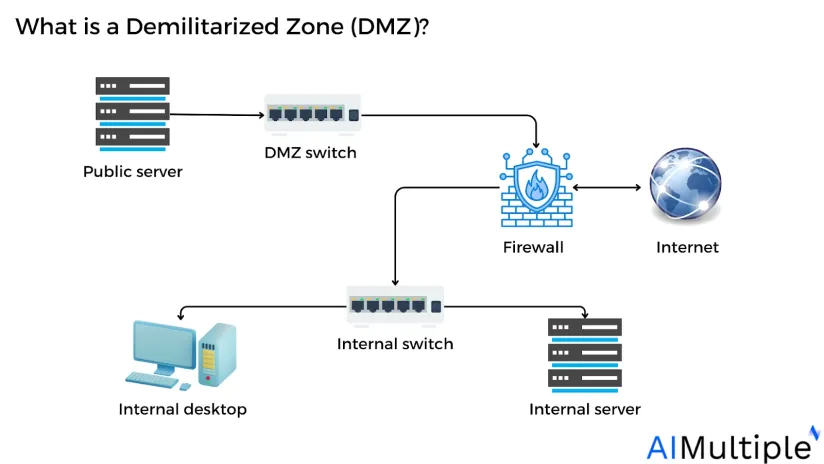
A Demilitarized Zone (DMZ) network is a subnetwork containing an organization’s publicly accessible services. It serves as an exposed point to an untrusted network, often the Internet.
DMZs are used across various environments—from home routers to enterprise networks—to isolate public-facing services and protect internal systems. To illustrate this, I have illustrated real-world DMZ examples and different DMZ architectures (single vs. dual firewall)
Why is DMZ important in network security?
DMZs add a layer of network segmentation to defend internal operational technology. It creates a buffer zone between the public internet and private networks
These subnetworks limit external access to internal servers and assets, making it more challenging for attackers to penetrate the internal network.
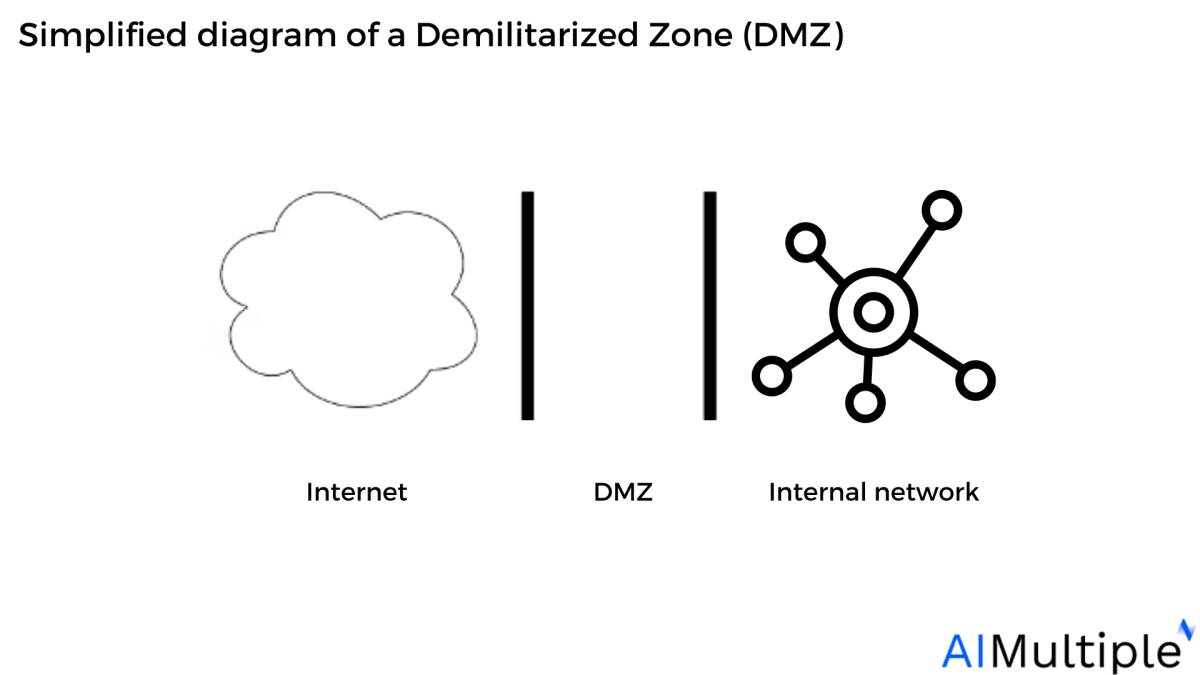
In typical configurations (see figure above), the DMZ subnet is placed between two firewalls or on a dedicated segment of a single firewall with multiple interfaces. This ensures that:
- Unauthorized access to the internal network is blocked, even if a DMZ-hosted service is compromised.
