Data classification software helps organizations locate sensitive data, such as personally identifiable information (PII), payment industry information (PCI), and other critical business data, stored across multiple enterprise systems, including databases and applications, as well as on user endpoints.
Data classification tools can be obtained as standalone solutions or as integrated components within data loss prevention (DLP) software and cloud data security software.
To help data-driven companies make informed decisions, we selected the top data classification tools designed to identify, categorize, and manage sensitive information effectively:
Administrative features
| Software | eDiscovery | Deployment |
|---|---|---|
✅ | On-prem & cloud |
|
✅ | On-prem & cloud |
|
Netwrix Auditor | ❌ | On-prem & cloud |
FileCloud Data Classification Software | ✅ | On-prem & cloud |
Safetica Pro | ❌ | On-prem & cloud |
Symantec Data Loss Prevention | ✅ | On-prem & cloud |
Collibra | ❌ | On-prem & cloud |
Satori | ❌ | On-prem & cloud |
Varonis | ✅ | Cloud |
Sensitive Data Finder by Spirion | ❌ | On-prem & cloud |
Microsoft Purview Information Protection | ✅ | Cloud |
- eDiscovery: A process that securely stores log details of electronic data, enabling organizations to comply with legal and regulatory requirements.
- Deployment: The process of installing software either on a company’s hardware infrastructure (on-premises) or on a cloud platform
Data classification features
| Software | Smart content classification | Custom data tagging |
|---|---|---|
✅ | ✅ |
|
❌ | ❌ |
|
Netwrix Auditor | ✅ | ✅ |
FileCloud Data Classification Software | ✅ | ✅ |
Safetica Pro | ❌ | ✅ |
Symantec Data Loss Prevention | ❌ | ❌ |
Collibra | ✅ | ❌ |
Satori | ❌ | ✅ |
Varonis | ✅ | ✅ |
Sensitive Data Finder by Spirion | ✅ | ✅ |
Microsoft Purview Information Protection | ✅ | ✅ |
- Smart content classification: Automated classification process of sensitive data through algorithms.
- Custom data tagging: Custom, granular labeling policies to fit your organization’s unique data protection and privacy requirements.
Data protection features
| Software | Data masking | MFA |
|---|---|---|
❌ | ✅ |
|
❌ | ✅ |
|
Netwrix Auditor | ❌ | ✅ |
FileCloud Data Classification Software | ❌ | 2 factor-authentication |
Safetica Pro | ✅ | ✅ |
Symantec Data Loss Prevention | ✅ | ✅ |
Collibra | ✅ | JSON token authentication/SSO with LADP |
Satori | Dynamic data masking | ✅ |
Varonis | ✅ | ✅ |
Sensitive Data Finder by Spirion | ✅ | ✅ |
Microsoft Purview Information Protection | ❌ | Microsoft Entra |
- Data masking: A technique of changing sensitive data so that it has little or no value to unauthorized intruders while remaining applicable to software or authorized individuals.
- MFA (multi-factor authentication): A multi-step account login process that requires users to enter more information than just a password.
Disclaimer: Insights come from our experience with these solutions as well as other users’ experiences shared in Capterra 1 , Gartner 2 , G23 , and TrustRadius4 .
