Data from network security statistics reveals that the cost of an average data breach in the last year reached a record-breaking $4 million. To safeguard their data, businesses are leveraging solutions such as data loss prevention (DLP) software.
Understanding the impact of DLP through data-backed insights can empower security leaders to address vulnerabilities and implement effective measures. We collected 15 important statistics on DLP:
State of data security
1. Data breaches impact: In 2023, there were 3,205 reported instances of data compromises in the United States. During the same period, data compromises impacted over 353 million people, encompassing data breaches, leaks, and exposures. Despite these being distinct types of incidents, they share a common outcome: sensitive data is accessed by an unauthorized entity.1
Figure 1. Annual number of data breaches & individuals impacted
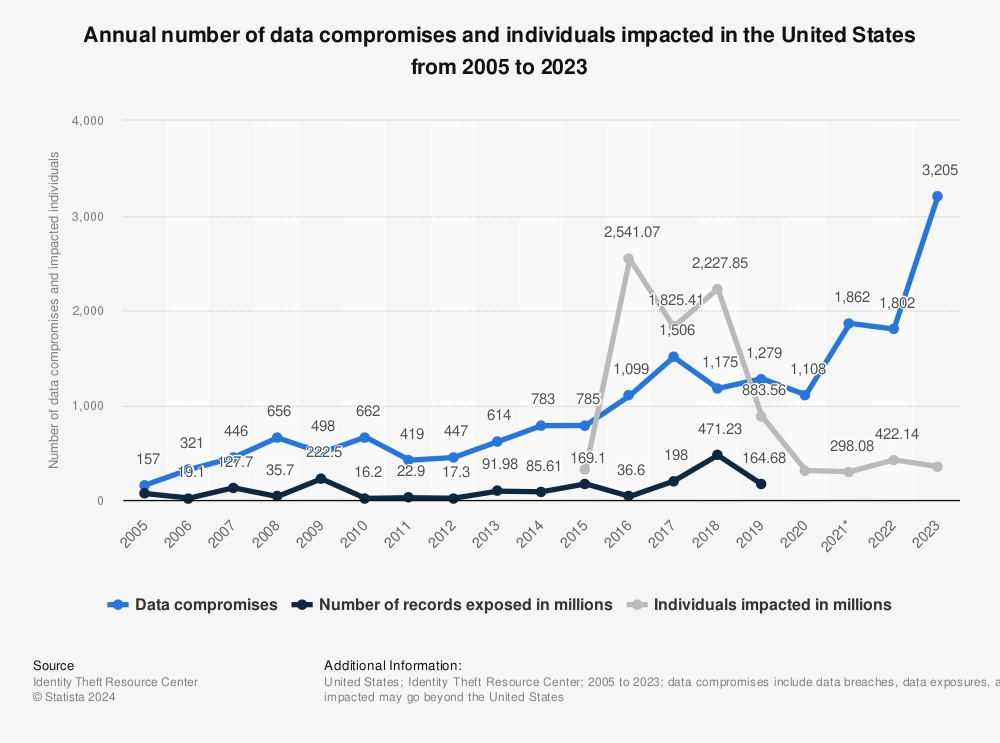
Source: Statista2
2. Data breach causes: In 2022, a global survey of IT and cybersecurity experts from various organizations revealed that the primary mistake leading to cyber incidents was employees’ weak password practices. The second most cited issue, according to 78 percent of the participants, was the improper use of personal email.3
