Network security statistics show that almost 2/3 of companies have 1,000+ high-value files accessible to each employee. Role-based access control (RBAC) systems (i.e. open source RBAC tools) can help organizations administer access controls to:
- assign employee roles based on job duties,
- and ensure that roles & permissions are only issued to the appropriate employees.
Discover 6 real-life RBAC examples; their challenges, solutions, and benefits:
6 Real-life RBAC Examples
1. Dresdner Bank
A major European bank with 368 different job functions and 1,300 roles.
Challenge — maintaining manual employee access privileges: Each employee’s access privileges were manually handled at the application level.
The increased use of internal apps led to significant administrative overheads. Maintaining several application-level privacy files for each user was inefficient and did not align with the overall security policy structure.
Solutions and outcome: The bank has changed its security system’s structure, administration, and control concepts by implementing an RBAC system into its environment. The following outcomes have been achieved by the bank:
- Specific employee and role grouping: Before implementing RBAC employees may only be classified based on their role, hierarchy, and organizational unit. With RBAC employees could be assigned group-specific access permissions based on different factors (e.g. demographics, department).
- Inheritance structure: The bank previously did not have any role inheritance structure. This means that the finance manager job title did not inherit ownership of other closely related job titles such as accounting specialist or bookkeeping assistant manager.
RBAC enabled the bank to access rights inherited through a role hierarchy, enabling fine-grained access control. When the finance manager needed to edit the monthly accounting notes he had to ask the accounting specialist before RBAC implementation, however, now the finance manager may access the monthly accounting notes since his job title inherits the accounting specialist role.1
Read more: Network security policy management, network security use cases.
2. Interfaith Medical Center
A U.S.-based multi-site community educational healthcare organization with 50,659 employees and 1,459 branches worldwide.
Challenge — maintaining HIPAA compliance: HIPAA required to set role-based internal controls for employees to protect electronic healthcare patient data against inappropriate use.
For example, Interfaith Medical Center administrators had to manually set a database configuration so that only authorized employees (such as medical coders or healthcare managers) had access to patient data.
Solutions and outcome: IT administrators at Interfaith Medical Center used bulk management capabilities to create, remove, and edit numerous Active Directory accounts to set specific user permissions in a single operation.
- Centralized access management: Administrators ensured that all network access is through a login that is unique to the employee and not shared.
- Automated RBAC management: The company claimed that after the bulk role-based access control implementation they can confidently manage 1000+ user objects, 750+ mailboxes, and 850+ workstations with two DBAs and five help desk specialists. 2
3. Western Union
The Western Union Company is an American international financial services firm with 5,000+ employees headquartered in Denver, Colorado.
Challenges — operating a centralized identity warehouse: The company’s current systems did not allow them to gleam source data from numerous apps in an identity warehouse, resulting in an unclear picture of user access controls. For example, when the managers requested access remediation, they had to go through a ticketing system; however, the system did not effectively update the user profile.
Time-consuming administration of access controls: The time spent administering access controls and reacting to regulatory changes was long. Each new hire required access to 7-10 applications and their related permissions. The access was manually supplied, and it took ~20 minutes per person to submit the access request and receive first-level approval.
The company expected to see who has access to which programs, services, and files, and how to assess whether that access complies with their security policy.
Solutions and outcome: Western Union transitioned from the previous program to an identity and access management (IAM) platform with RBAC capabilities for ~750 applications.
- Enhanced network visibility with an identity warehouse: Western Union started collecting all of the necessary role-based identity data from their HR systems as a single identity warehouse, enabling them to get full insight into users’ access privileges across a centralized environment with 600+ applications.
- Robust user database management: The company claims that the role-based identity management solution streamlined its provisioning procedure for departments that routinely hire new employees. Hence, their provisioning of 50 users now takes 2.5 minutes, down from 14 minutes.3
4. A large bank
A large bank that has a centralized site reliability engineering (SRE) team to oversee network security operations for all resources inside the firm.