Sentra
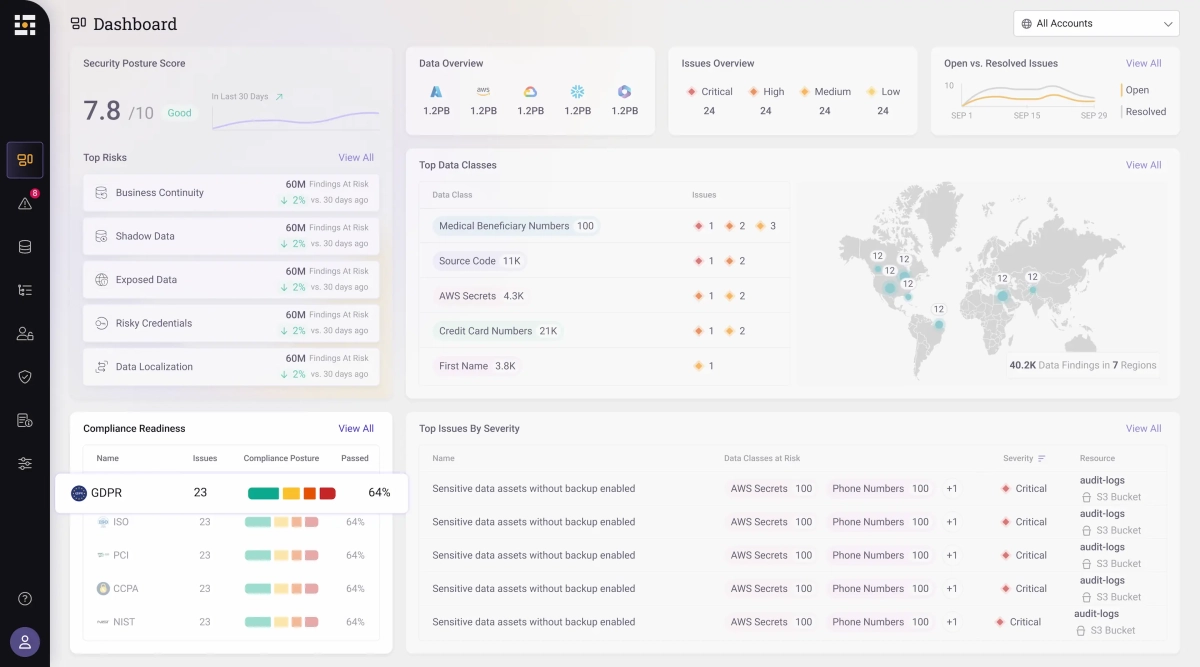
Sentra is a data security posture management (DSPM) platform with data detection and response (DDR) capabilities.
Sentra builds an organized catalog of your sensitive data assets. It detects all sensitive data, both structured and unstructured, such as PII, PCI, and PHI, based on sensitivity (e.g., high, low) or category (e.g., financial, credentials, healthcare).
Sentra is designed to manage petabyte-scale data operations and provides extensive coverage across major cloud environments. It is a suitable solution for enterprises dealing with large volumes of sensitive data.
Pros
- With 200+ classifiers and 20 pre-built or customizable integrations, companies can effectively categorize and monitor sensitive data.
- Effectively identifies unmonitored shadow data across multiple platforms.
- Extensive support across IaaS and DBaaS environments:
- Azure/Microsoft 365: Comprehensive support for Azure, OneDrive, SharePoint, Office Online, and Teams.
- AWS: Includes S3, DynamoDB, SQL Server, PostgreSQL, Redis, and more.
- GCP: Covers Google Cloud Storage, BigQuery, Cloud Spanner, and Google Workspace.
Cons
- The AI chatbot assistant provides inaccurate results.
Choose Sentra to secure and classify your cloud data.
Endpoint Protector by CoSoSys
Endpoint Protector by CoSoSys, now acquired by Netwrix, offers comprehensive data loss prevention (DLP) and endpoint security solutions for businesses.
Endpoint Protector specializes in modules such as USB device control, content-aware protection, e-discovery, and encryption. It is compatible with Windows, macOS, and Linux.
Note that the company is based in Romania with a small team, which might influence support availability and responsiveness due to time zone differences.
Pros
- The e-discovery module is practical, easy to implement, and user-friendly
- Data classification effectively identifies sensitive data and takes actions such as blocking, notifying, or allowing based on predefined rules.
- Administrators can define sensitive data using custom or preset rules through the eDiscovery menu.
See our DLP review for more on Endpoint Protector’s data classification capabilities.
Cons
- No data masking.
- No database fingerprint audit.
- Sometimes, the modules crash, but customer support helps quickly.
Choose Endpoint Protector for a DLP solution with one of the most effective data classification capabilities, as determined by our tests.
FileCloud Data Classification Software
FileCloud provides enterprise file sharing, sync, and collaboration solutions. The platform allows businesses to securely store, access, and share files both within the organization and with external partners or clients.