- All inbound traffic from the internet is first filtered and inspected before reaching the DMZ servers.
- Internal network traffic to and from the DMZ is tightly controlled and monitored.
DMZ examples
DMZ example 1: DMZ implementation with one firewall
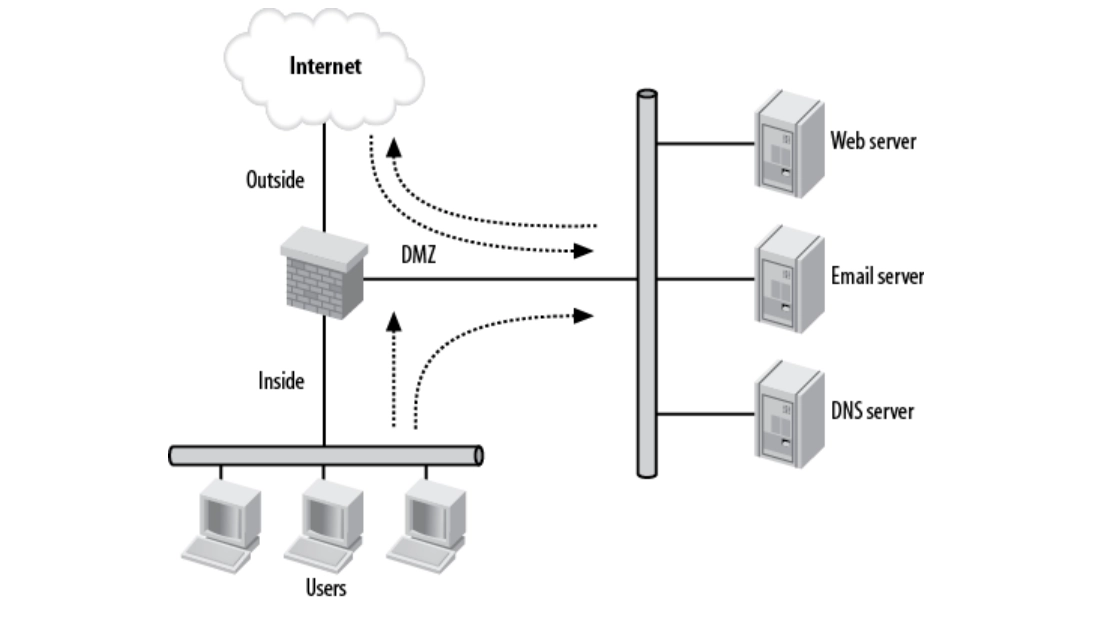
As seen in Figure 1, the DMZ network is neither within nor outside the firewall. It is accessible through both internal and external networks.
One of the primary advantages of this network diagram is isolation. For example, if the email server is hacked, the attacker will be unable to access the internal network. In this scenario, the attacker may access various servers in the DMZ as they share the same physical network.
Figure 1: Simple DMZ diagram
Source: International Journal of Wireless and Microwave Technologies1
In this configuration, the DMZ enforces the following access controls:
- Inside network: The internal network can start connections to external networks, but the network cannot start connections to the internal network.
- Outside network: The outside network cannot establish connections with the inner network, however, the outside network can begin connections to the DMZ.
