Explore Research Studies
Analysis of Top 4 Open Source NGFWs Based on Features
Data breaches led to the exposure of 6M records in the first quarter of 2023, according to network security stats. Teams using NGFWs, AI-driven security, and automation are saving ~$2M more than those use the traditional tools.
Opcon Automation in: Pros, cons, features & 4 alternatives
In a survey, 82% of businesses plan to add or replace their workload automation and orchestration technologies. Some of the reasons behind such dissatisfaction associate with: OpCon Automation is one of the potential workload automation software that business leaders and IT teams might choose.
Top 7 Real-life Micro Segmentation Examples
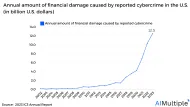
Source: IC3 Network security statistics show that the monetary damage caused by cybercrime reported to the U.S. increased by around 21% in 2023, reaching a historical high of $12.5 billion. Micro segmentation tools may assist companies in: See the top 7 real-life micro segmentation examples with stories from diverse industries: 1.
Top 4 Field Agent Competitors & Alternatives
Monitoring retailers across different countries can pose a challenge for manufacturers of CPGs (consumer packaged goods) and FMCGs. Planogram audit services or retail audit companies offer solutions to help overcome these challenges. Field Agent is a service provider specializing in retail monitoring services for consumer packaged goods (CPG) producers.
Top 7 Real-life Network Segmentation Use Cases
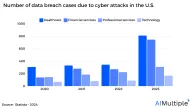
Network security statistics show that the total amount of data breaches has more than doubled in the last three years rising to 1,300+ cases from ~600. Network segmentation tools can help organizations build a finer-grained network to prevent breaches. Here are the top 7 real-life network segmentation use cases and examples: 1.
Top 10 Endpoint Detection & Response (EDR) Tools
Endpoint Detection and Response (EDR) solutions, also known as endpoint detection and threat response (EDTR), provide real-time monitoring, threat detection, and response capabilities at the endpoint level, enabling organizations to hunt for threats proactively. The EDR tools market is characterized by a multitude of vendors offering a variety of functionalities and features.
List of the best SOC (Security Operations Center) Tools
An effectively equipped SOC team holds significant importance in countering cybersecurity threats and promptly addressing security incidents. A Security Operations Center (SOC) team uses a range of security tools, methodologies, and protocols to identify and prevent security incidents.
Top 10 Text-to-Speech Software: Use Cases & Features
In 2024, the global text-to-speech (TTS) market was valued at $3.5 billion. It is expected to reach $28.52 billion by 2032, growing at a compound annual growth rate (CAGR) of 30%.This projected growth highlights the increasing role of artificial intelligence in advancing TTS technology.
DLP Review: Benchmark Testing of 6 DLP Products
Leveraging my 2 decades of experience as a cybersecurity practitioner, I selected top DLP software for securing sensitive information & complying with regulatory standards. I tested 6 of these DLP solutions over a month, focusing on key features like channel coverage, ease of deployment, and classification accuracy.
Top 5 NGFW Use Cases with Case Studies
The market for next-generation firewalls (NGFWs) is rapidly expanding, with an anticipated compound annual growth rate of ~11% between 2023 and 2028, increasing from $5 billion to $8.6 billion. As organizations seek advanced security solutions to combat evolving cyber threats, NGFWs are becoming essential.