FileCloud prioritizes data privacy and security, offering features such as end-to-end encryption, granular access controls, and compliance with regulations like GDPR and HIPAA.
Pros
- Robust security features that comply with cybersecurity standards, including ITAR compliance for sensitive data.
- Comprehensive wiki and documentation.
- Supports remote work environments with seamless file sync between cloud and local storage.
Cons
- Lack of flexibility in licensing, as multiple licenses cannot coexist in the same tenant/domain.
- Add-ins and extensions are functional but not fully optimized.
Safetica Pro
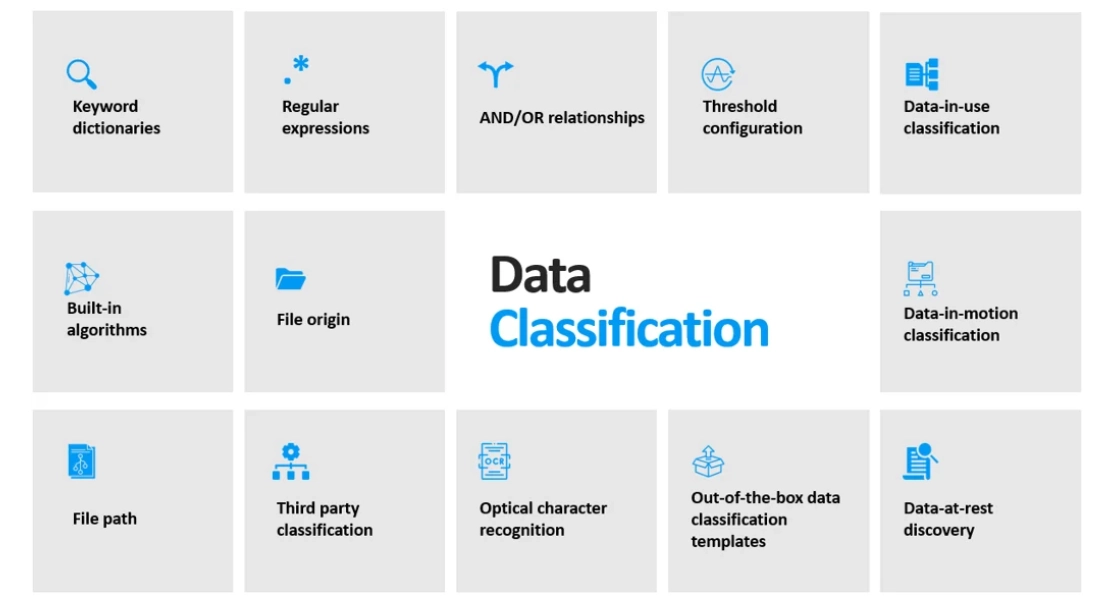
Safetica is a data loss prevention (DLP) and insider risk management (IRM) solution that prevents data breaches and defends businesses against insider threats. It is ideal for both small and large enterprises.
Safetica unified categorization uses content analysis and context awareness to detect sensitive information.
It enables you to identify sensitive files based on sensitive content, origin, file type, and even pre-existing third-party data classification.
Safetica’s unified classification classifies:
- Data in use: Refers to actively working with files, such as opening and editing them in various applications.
- Data in motion involves the transfer of files, whether through uploading, sending emails, or sharing across different platforms.
- Data at rest: Safetica scans devices to identify sensitive data that remains stored but has not been accessed or used for an extended period.
Pros
- Comes with ready-to-use data classification categories (e.g., personal or financial data), enabling instant detection and monitoring of sensitive file operations.
- Allows detailed rule creation, combining specific elements and setting thresholds for occurrences, ensuring precise data management.
- Supports optical character recognition (OCR) to classify and detect sensitive information embedded in scanned documents or images.
Cons
- The Linux support is inefficient.
- Policy deployment is not flexible.
- Its use on Mac-supported devices is problematic.
- Its cloud options are limited in comparison to its on-premise options.