Challenges — maintaining manual access controls through Kubernetes and cloud deployment: Manually maintaining this access configuration across an increasing number of accounts were:
- error-prone
- did not comply with certain network audit controls
Solutions and outcome: The bank leveraged templates to define role-based access controls (RBAC) for their SRE team and assigned them to the organization’s accounts
- Enhanced control with access policy templates: The bank created access policy templates for managing cloud Kubernetes and cloud service clusters for MongoDB instances in the sub-accounts. Next, they assigned the profile template to the user accounts and provided the SRE team with policy templates with the needed permissions. Finally, with the role-based profile templates the SRE access has been launched in user accounts and the sub-account administrators lost their privileges to change access controls.4
5. VLI
VLI provides rail-based logistics solutions in Brazil. It manages a railroad system, 100 locomotives, and over 6,000 train vehicles, with 8,000 employees and 1,000 contractors.
Challenge — complex supply chain access controls: The company declared that they have difficulties assigning access to records of goods movement and transactions.
VLI’S CISO states that they have ~9,000 employees who need to use various systems to move the trainsand we need a governed system for better timing; since employees cannot wait to have access to unload a truck.
For example, truck drivers and train operators had to continually sign on to systems to obtain information and transactions as part of the cargo routine, which slowed the process and reduced productivity. Despite the company’s vast IT and development teams, there was no mechanism to detect or track privileged individuals who accessed VLI servers.
Solutions and outcome: VLI mitigated to a centralized user access control platform.
- Fast user access management: VLI reached the capacity to give the right users access to the relevant resources at the right time. VLI reduced user access request response times from 5 days down to seconds.
- Secured servers: VLI secured its servers by removing the requirement for shared authorized login information.
- Reduced the risk of malware and ransomware attacks: VLI limited the number of non-administrator users with administrative access on endpoints and set up lists of reliable and untrusted apps and instructions, thus minimizing the risk of cyber attacks.5
Read more: Cybersecurity risk management, most common cyber attack vectors.
6. Nine Entertainment
Nine Entertainment is Australia’s largest domestically owned media company.
Challenge — access control permissions: Maintaining these custom-built solutions became a huge load on the technical staff since they failed to manage thousands of access control permissions.
Solutions and outcome: Nine Entertainment created a unified directory with real-time AD sync and MFA to build standardized RBAC procedures.
- Unified access management: The company effectively uses 200+ connections to provide access to 50+ applications and multiple WordPress sites based on custom-built permissions.
- Improved authentication controls: With the software implementation, Nine Entertainment users are no longer required for MFA; authentication occurs smoothly.
For example, with identity management and RBAC features, Nine Entertainment could detect users logging in from any location, such as their home office. And, if a user needs to enroll with identity-based authentication, they are guided via a self-service, wizard-based enrollment procedure.6
What is RBAC?
Role-based access control (RBAC) is a model for managing user access to safeguard resources like information, applications, and systems from unauthorized access.
