Misconfiguration of security management systems cause 99% of firewall security breaches.1 Therefore, using advanced firewall configuration software is essential to manage configurations and strengthen defenses.
See the comparison of the top 5 open source configuration tools based on features like audit trail and configuration rule analytics:
Comparison of top 5 open source configuration tools
| Tool | Audit Trail | Rule Analytics | Status Tracking | |
|---|---|---|---|---|
| Red Hat Ansible | ❌ | ✅ | ✅ | |
| Progress Chef | ❌ | ❌ | ❌ | |
| Puppet Enterprise | ❌ | ✅ | ❌ | |
| Rudder | ✅ | ✅ | ❌ | |
| CFEngine | ❌ | ❌ | ❌ |
To see the definitions of these features or understand common features of these solutions, see features of configuration management tools.
Businesses looking for more enterprise-focused features may explore closed-source firewall configuration management software.
Market presence comparison
| Tool | Github Star | User Rating* | Number of Employee** | Platform Compatibility*** |
|---|---|---|---|---|
| Red Hat Ansible | 61K | 4.4 out of 183 reviews | 5 | MacOS, Linux |
| Progress Chef | 8K | 4.2 out of 113 reviews | 169 | MacOS, Linux |
| Puppet | 7K | 4.3 out of 67 reviews | 243 | MacOS, Linux |
| Rudder | Less than 1K | 4.7 out of 19 reviews | 19 | Linux |
| CFEngine | Less than 1K | 4.8 out of 2 reviews | 21 | MacOS, Linux |
*Based on data from leading B2B review platforms
**Based on data from LinkedIn
*** All analyzed software packages are compatible with Windows.
Disclaimer: ❌ means that the AIMultiple team couldn’t identify publicly available evidence.
Ranking: The companies are ordered based on the total count of reviews.
Inclusion criteria:
- All vendors featured in this list employ over 20 individuals.
- Only vendors with over 10 reviews across all review platforms were considered.
1. Red Hat Ansible
Red Hat Ansible is one of the most popular open source configuration management tools, boasting 61K stars on GitHub. Ansible uses simple configuration files written in YAML, known as playbooks, which are easy to read and write. This configuration management tool is known for its agentless architecture, which simplifies the deployment process.
Features
It focuses on compliance management, rule analytics, and status tracking, making it ideal for managing configurations in complex environments. These features ensure regulatory adherence, optimize performance, and provide real-time updates on configuration changes.
Case study
Zoom uses Ansible to meet strict security industry security standards, ensure compliance, and efficiently deploy applications.2
2. Progress Chef
Progress Chef focuses on infrastructure as code and automates the deployment processes.
Features
Though it lacks rule analytics, status tracking, and audit trails, Chef’s strength lies in its automation infrastructure, enabling consistent configuration across environments. This helps streamline deployment processes and maintain regulatory compliance.
Case study
Chef’s configuration management system helps IBM by providing a stable and automated build-and-converge system. This ensures that everything is in place and properly configured, reducing the risk of application deployment failures and manual drift across nodes.