Automation and AI help with security
Figure 1. Data breach costs in USD millions
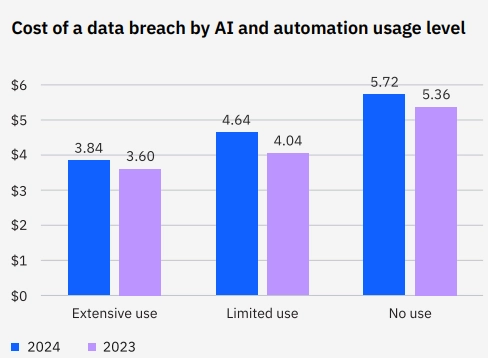
Source: IBM
The most recent IBM report, Cost of a Data Breach 2024, indicates that companies that automate security controls suffer less damage than those that don’t.
How does AI enable data classification?
Data classification can be fused with AI for better results. AI helps the data classification process by continuously analyzing historical data patterns and projecting improved classification actions.
Read more: AI data classification.
Figure 2. AI data classification by schema
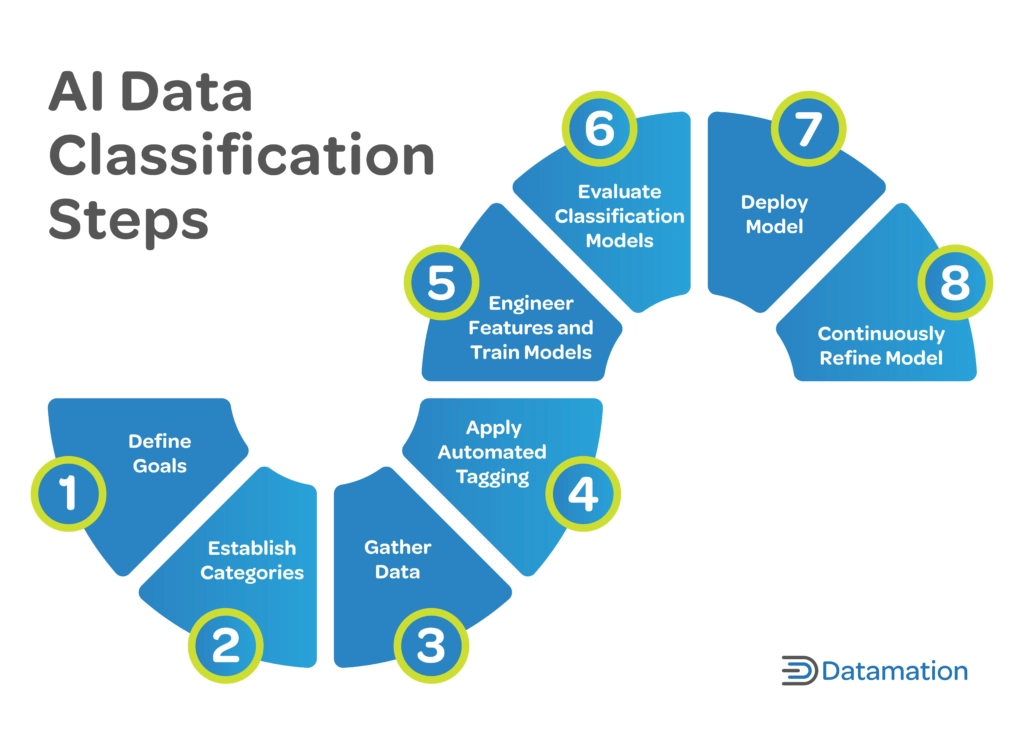
Source: Datamation
Types of data classification
Data classification can be made based on four aspects, as follows5
1. User-based classification
Users carry out manual data classification. Due to its reliance on manual categorization, lack of analysis, and dynamic nature, this type of data classification is prone to errors.
Figure 3. Key findings in data classification utilization

Source: Gartner
2. Context-based classification
Data is categorized according to its context or intended use. For instance, it can be classified as financial, research, customer, or intellectual property data. Other factors considered for data classification include file type and location.
3. Content-based classification
Content-based data classification, also known as content-aware data classification, involves analyzing the actual content of data to determine its classification.