DMZ example 2: A DMZ connected to a third-party device
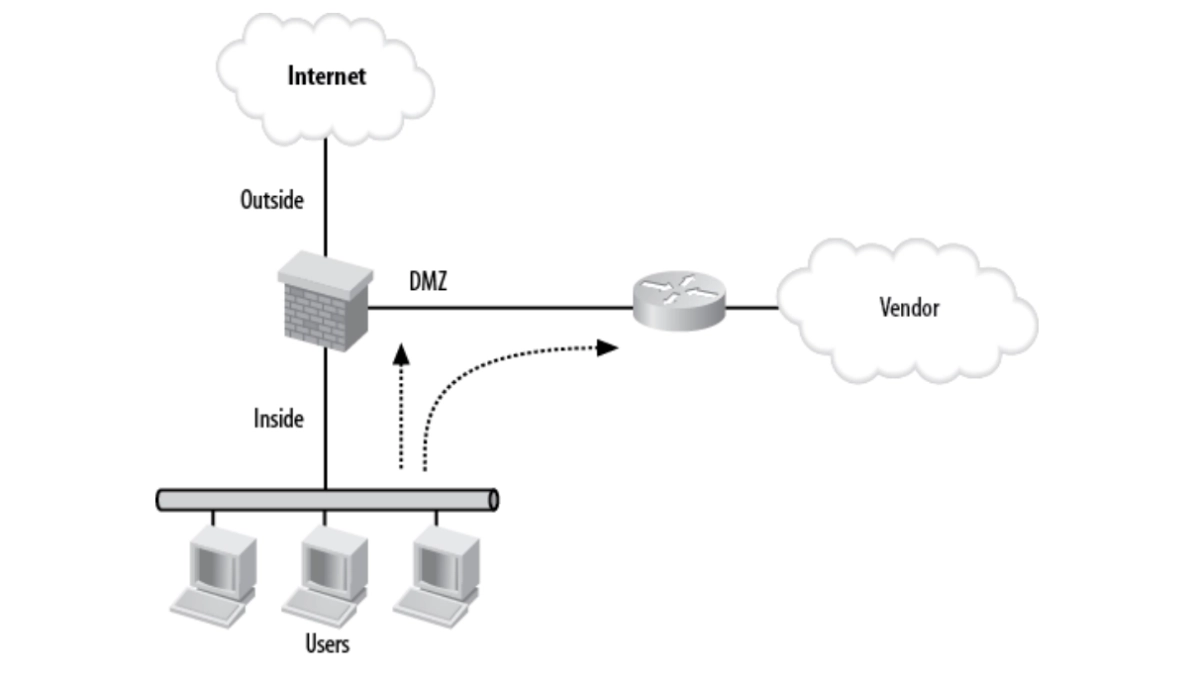
Another typical DMZ approach is connecting to a third-party device, such as a vendor. Figure 2 depicts a network with a vendor linked by T1 to a router in the DMZ.
This DMZ example can be used when companies outsource their systems to an outside party, allowing access to the vendor’s server via this setup.
