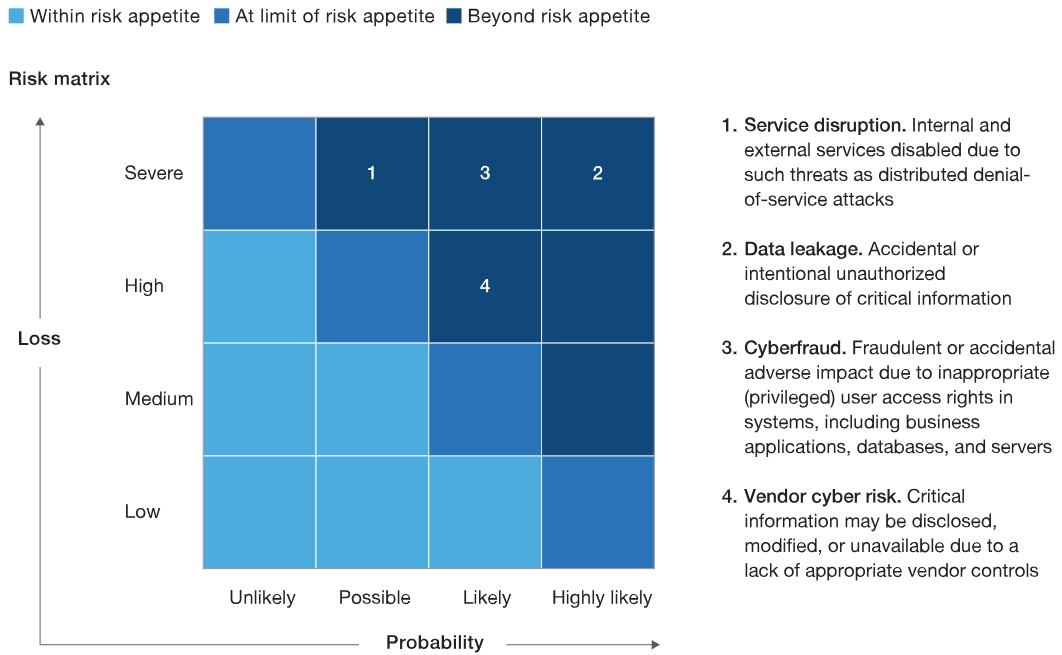
Source: McKinsey & Company1
3.2 Steps for assessing a data breach
If 3.1 b) is met, the CIO must immediately call a meeting of the data breach incident response team for the assessment. When doing the assessment, the following factors must be examined:
- The form of personal information affected.
- The context of the impacted information and the breach.
- The source and scope of the breach.
- The risk of individuals getting significant harm.
4. Notification
In phase 3, if the CIO identifies an eligible data breach, the affected company must notify the Department of State’s Privacy Office and the individuals impacted.
The notification must include the company’s:
- Identity and contact details.
- A description of the potential data breach.
- The types of private data affected.
- Company’s suggestion to secure stolen credentials.
5. Review
After addressing the immediate implications of a data breach, the CIO conducts a post-breach analysis and assessment. To conduct the review, the CIO should seek unofficial feedback from the data breach incident response team and other business units as needed.
The following are some examples of steps that could be taken in specific scenarios:
Example 1: If an employee committed a data breach the affected company can:
- Increase network audits or IoT monitoring to avoid data breaches from occurring again.
- Modify network security policy management rules to prevent recurrent data breaches.
- Implement new controls and limitations on role-based access control (RBAC) and mandatory access control.
Read more: Network security policy management solutions (NSPM).
Example 2: If a third party caused the data breach, the affected company can:
- Improve its IT security measures.
- Implement additional security measures to secure personal data (e.g. data encryption).
- Provide staff or contractors with instructions to prevent future breaches.
Read more: Third-party cyber risk management.
Further reading
- Role-based access control (RBAC)
- Network Segmentation: 6 Benefits & 8 Best Practices
- 80+ Network Security Statistics
- Network Security Policy Management Solutions (NSPM)
- Top 10 SDP Software Based on 4,000+ Reviews
- Top 10 Network Security Audit Tools Based on 4,000 Reviews
External Links
- 1. Reporting with a cyber risk dashboard | McKinsey. McKinsey & Company


Comments
Your email address will not be published. All fields are required.