Network security statistics show that the United States has the highest average total cost of a data breach with ~$9M.1 . Cybersecurity is a critical issue for both businesses and individuals. Both proxy servers and firewalls provide data and network security. However, proxy server and firewall have its own benefits, and achieving cybersecurity without understanding these distinctions can be difficult.
In this article, we discussed how firewalls and proxy servers work, what benefits they provide, and how they differ from one another.
What is a proxy server?
A proxy server is an intermediary between the client machine and the target website. The proxy server receives client connection requests and transmits all incoming and outgoing data traffic between clients and web servers.
What is a firewall?
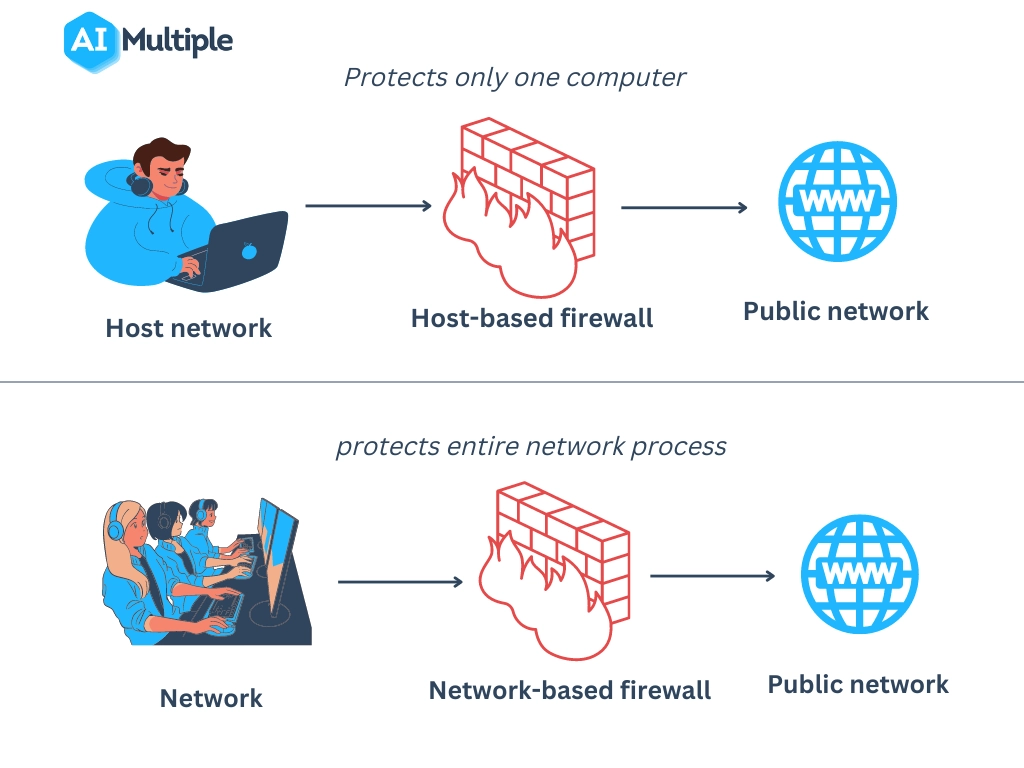
A firewall is a network security system that detects and monitors unauthorized access to a private network to protect it from untrustworthy public networks. There are mainly two types of firewalls, network-based and host-based systems. Both control network traffic and provide network security, but in different ways (see Figure 1).
- Network-based firewalls: A network-based firewall is placed between clients and web servers. Unlike host-based firewalls, a network-based firewall provides network-level protection. A network-based computer protects the entire network. It is suited for larger networks like large-size companies.
- Host-based firewalls: A host-based firewall is a software that monitors network traffic between clients and servers. It is installed on a single computer and protects that computer only. It is suited for small networks like individual computers.