Figure 2: DMZ connecting to a vendor
Source: O’Reilly Media2
DMZ example 3: Multiple DMZs connected to a third-party device
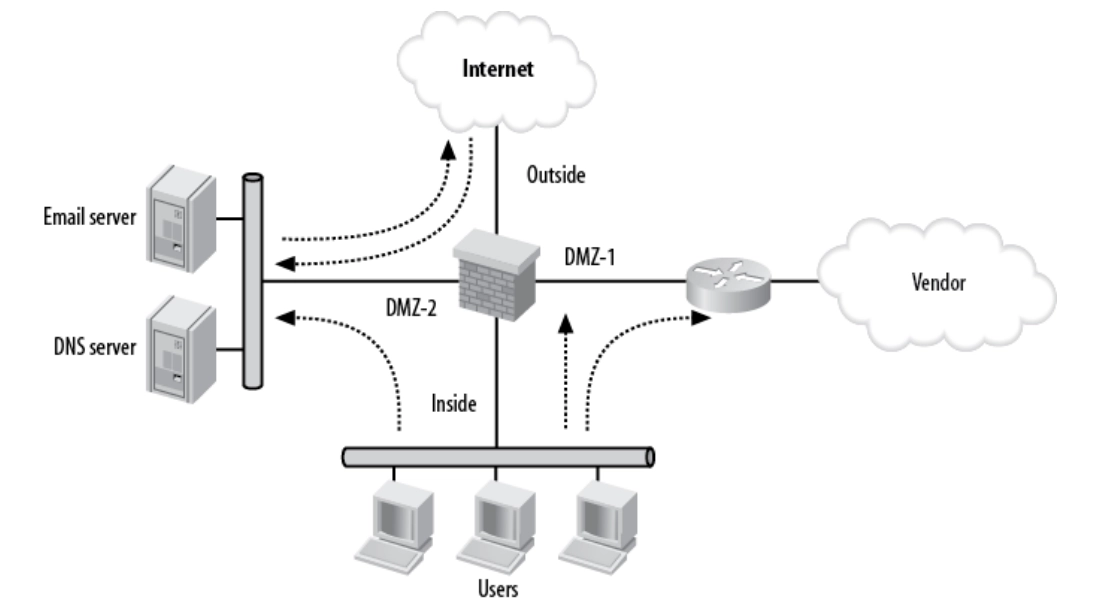
Sometimes a single DMZ is insufficient for organizations that operate complex networks. Figure 3 depicts a network that has several DMZs. The design combines the first two examples: the Internet is outside, and the users are within the network.
Figure 3: Multiple DMZs
Source: O’Reilly Media3
- DMZ-1 is an access point to a vendor.
- DMZ-2 is where the Internet servers are located.
The security requirements are consistent with the previous example (Example 2), but an additional consideration is needed: whether DMZ-1 is permitted to initiate connections to DMZ-2, and vice versa.
Evaluating this bi-directional access helps enforce granular security controls within complex network environments.
DMZ architectures
A DMZ can be configured in a variety of ways, ranging from a single firewall to dual or multiple firewalls. The majority of current DMZ architectures include twin firewalls that can be scaled to support complex networks.
1. Single firewall
A single firewall with at least three network interfaces is needed to build a network architecture that includes a DMZ.
Figure: Illustration of a single firewall architecture
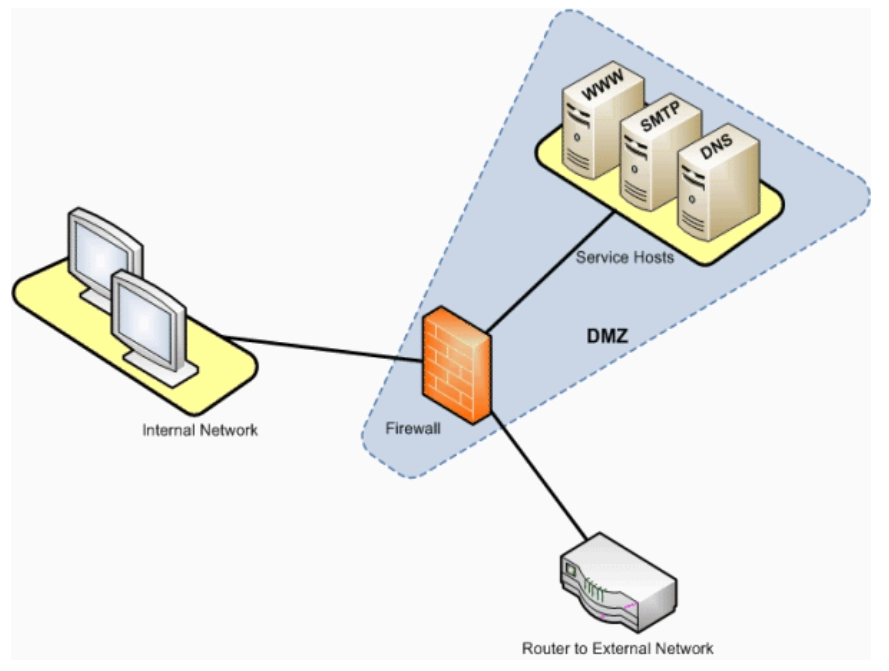
Source: SAP4
Why to use single firewall: A single firewall simplifies network architecture by consolidating traffic control, policy enforcement, and logging into one device. This reduces administrative complexity and lowers both capital and operational costs. It is best for smaller environments where there is no need for multi-layered perimeter defenses.