IBM aims to empower customers to deploy at their own pace while meeting business drivers, and Chef’s automation capabilities align with this goal by maintaining a strong and consistent IT infrastructure.3
Figure 1. Process of achieving reliability with a group of tools, including Chef, a configuration management tool
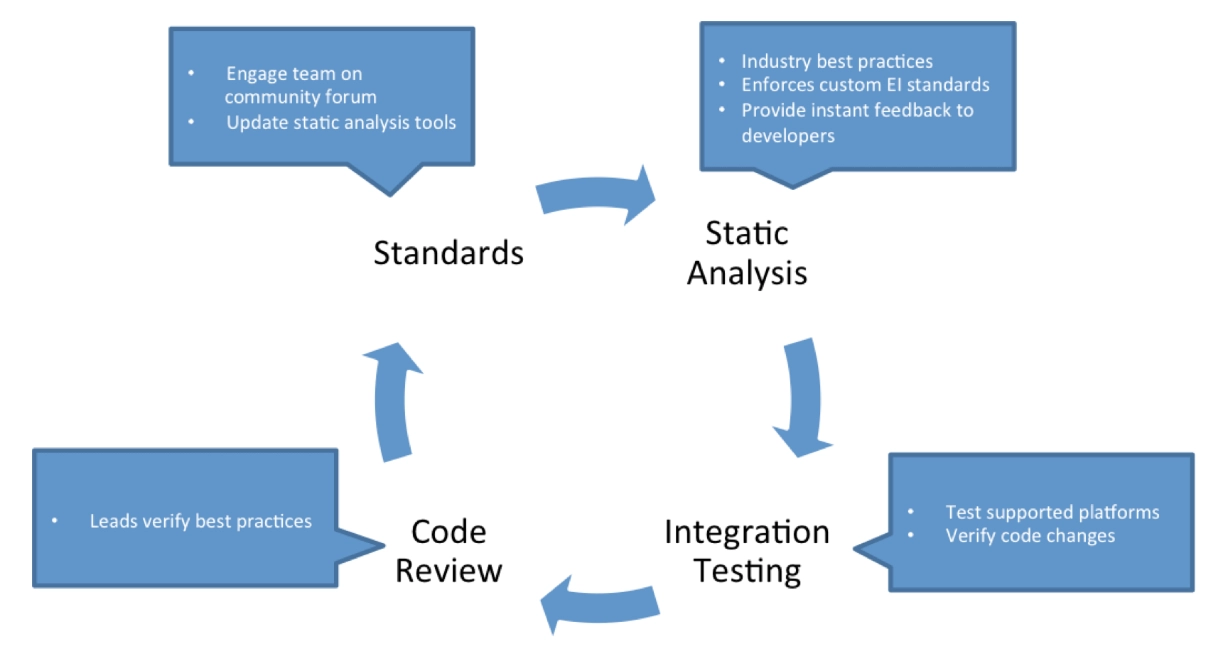
Source: Chef4
3. Puppet Enterprise
Puppet is a powerful configuration management system that uses a declarative language to define system configuration. It works in a client-server model, where the server sends configuration instructions to the clients. Administrators can describe configurations in simple terms like users, services, and packages. Puppet ensures that the servers match these descriptions.
Features
Puppet Enterprise offers strong compliance management and rules analytics. These features ensure configurations meet standards and optimize performance. Despite missing audit trails and status tracking, Puppet’s declarative language and central server model make it effective in managing complex environments.
Case study
Puppet’s configuration management system empowers Athenahealth by automating application stack builds, ensuring security consistency, and enhancing compliance across its infrastructure.
This automation significantly reduces labor costs, accelerates deployment and update processes, and improves security monitoring and alerting, aligning with Athenahealth’s goal of achieving “Zero-Touch” builds and streamlined infrastructure management.5
Figure 2. Benefits of Puppet as a configuration management tool
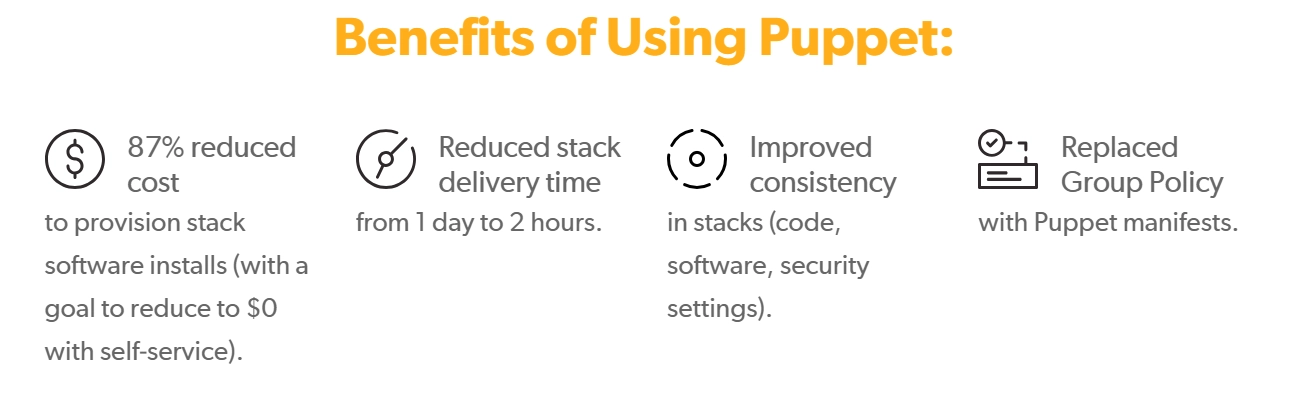
Source: Puppet Enterprise6
4. Rudder
Rudder is an open source configuration management tool that helps automate system configuration for large IT setups. It uses a lightweight local agent installed on each machine it manages.