Figure 1: Role assignments of role-based access control
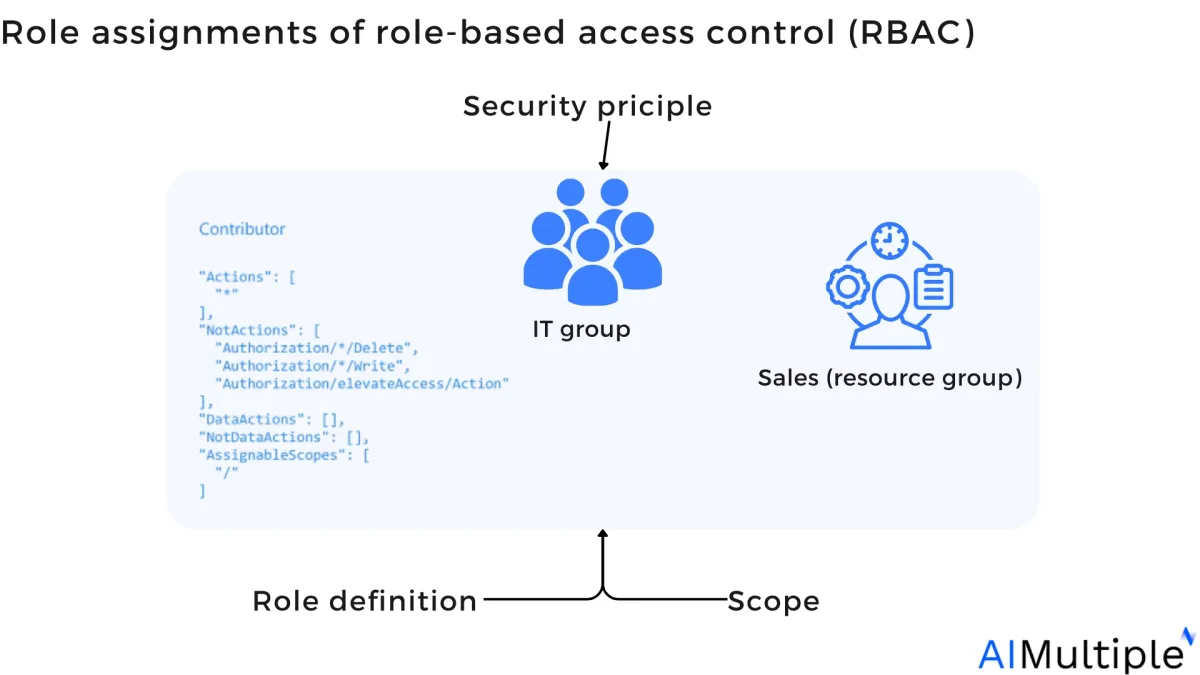
Organizations without RBAC might be challenged to perform some tasks:
- Applying the “least privilege” principle might be difficult for administrators since they can’t comprehend user roles and permissions.
For example, administrators might not identify the lowest degree of access of an employee required to accomplish his or her tasks.
- Onboarding requests (e.g. new hire user permissions) might require additional time and effort because access requests are submitted on a case-by-case basis utilizing specific forms.
- Controlling access of people who switch jobs, might require complex adjustment requests for access on an individual basis.
- Risk related to unauthorized access, which might involve misuse, causing mirrored access (resulting in Bert’s access appearing like Eva’s).
Read more: Mandatory access control (MAC).
RBAC demonstration
RBAC demonstration: Assigning roles and permissions
Consider a dental office that subscribes to a software-as-a-service (SaaS) product to administer, and promote healthcare services to potential customers with the following modules:
- A billing module that collects payments from insurance companies and patients for medical services covered by dental billing codes.
- A sales module that enables dental settings to categorize potential leads according to their likelihood of purchasing a product and service from your organization.
The dental office administrators may use your software’s user interface (see Figure 2) to assign permission access to various business functions.
By using drag-and-drop options administrators can use your software to create different permissions such as “view” “edit” “create” and delete”.
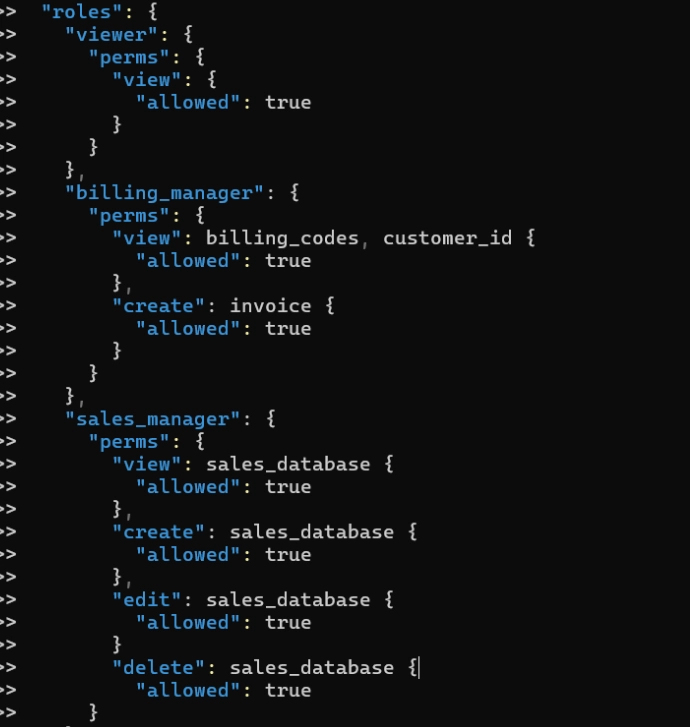
Across the billing module administrators can assign specific rules stating that only the “billing manager” will have a permit to view billing codes, customer ID, and create invoices.