Figure 1: Process comparison of a network-based firewall and a host-based firewall
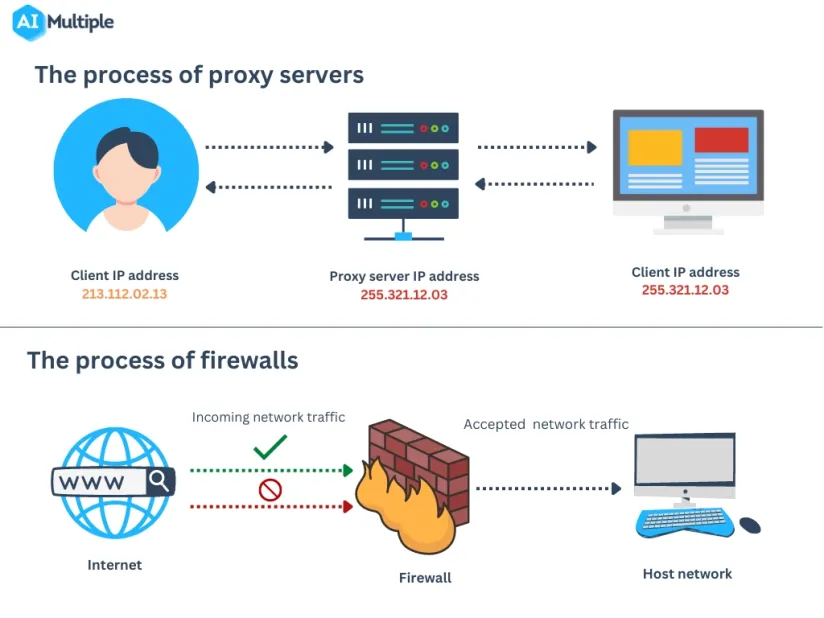
How does a proxy server work?
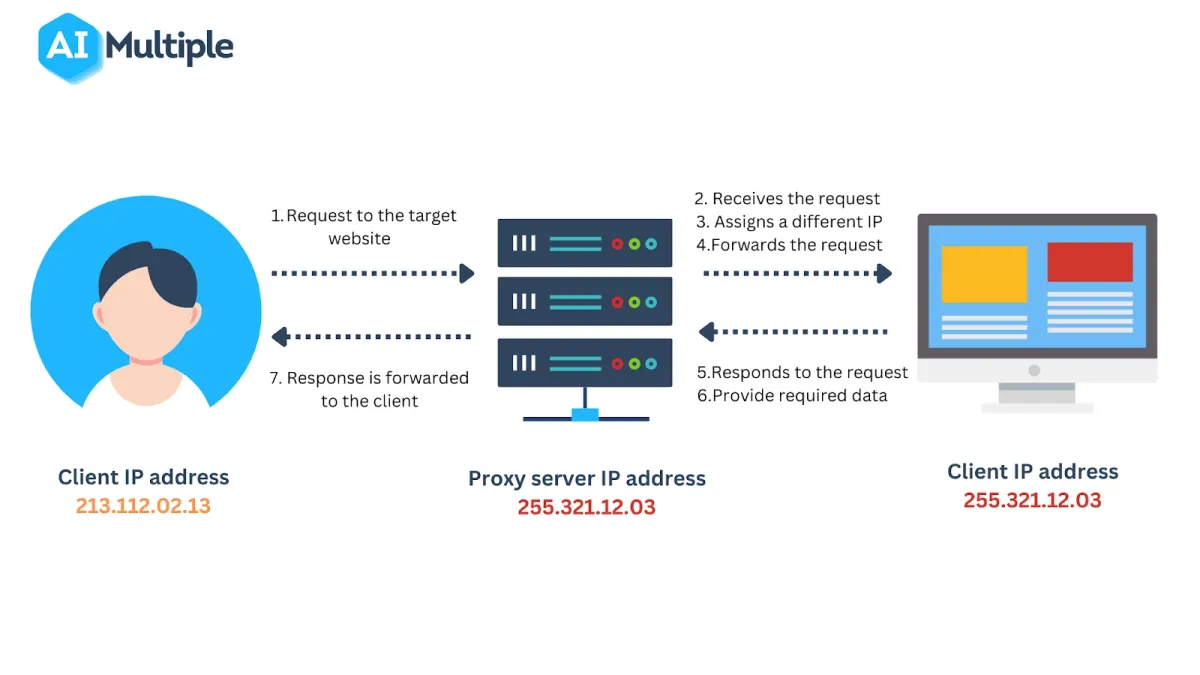
Both a firewall and a proxy server are network security systems that aim to protect user information. However, they differ in the methods and techniques they employ. We described the general proxy server process in 6 steps:
- A client requests to view content on a website.
- The proxy server receives the client’s connection request and hides the client’s real IP address by assigning a different IP address.
- The proxy server forwards the client’s request to the destination without revealing the client’s real network id.
- The web server receives the client’s request.
- When the target web server accepts the request, the requested information returns to the proxy server.
- The proxy server receives information on behalf of the user and forwards it to the client.
Figure 2: Process representation of proxy servers
To learn more about the various types of proxies and their features, see the ultimate guide to proxy server types.