Features
Rudder provides audit trails, compliance management, and rule analytics. These features track configuration changes, ensure regulatory adherence, and optimize the performance of software installation. Though it lacks status tracking, Rudder’s audit trail and compliance focus make it valuable for security-conscious environments.
Case study
Rudder’s configuration management system aids BMW in standardizing its global IT infrastructure, ensuring security compliance, and enabling centralized and secure management of configurations and package installations across multiple servers.
Rudder’s configuration management contributes to efficient configuration reliability, supporting its stringent security requirements and multi-client environment.7
Figure 3. Five steps of the package and configuration management tool implementation of Rudder
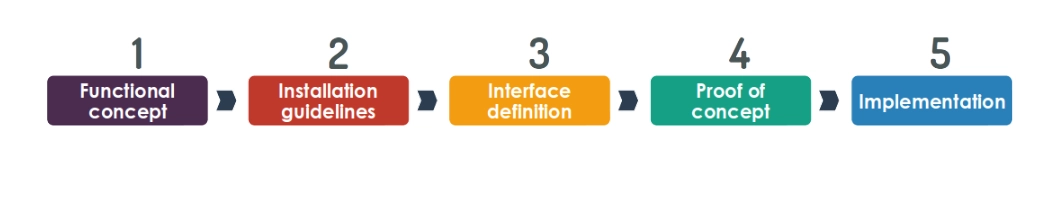
Source: Rudder8
5. CFEngine
CFEngine is known for its efficiency in managing large scale infrastructures and automating administrative tasks in complex workflows. This software configuration management (CM) tool manages configurations for many computers using either a client-server setup or independently.
If a client’s state doesn’t match the desired configuration, it’s automatically changed. Configurations are described using a declarative language. CFEngine’s focus on security and lightweight footprint makes it suitable for managing configurations in extensive and distributed environments.
Features
CFEngine focuses on compliance management. Although lacking rule analytics, audit trails, and status tracking, CFEngine supports infrastructure automation and automated control of server configurations, maintaining adherence to regulatory standards and ensuring IT infrastructure security and reliability.
Case study
LinkedIn uses CFEngine to automate operations across a vast server network of over 100,000 servers, enhancing efficiency and cost-effectiveness. With CFEngine’s automation tools, LinkedIn’s DevOps team can seamlessly manage daily production changes and large scale computer systems efficiently.9
Features of configuration management tools
All CM tools mentioned in the table provide encryption and compliance management capabilities.
Robust encryption capabilities secure sensitive configuration data, credentials, and communication channels. Encryption ensures data integrity, confidentiality, and protection against unauthorized access or breaches.
Compliance management ensures that configurations adhere to regulatory standards, industry best practices, and organizational policies. By leveraging compliance management, organizations can mitigate risks, avoid penalties, and maintain a secure and compliant IT environment.
Differentiated features
1. Audit trail
An audit trail feature in CM tools provides a detailed record of changes made to configurations over time. This feature is crucial for accountability, security, and compliance auditing purposes. With an audit trail, organizations can trace configuration modifications, identify unauthorized changes, and maintain a secure and transparent configuration management process.
2. Rule Analytics
Rule analytics in open source configuration tools provides insights into configuration rules, their impact on system performance, and potential optimization opportunities. This feature analyzes configuration rules to identify inefficiencies, security vulnerabilities, and areas for improvement.