3. Company view of security breaches: In 2023, over three-quarters of respondents from the Americas indicated that their company viewed security breaches and data leaks as a significant threat. This proportion was somewhat smaller for respondents from the Asia-Pacific and EMEA regions.4
Figure 2. Threat of data leaks to global organizations, by region
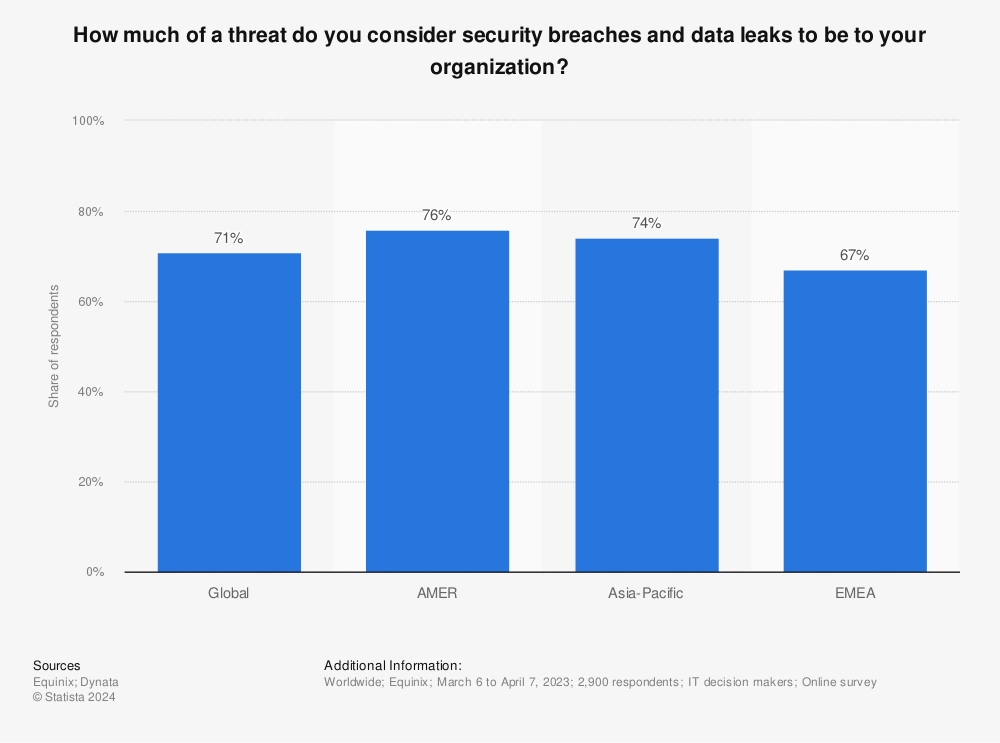
Source: Statista5
4. Habits of remotely working employees: In 2020, 49 percent of respondents from the United States reported using personal devices, such as laptops, tablets, or smartphones, to access company applications and networks. This kind of behaviour makes companies more vulnerable to cyber threats, as inadequate security habits, such as recycling passwords, can increase an enterprise’s risk of a breach.6
5. Ransomware attack downtime: Ransomware attacks result in an average of 16.2 days of downtime for affected businesses, emphasizing the disruptive nature of such attacks on operational continuity.7