- view: billing_codes
- view: customer_ID
- create: invoice
Similarly, administrators can set permissions for the sales module users such as:
- view: sales_database
- create: sales_database
- edit: sales_database
- delete: sales_database
After setting permissions the administrator can create a “sales manager” role and assign these permissions to that role, limiting other employee’s access to the sales database.
Figure 2: Assessing RBAC policies for the “sales_manager” with user interface (UI) elements
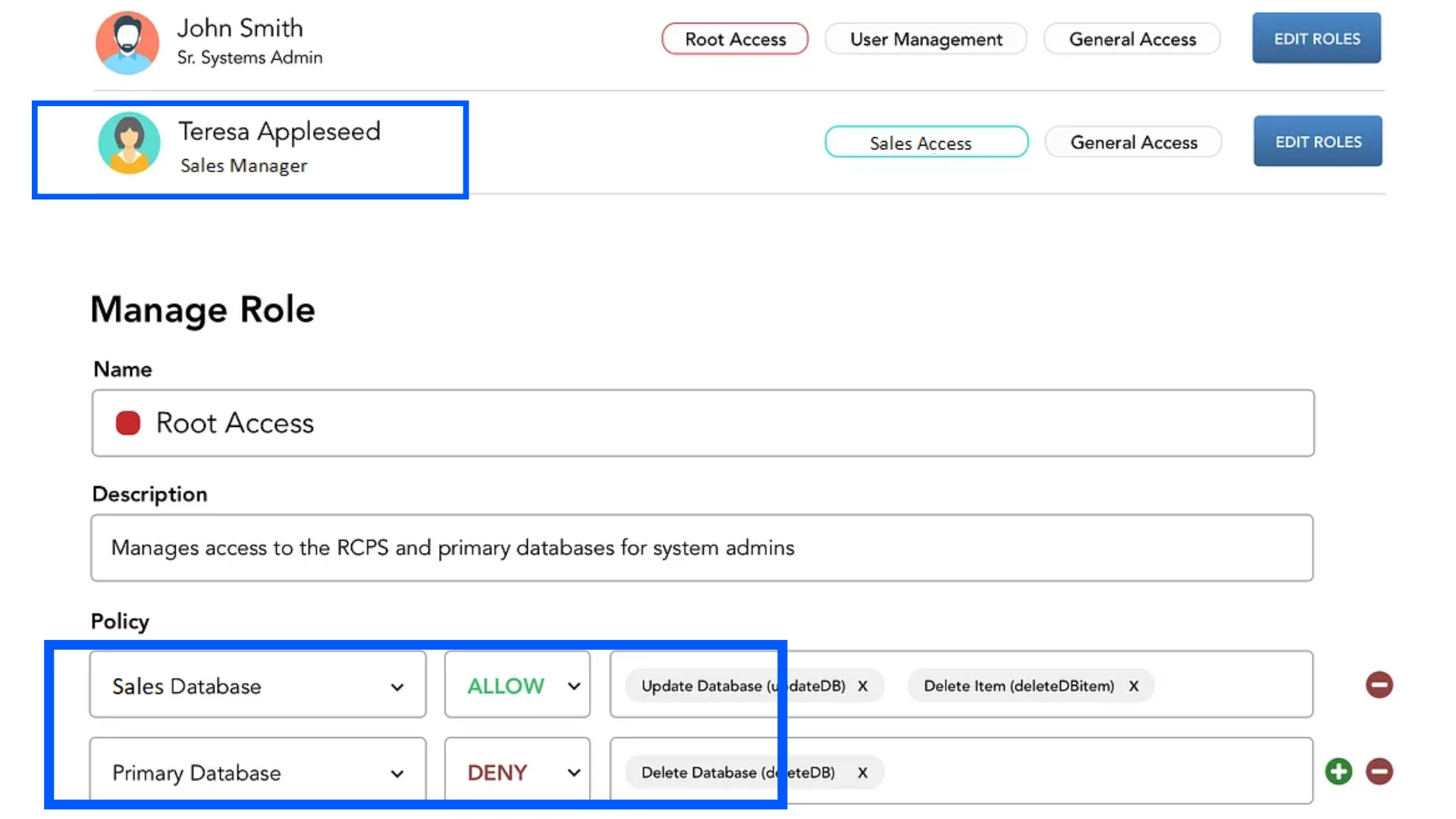
Figure 3: Example of how the data.json file may look for the “billing_manager” and the “sales_manager” roles:
5 benefits of RBAC
1. Limited excessive access
With the transition to cloud infrastructures, SaaS apps, and the simplicity of single-sign-on (SSO), individuals and groups frequently inherit roles with excessive access. RBAC helps reduce this risk by designing groups and subgroups so that users only have access to what they need.
Example: Assume users are submitting their images to a competition for the best travel photos, and we expect only the competition judges will see those photos. The policy outlined below allows any input in the position of “travel_photo_judges” to examine the photo “travel_photo1997.jpg”.
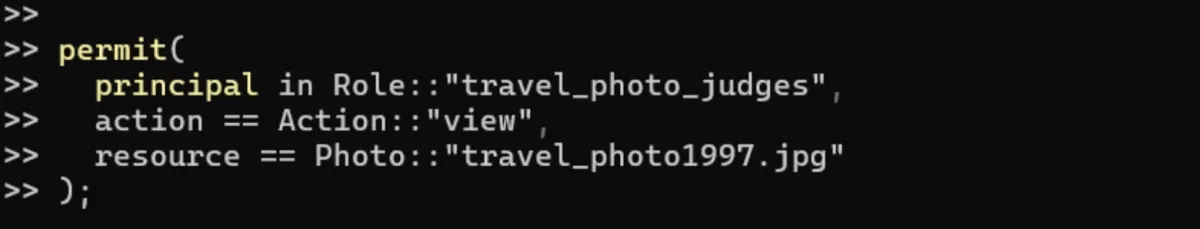
This is accomplished via RBAC evaluation which passes group information to the evaluation engine and determines if the input indicated in the permission request is a member of the group.
2. Unique access control policies
RBAC systems can provide unique access control policies based on companies’ needs compared to mainframe access control systems.
Example: RBAC systems administrators can also employ roles for administrative purposes by restricting network access based on an individual’s role such as “guest user with limited permissions”
3. Application level support
RBAC helps companies to have a granular access approach by supporting permissions at the application level.
Example: RBAC can assign a set of permissions in a writing program that allows users to read, edit, and delete content.
4. Flexible role allocation
RBAC models can build relationships between roles, permissions, and users. Two roles might be mutually exclusive, enabling a single user to have two roles. Roles can inherit permissions provided to other roles.
Example: When permission is set, it can be allocated numerous roles. For example, Matt may hold both the administrative and financial specialist roles, while Eva may only have the financial specialist role.
5. Demonstrating compliance
Implementing RBAC will assist financial institutions and healthcare providers in demonstrating technical and operational standards with requirements such as HIPAA, PCI, and PHI.
Why use RBAC?
Unauthorized network access accounts for 40% of third-party cyber intrusions that occurred in 2023.7 Considering that unauthorized access is one of the main drivers of data breaches, establishing RBAC is critical, especially for companies with several employees. Here are some benefits:
1. Improved security
- Minimized risk of unauthorized access: By assigning permissions based on roles, rather than individuals, it becomes easier to ensure that users only have access to the information and resources necessary for their roles.