Top proxy service providers
| Proxy providers | Proxy types | Starting price/GB | Free trial | PAYG |
|---|---|---|---|---|
| Bright Data | Residential ISP Mobile Datacenter | $6.3 | 7-day | For all proxy types |
| Oxylabs | Residential ISP Mobile Datacenter | $9 | 7-day | Residential Mobile |
| Nimble | Residential | $8 | 7-day | ❌ |
| Smartproxy | Residential ISP Mobile Datacenter | $7 | 14-day money-back | Residential Mobile |
| NetNut | Residential ISP Mobile Datacenter | $15 | 7-day | ❌ |
| IPRoyal | Residential ISP Mobile Datacenter | $7 | 24-hr refund | N/A |
| SOAX | Residential ISP Mobile Datacenter | $6.6 | 3-day trial for $1.99 | ❌ |
Starting price/GB: The basic monthly subscription package available from the provider for residential proxy services.
How does a firewall work?
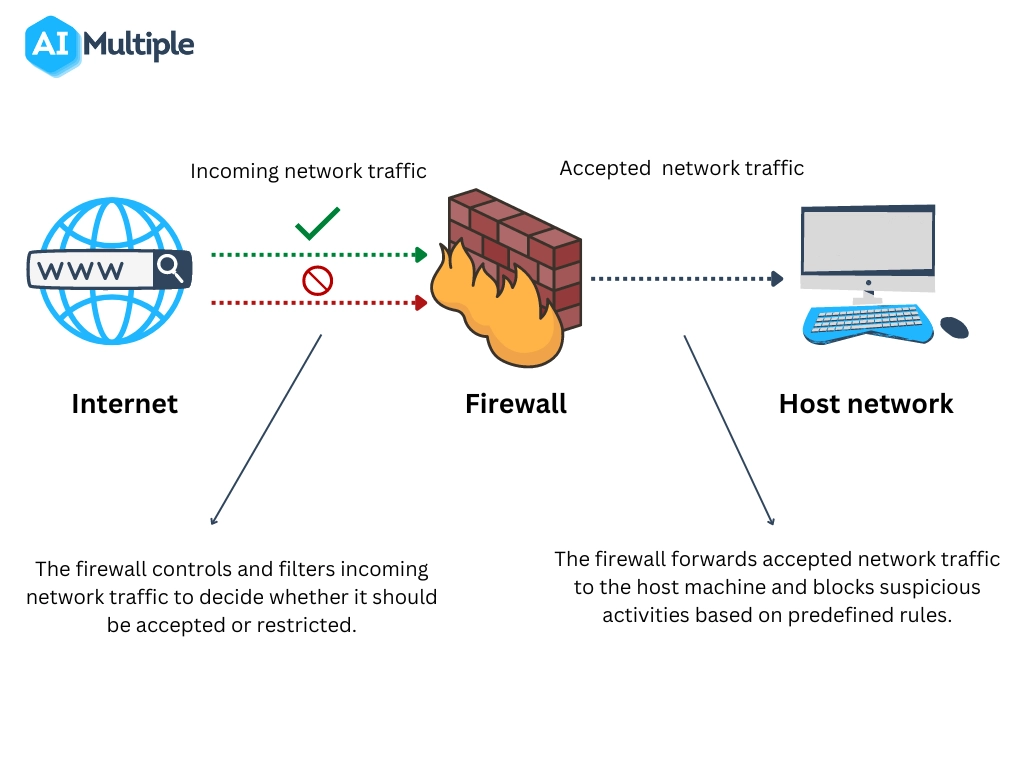
A firewall acts as a gatekeeper between clients and the public internet to control all incoming and outgoing network traffic. To protect clients’ private networks from public network attacks, it checks the source of the public network and filters out unwanted traffic within the network. Here is a basic roadmap of how firewalls control traffic between private and public networks (see Figure 3):
- The client requests a connection to a web server.
- The web server receives the connection request and provides the requested information.
- The firewall controls and analyzes incoming network traffic from the web server to determine whether it should be allowed or denied. If traffic comes from a trusted web server, the firewall allows access to the web server so the client can receive the requested information.