DLP market
6. DLP market projections: The DLP (Data Loss Prevention) market is anticipated to expand quickly in the near future, partly due to growing public awareness of data privacy and security. Revenue in the DLP market is expected to rise from $1.24 billion in 2019 to $3.5 billion by 2025.8
Figure 3. DLP market revenue forecast worldwide
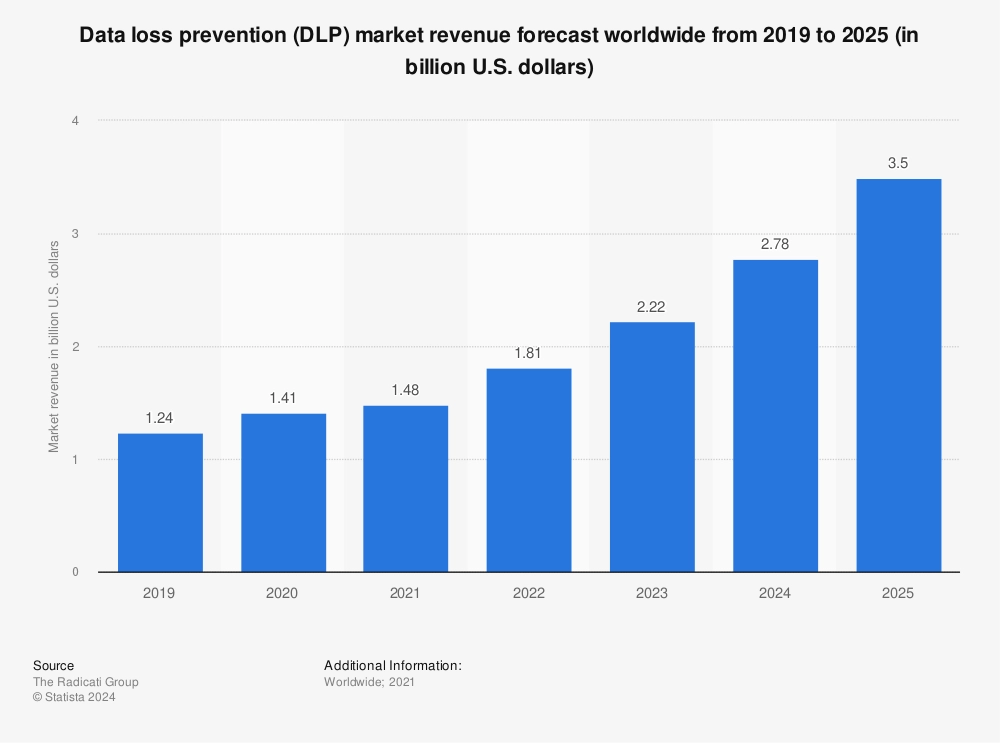
Source: Statista9
Data protection technology
7. Data replication & protection: The data replication and protection software market is forecasted to reach around $14 billion in 2027, up from nearly $12 billion in 2022.10
8. Security application in IT: A 2021 worldwide survey revealed that IT professionals across different organizations do not significantly differentiate in the protection frequency of “high priority” and “normal” applications. Roughly 20% of respondents continuously apply security processes such as backup and replication to high-priority applications, while only 12% do the same for other applications.11
Figure 4. Frequency of data loss protection methods worldwide
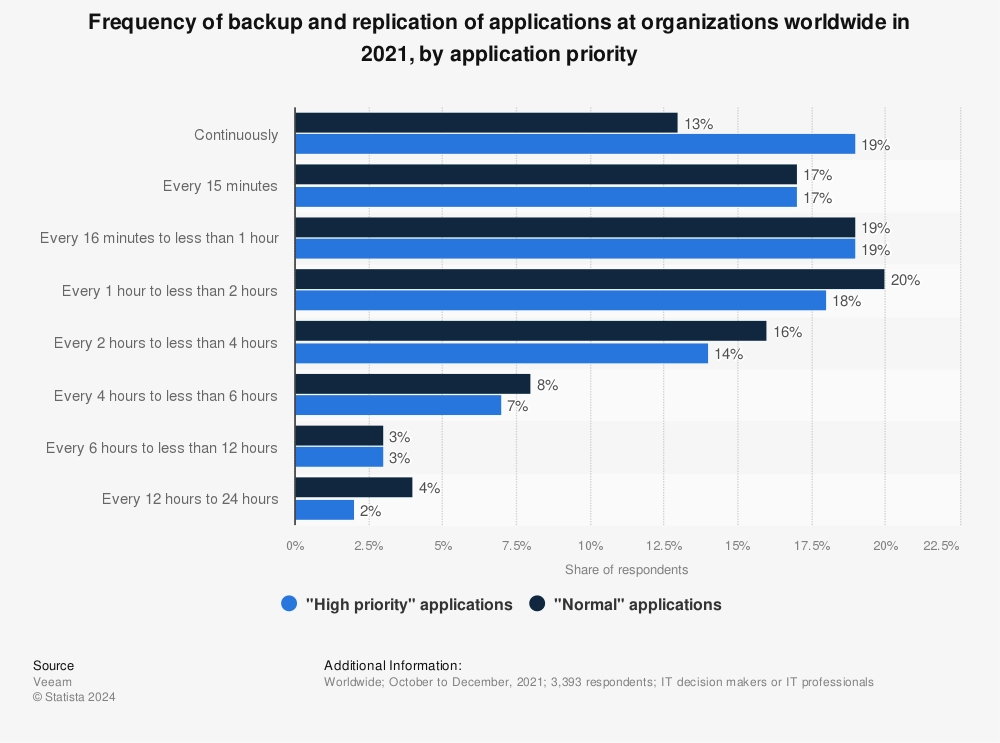
Source: Statista12