2. Dual firewall
This implementation creates a DMZ using two firewalls.
Figure: Illustration of dual firewall architecture
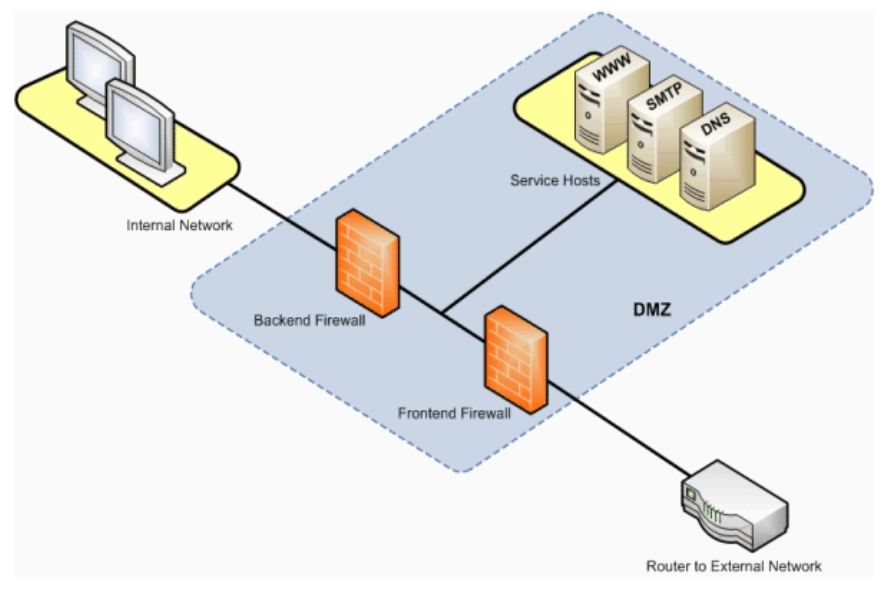
Source: SAP5
Why to use dual firewalls: Dual firewalls offer a more secure system. In some companies, the two firewalls are offered by separate providers. If an attacker can breach the first firewall, it may take longer to breach the second one if it is built by a different manufacturer, making it less likely to fall victim to the same vulnerabilities.
Benefits of Demilitarized Zone (DMZ)
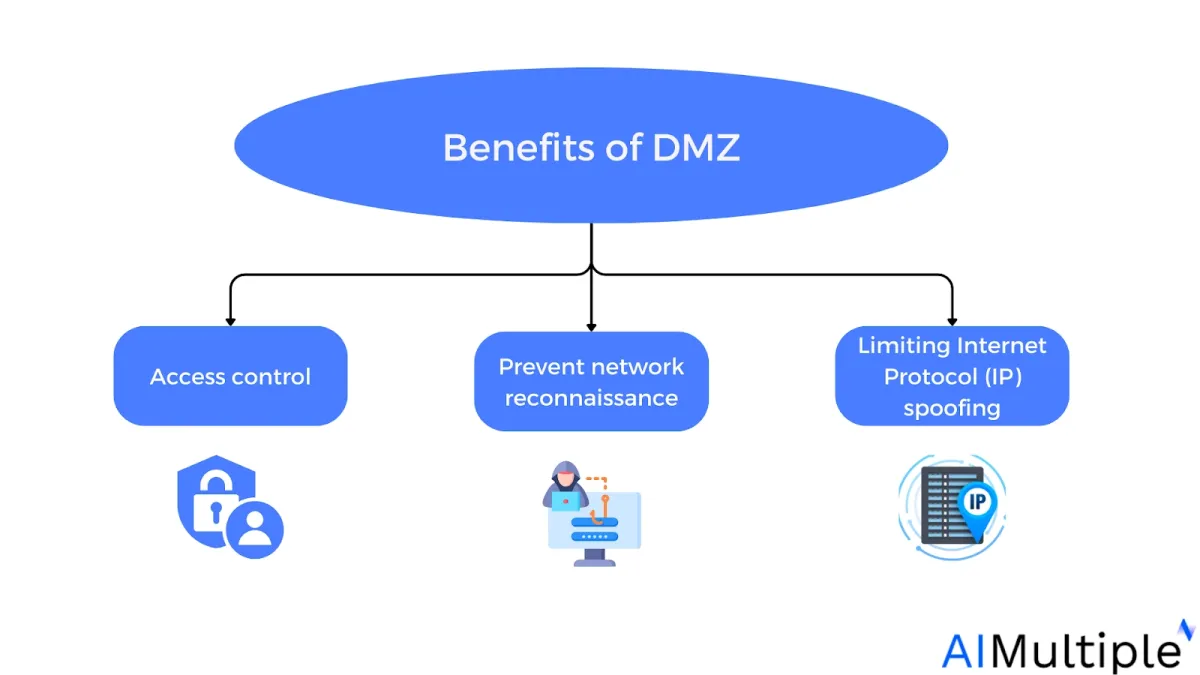
The primary value of a DMZ lies in its ability to provide public internet users with access to specific external-facing services, while serving as a protective barrier that shields the organization’s internal network.
This added layer of defense offers several key security benefits:
A DMZ network controls access to services accessible over the internet that are not within a company’s network perimeter. It also adds a layer of network segmentation, increasing the amount of barriers a user must overcome before getting admission to a company’s private network.
Prevent network reconnaissance:
A DMZ limits an attacker from assessing prospective targets on the network. Even if a machine in the DMZ is hacked, the internal firewall defends the private network by isolating it from the DMZ. This configuration makes external network exploits more difficult.
Limits Internet Protocol (IP) spoofing:
IP spoofing involves forging the source IP address of packets to gain unauthorized access. A DMZ helps detect and block spoofed traffic, especially when combined with additional security measures that validate IP authenticity, further protecting the internal network from impersonation attacks.
Applications of DMZs
1. Cloud services
Some cloud services employ a hybrid security strategy in which a DMZ is established between the company’s on-premises network and its logical network. This strategy is commonly employed when the company’s services run partially on-premises and partially over a logical network.