Rule Analytics enhances configuration management by optimizing rule sets, improving resource utilization, and ensuring configurations align with best practices.
3. Status tracking
Status tracking capabilities in configuration management tools enable real-time monitoring and tracking of configuration changes and deployment statuses. This feature facilitates proactive management, identifies bottlenecks or issues, and ensures timely resolution of configuration-related issues.
By tracking status effectively, organizations can improve operational efficiency, reduce downtime, and enhance overall configuration management effectiveness.
Finding the best configuration management tools
Selecting the right tools enables organizations to streamline operations, ensure compliance, and manage complex environments effectively. Businesses may consider the following factors while choosing the best configuration management tool that fits their needs.
- Audit trail capabilities: Evaluate open source configuration tools that offer robust audit trail capabilities.
- Rule analytics: Consider tools with rule analytics features that analyze configuration rules for optimization and performance enhancement.
- Status tracking: Look for open source configuration tools that provide real-time status tracking of configuration changes and deployments.
- Compliance management capabilities: Choose open source configuration tools with robust compliance management capabilities that help ensure configurations adhere to regulatory standards and internal policies.
- Encryption: Prioritize open source configuration tools that offer strong encryption capabilities to protect sensitive data, configurations, and communications.
Benefits of open source configuration tools
Configuration management tools provide several benefits to their users. Here are some benefits:
1. Swift disaster recovery
Open source configuration tools streamline disaster recovery by ensuring assets are easily recoverable, offering quick rollback options, and maintaining comprehensive documentation of recovery points and logs.
2. Enhanced uptime and reliability
Tracking system changes reduces the risk of downtime and security breaches, as misconfigurations are a common cause of outages. Proper configuration management allows test environments to mirror production, minimizing surprises and ensuring increased uptime and site reliability.
3. Optimized resource utilization
By eliminating duplicates and optimizing resource usage, open source configuration tools enhance resource utilization efficiency. This optimization leads to cost savings and improved overall system performance.
4. Decreased cost
Open source configuration tools can offer a decreased cost benefit compared to proprietary solutions, as they often come with lower licensing fees and offer flexibility for customization and integration with existing systems. Additionally, configuration management tools can lead to decreased costs by streamlining operations, reducing manual labor, and improving efficiency.
Configuration management tools offer a range of benefits in a DevOps pipeline:
- Version control: Easily track and manage changes in software configurations over time.
- Automation: Streamline tasks like setup, deployment, and management of configurations, reducing manual effort.
- Collaboration: Provide a central platform for stakeholders to collaborate, share configurations, track changes, and resolve conflicts efficiently.
- Consistency: Ensure consistent configurations across various environments, enabling applications to behave predictably in different settings.
FAQ
What is a configuration management tool?
Configuration management in software development involves tracking and managing changes to applications and their infrastructure. Configuration management tools ensure configurations are known and trusted, reducing reliance on tribal knowledge. These tools enhance visibility, streamline control processes, and automate system configurations based on predefined states. Integration with version control, testing, and bug tracking tools promotes internal best practices, productivity, and quicker recovery from infrastructure failures.
Further Reading
- 3-Step Guide to Effective Firewall Audit
- Top 12 Firewall Audit Software & Integration-Based Comparison
External Links
- 1. Focus On The Biggest Security Threats Not The Most Publicized.
- 2. Zoom for Government enhances security with a Red Hat platform.
- 3. IBM - Customer story | Chef .
- 4. IBM - Customer story | Chef .
- 5. athenahealth Automates Stack Builds + Secures IT with Puppet.
- 6. athenahealth Automates Stack Builds + Secures IT with Puppet.
- 7. Success Story Configuration and package management for an industrial company. Rudder. Accessed: 23/May/2024.
- 8. Success Story Configuration and package management for an industrial company. Rudder. Accessed: 23/May/2024.
- 9. Case Studies: LinkedIn. CFEngine. Accessed: 23/May/2024.


Comments
Your email address will not be published. All fields are required.