9. Cloud-sensitive data protection: According to a SANS 2022 cloud security survey, the following are the top implementations of security controls for cloud-sensitive data protection.13
Figure 5. Security controls for cloud-sensitive data protection
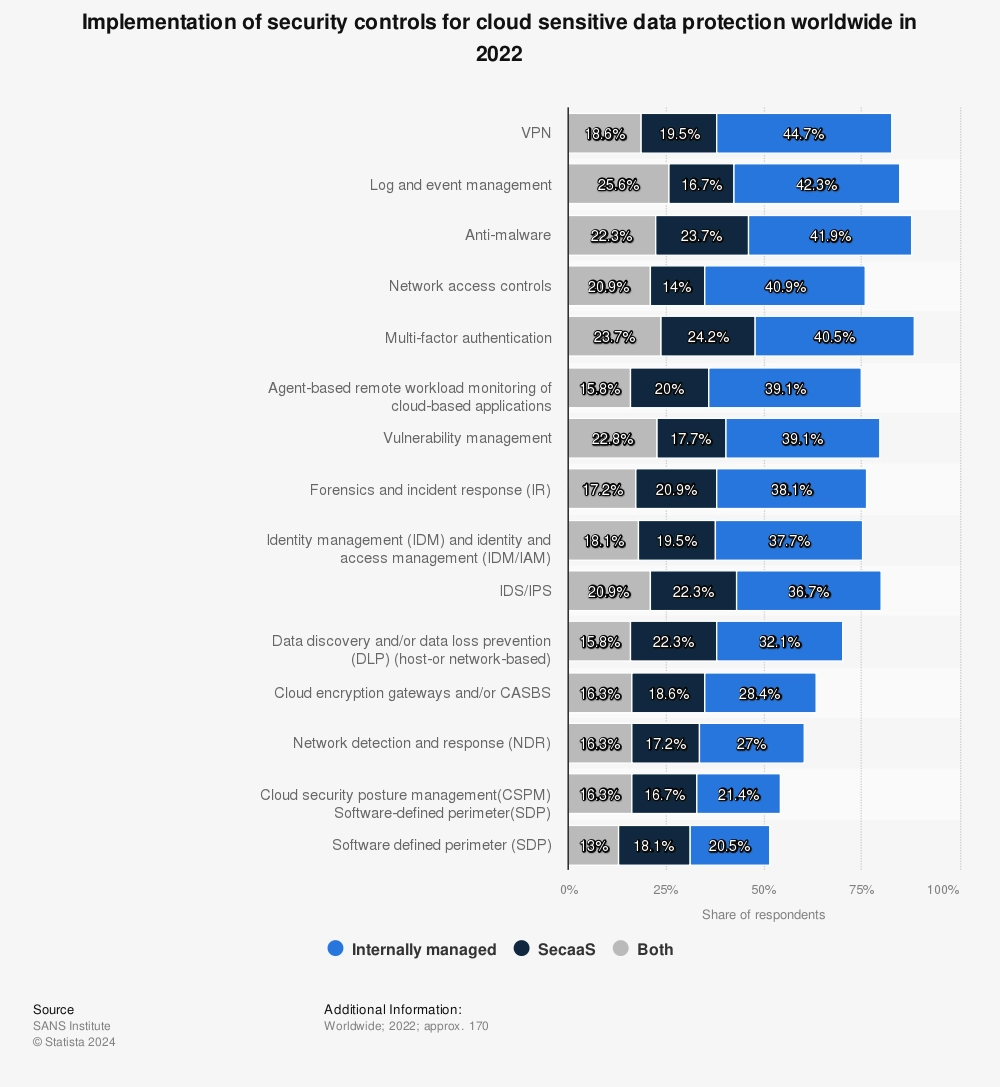
Source: Statista14
Data security projections
10. Endpoint as a major threat vector: In 2024, it’s anticipated that the endpoint will become the primary threat vector for data loss, with more than 70% of data loss incidents originating from endpoints, shifting focus from cloud security back to endpoint security.15
11. Time to identify and contain breaches: In 2023, it took an average of 204 days to detect data breaches, a slight improvement over 2022’s 207 days. However, containment times increased slightly from 70 days in 2022 to 73 days in 2023.16
Figure 6. Average time to detect and contain data breaches
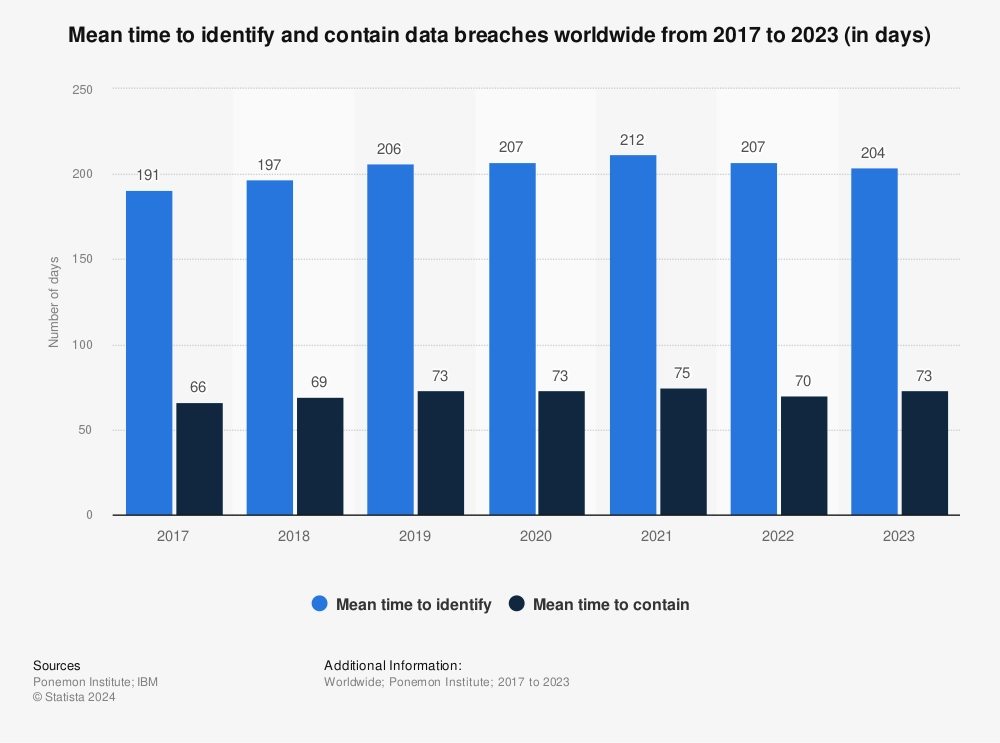
12. Information security spending worldwide: Global expenditure on information security has been on the rise from 2017 through 2023, climbing from just below $100 billion in 2017 to nearly $200 billion in 2023.
