Explore Research Studies
JDE Orchestrator in: Pros, Cons, Features & 3 Alternatives
82% of businesses plan to either replace their legacy IT automation tools or enhance them with new solutions for IT orchestration. JDE Orchestrator is an orchestration tool that can be deployed to streamline processes, integrate diverse systems, and improve operational efficiency. Yet, users complain about functionality customization, data management capability and upgrade time.
Discover 8 SAP BTP Generative AI Tools
70% of 500 top-tier IT leaders indicated that they plan to prioritize generative AI for their businesses in the next year according to generative AI stats. 80% of big tech firms have already invested in generative AI. SAP is expanding its generative AI capabilities through the SAP BTP platform to support enterprise use cases.
The Best Cyber Threat Intelligence Tools
Global cost of cybercrime is expected to reach $10.5 trillion annually by 2025, highlighting the need for stronger cybersecurity strategies.
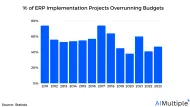
ERP Pricing: 5 Vendors, 5 Models & 6 Factors
ERPs are popular for providing end-to-end solutions, with the ERP market projected to reach ~$52bn in 2024. However, 47% of organizations faced cost overruns in their ERP implementations in 2023, often due to unclear pricing This article explores ERP pricing models, factors influencing costs, and the pricing structures of 5 vendors.
MFT Pricing: Comparison of Top 3 MFT Vendors' Pricing
Managed File Transfer (MFT) solutions vary widely in terms of pricing, depending on the features and deployment options you choose. Here’s a comparison of some leading MFT pricing: Understanding MFT Pricing Models MFT vendors typically employ different pricing approaches based on deployment requirements and organizational scale: MFT Pricing for different companies 1.
Discover Latest 6 SAP Datasphere AI Integrations
SAP Datasphere is AI tool that can help deliver meaningful data to the enterprises that struggle to utilize 60% and 73% of their data for analytics, as the latest big data statistics indicate.
Top 8 SIEM Use Cases and Real-life Examples
We previously explained open source & commercial SIEM tools, including how to select the best solution.

6 Data Security Posture Management (DSPM) Use Cases
Network security statistics show that the human factor accounts for ~80% of breaches. Protecting your organization’s data entails more than merely preventing the cyber attack vectors. It is also important to minimize the exposure of sensitive information within the company’s own network.
Top 10 ZTNA Solutions: Ratings, Size & Pricing
With around 22 million U.S. adults (~14% of the total employed population) working from home full-time, secure remote access is critical. Zero-trust network access (ZTNA) solutions address this need by ensuring only authenticated and authorized users access sensitive resources.
Top 10 Open Source Network Security Software
Network security statistics show that data breaches impacted ~350 million people in the U.S. Open source network security software can prevent unauthorized access to network services and identify the most common cyber attack vectors. These software continuously monitor a network for malicious activity and take action to prevent it.