- Apply the least privilege principle: Users are granted the minimum level of access required to perform their jobs, reducing the risk of internal data breaches and exposure to sensitive information.
2. Simplified management
- Ease of administration: Administrators can easily assign and manage user permissions by roles, rather than having to manage permissions on an individual basis.
- Scalability: As organizations grow, new users can quickly be assigned to predefined roles, streamlining the onboarding process and ensuring consistent access control policies.
3. Reduced Risk of Errors
- Centralized control: Centralized management of roles reduces the risk of human error in assigning permissions and ensures that access policies are consistently enforced.
- Clear accountability: It is easier with RBAC to determine responsibility and accountability for access to sensitive resources.
4. Adhere to compliance
- Regulatory compliance: RBAC helps organizations comply with various regulatory requirements by ensuring that access to sensitive data is controlled and documented.
- Audit trails: The role-based nature of access control makes it easier to track and audit who has access to what resources, facilitating better monitoring and reporting.
Read more: Mandatory access control (MAC).
How do you implement RBAC in your organization?
1. Create inventory systems
Make a detailed inventory of all servers, databases, applications, external websites, and other resources that users may require access:
- Include physical security in this list as an option, which would encompass access to servers or other key physical areas and resources.
- Make a map showing who (or what) presently has access to those resources.
2. Establish business workflows
Determine who will interact with them and how:
- Identify the specific resources that various users require to complete their tasks and map internal procedures.
- Decide whether to allow authorization inheritance between roles or require separation of tasks.
- Analyze whether to construct roles that are consistent with existing usage or to employ newly defined roles.
3. Create roles based on your business functions
Predefined roles examples may include:
Power User: Manages the model creation and execution process. This job provides high-level access to many functional domains. Power Users can conduct all of the same tasks as regular users. Furthermore, a Power User can accomplish these tasks:
- Creates ad hoc layouts, and loads data employing the data integration system.
- Manipulates data.
- Develops and executes integrations.
- Builds models.
User: Users can execute all of the same things as Viewers. A User can do the following extra operations:
- Performs ad hoc tasks, but cannot write back into ad hoc layouts or load data using the data Integration system.
- Creates, changes, and deletes rules
- Executes and deletes reports.
Viewer: Can only see and evaluate data; cannot write to it. A Viewer conducts the following operations:
- View models.
Note: Predefined roles are hierarchical. Higher-level roles inherit the access given by positions at the lower levels. Power users inherit privileges provided through the User, and Viewer roles in addition to their own.
4. Audit regularly
Perform periodic network audit practices to ensure that users are allocated to the right roles (since roles might change over time) and that each position has the necessary permissions.
Don’t make one-time alterations to accommodate one employee’s specific demands. Either change their position’s permissions or establish a new role if needed.
Read more: Network security audit tools.
Further reading
- Top 10 Microsegmentation Tools
- Intrusion Prevention: How does it work? & 3 Methods
- Role-based access control (RBAC)
- Network Segmentation: 6 Benefits & 8 Best Practices
- 80+ Network Security Statistics
- Network Security Policy Management Solutions (NSPM)
- Top 10 SDP Software Based on 4,000+ Reviews
- Top 10 Network Security Audit Tools Based on 4,000 Reviews
AIMultiple can assist your organization in finding the right vendor.
External Links
- 1. ”The Role-Based Access Control System of a European Bank: A Case Study and Discussion”
- 2. Case Study on Interfaith Medical Center - Easy and Effective HIPAA compliance Established using ManageEngine ADManager Plus's Active Directory Management and Reporting Capabilities.
- 3. The Identity Governance Blog.
- 4. Enterprise-managed IAM: A SRE team case study | IBM.
- 5. ”More than Point A to Point B”
- 6. Nine Entertainment Customer Case Study | OneLogin.
- 7. 2023 Third Party Data Breach Report - Black Kite. Black Kite



Comments
Your email address will not be published. All fields are required.