Figure 3: Process representation of firewalls
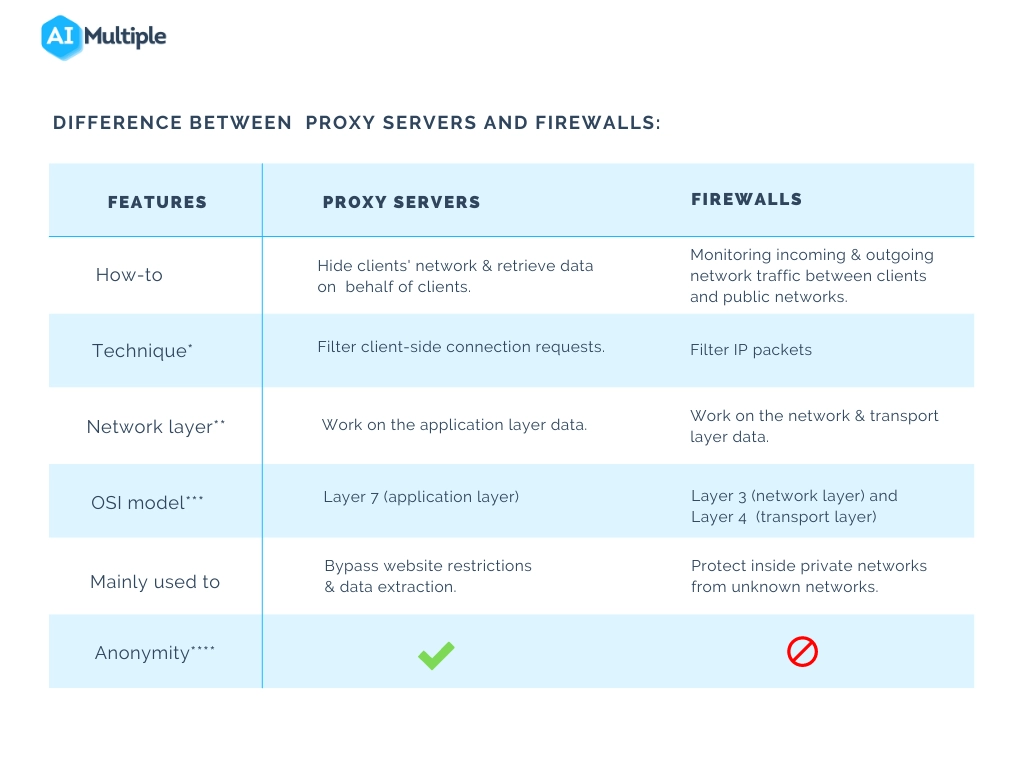
What is the difference between proxy and firewall?
Figure 4: A comparison of proxy server and firewalls
Explained features
Technique*:
- Firewalls: Data that passes through a network is split up into small packets. IP packet filtering is a method used by firewalls. It is used to ensure that data packets arrive at the intended destination. Firewalls filter IP packets based on the rules that are configured in them. They monitor IP packets to determine where the data packet is coming from and where it is going.
- Proxy servers: When the target website accepts a client’s connection request, proxy servers receive the information from the target website and forward it to the client’s actual IP address without revealing the client’s real network id.
Network layer** & OSI model***
An OSI model consists of seven layers that allow the machine to communicate with each other. It explains how data is transformed between networks. Firewalls function at layers 3 (network layer) and 4 (transport layer), whereas proxy servers function at layer 7. (application layer).
- Transport layers receive incoming and outgoing data in the network traffic and divide it into data units (also called segments). They are also responsible for the amount of data transferred through the network. Transport layers determine the amount of data passed through the layer by decreasing and increasing the amount of transferred data.
- Network layers receive data segments from transfer layers. Received data segments are divided into packets by network layers. Network layers assign IP addresses to computers in the network to ensure that data packets reach their intended destination. The second function of network layers is routing data packets from source to destination.
- Application layers enable users to access network services by determining the identity and availability of network communication partners.
Anonymity***
Proxy servers mask clients’ real network IDs to protect their identity when they connect to the internet.
Sponsored
It is crucial to choose a reliable proxy provider to ensure your data and privacy are protected. Oxylabs provides a variety of ethically sourced proxy pools, such as residential, datacenter, mobile, and SOCKS5 proxies, based on the user’s specific data collection requirements and budget.

What are the main benefits of proxy servers?
- Hide IP addresses
- Increase privacy
- Bypass geo-restricted content
- Overcome obstacles such as IP blocks
- Speed up the process of information retrieval
- Bypass bandwidth throttling
What are the main benefits of firewalls?
Network traffic protection
A firewall keeps a private network by filtering incoming traffic based on a set of rules. It examines the IP address and network source and rejects incoming traffic from suspicious IP addresses. You can, for example, configure your access list by modifying your protocol settings. Instead of using the “ANY” option, select TCP, UDP, and IP protocols. Any incoming data from TCP, UDP, and IP can pass through the firewall. Other incoming traffic will be denied by the firewall based on your predefined rules.
Protect against cyberattacks
Firewalls act as a security barrier between the client and unauthorized networks. It controls IP addresses, domain names, and destination ports to filter network traffic. All incoming and outgoing data must first pass through the firewall.
Further reading
- The Ultimate Guide to Proxy vs. VPN: Which One Is Better?
- The Ultimate Guide to Rotating Proxies vs. Static Proxies
- The Ultimate Guide to Proxy Server Types
Also do not forget to check out data-driven list of web scrapers
Please reach out to us if you have any further question:


Comments
Your email address will not be published. All fields are required.