2. Home networks
A DMZ can also be useful for home networks that use LAN settings and broadband routers. Several household routers include DMZ options or DMZ host settings. These options enable users to connect only one device to the internet.
3. Industrial control systems (ICS)
DMZs may provide a solution to the security problems associated with ICS.
Most of the operational technology (OT) equipment that connects to the internet is not as well-designed for mitigating attacks as IT devices are. A DMZ can strengthen OT network segmentation, making it more difficult for malware, viruses, or other network threats.
4. Web and email hosting
Public-facing services—such as web servers, email servers, and DNS servers—are typically deployed within a DMZ to provide external users with access to essential resources while maintaining the security of the internal network.
5. Intrusion detection and prevention systems (IDS/IPS)
Some security architectures place IDS/IPS sensors in the DMZ to inspect incoming and outgoing traffic for malicious behavior before it reaches the internal network.
6. Partner and vendor access
Organizations that provide network access to third-party partners or vendors often use a DMZ to host shared services (e.g., APIs, SFTP portals). This limits the exposure of the internal network in case the external party’s access is compromised.
7. Remote access gateways
VPN concentrators, remote desktop gateways, or virtual desktop infrastructure (VDI) brokers are often deployed in a DMZ to allow secure remote access to internal systems without exposing them directly to the internet.
External Links
- 1. ResearchGate - Temporarily Unavailable.
- 2. ”Network Warrior“. (PDF). O’Reilly Media. May 2011. Retrieved February 6, 2024.
- 3. ”Network Warrior“. (PDF). O’Reilly Media. May 2011. Retrieved February 6, 2024.
- 4. SAP Help Portal | SAP Online Help.
- 5. SAP Help Portal | SAP Online Help.


Comments
Your email address will not be published. All fields are required.