Instead of relying solely on metadata (data about data) or predefined labels, content-based classification uses algorithms and techniques to scan the contents of files or data streams to identify sensitive or valuable information.
Here are common data rules based on content classification:
RegEx (regular expression) based data rule: Searches for the pattern of characters that are defined by regex rules.
Figure 4. Regular expression search through the text

Source: Google
Exact data match (EDM)/ keyword evidence-based data rule: Looks for the precise match of the keyword or combination of keywords prompted.
Figure 5. Exact data match classification
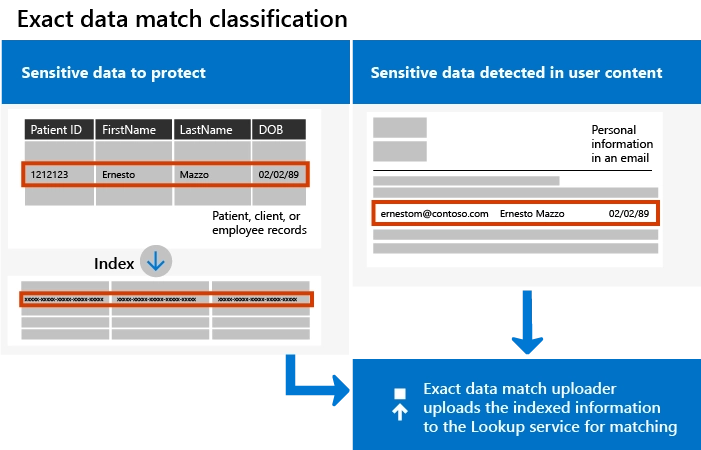
Source: Microsoft Learn
4. Sensitivity-based classification
Data can be classified into four different sensitivity levels:
1. Restricted: Data labeled as “restricted” is of the utmost sensitivity and requires the highest level of protection. This includes information that, if compromised, could cause severe damage to the organization, such as trade secrets or sensitive personal information.
2. Confidential: Data labeled as “confidential” is sensitive and requires protection from unauthorized access or disclosure. This category includes information that, if exposed, could harm the organization’s reputation, competitiveness, or compliance with regulations.
Examples may include financial records, customer data, or proprietary business strategies.
3. Internal: Data labeled as “internal” is restricted to authorized personnel within the organization. While it may not be classified as highly sensitive, it is intended for internal use and should not be shared externally without proper authorization.
Examples include internal documents, memos, or reports.
4. Public: Data labeled “public” is intended for unrestricted access and can be freely shared with anyone, both inside and outside the organization. This category typically includes information that poses minimal risk if disclosed, such as marketing materials or public announcements.
Common features of data classification software
- Automated and continuous content scanning for data discovery: Scans of data at rest or data in transit for sensitivity.
- Sensitive data compliance: Ensures compliance with regulatory requirements involving sensitive data such as personal information (PI) and personal health information (PHI).
- Audit trail: Monitors and logs agent activity.
- Access control: Administers access permissions to data based on user roles or designated rules.
- Data encryption: Encrypting data at rest, data in transit, or both.
- API/Integrations: Enables integration with APIs and Active Directory (AD).
FAQ
What role does data discovery play in data classification?
Data discovery plays a significant role in data classification by helping to understand the underlying structure and characteristics of the data, identifying relevant features for classification, and uncovering patterns or relationships that can inform the classification process.
Further reading
- Top 10 DSPM Vendors in 2024
- DLP Review: Benchmark Testing of 4 DLP Products
- Top 5 NinjaOne Alternatives
- Top 5 Endpoint Management Software
External Links
- 1. Capterra: Find The Right Software and Services. Capterra
- 2. Gartner | Delivering Actionable, Objective Insight to Executives and Their Teams.
- 3. Bewertungen von Geschäftssoftware und -diensten | G2. G2
- 4. TrustRadius: Software Reviews, Software Comparisons and More. TrustRadius
- 5. 5 Common Data Classification Types | Digital Guardian.

Comments
Your email address will not be published. All fields are required.