The majority of this spending has been focused on security services, infrastructure protection, and network security equipment. By 2024, it is anticipated that spending on security services will approach $90 billion.17
Figure 7. Spending on global information security

Source: Gartner, Statista18
Key DLP insights
13. Insider threat dynamics: Insider threats account for nearly 35% of data breaches, either through malicious intent or inadvertent errors. These incidents often involve employees unintentionally sharing sensitive information or failing to adhere to security protocols.
14. Role of AI in DLP: AI-powered DLP solutions are gaining traction for their ability to detect anomalies, classify sensitive data, and provide predictive analytics for threat mitigation. Businesses implementing these tools report a 35% reduction in data breach costs on average.
15. Rising cost of non-compliance: Failure to implement adequate data protection measures can lead to significant financial penalties. In 2023, global regulatory fines for data breaches and non-compliance with data protection laws surpassed $4 billion, with GDPR violations alone accounting for over $1.5 billion.
Future of DLP solutions
- Adoption of cloud-native DLP tools:
By 2025, 90% of organizations are expected to rely on cloud infrastructure, making DLP tools optimized for cloud environments a pivotal role in securing hybrid workforces and distributed data systems. - Expansion of regulatory frameworks:
As governments implement stringent data protection laws such as GDPR and CCPA, organizations must ensure compliance through detailed data classification and governance measures. Non-compliance penalties, which exceeded $1.4 billion globally in 2023, underscore the financial implications of inadequate DLP strategies. - Comprehensive endpoint protection:
In response to endpoint vulnerabilities, organizations are adopting unified endpoint management (UEM) systems that integrate DLP, device management, and user activity monitoring into a cohesive framework. - DLP automation trends:
Automation is set to revolutionize DLP, enabling real-time responses to threats and reducing the manual effort involved in data classification and monitoring. - Behavioral analytics integration:
Behavioral analytics is emerging as a key feature in advanced DLP solutions, helping organizations identify unusual patterns indicative of potential insider threats or compromised credentials.
Why are DLP solutions critical?
As data breaches and cyber threats continue to evolve, organizations must prioritize robust DLP solutions. These tools help mitigate risk, safeguard sensitive data, and ensure compliance with regulatory standards. With the DLP market set for significant growth, businesses are recognizing the necessity of investing in advanced data protection measures.
FAQs for DLP statistics
-
What does DLP mean?
DLP stands for Data Loss Prevention. It is a strategy and set of tools used to ensure that sensitive data, including personally identifiable information and financial information, is not lost, misused, or accessed by unauthorized users. DLP helps organizations protect critical data by monitoring, detecting, and blocking data leaks through control of data access and data movement within corporate networks. This protection extends to preventing accidental data loss, securing data against insider threats and external threats, and ensuring compliance with regulatory standards.
-
What is data loss prevention analytics?
DLP (Data Loss Prevention) Analytics involves analyzing and managing data to prevent leaks, breaches, and unauthorized access.
This practice focuses on securing data, particularly sensitive data, by monitoring data access and movement across a company’s network and storage solutions. DLP solutions are essential for protecting data such as personally identifiable information and financial records from insider threats, external threats, and accidental losses due to human error or computer viruses.
Key aspects of data loss prevention include data visibility, data protection, and implementing strategies to safeguard business-critical data, ensuring compliance with regulatory standards, and minimizing data loss risks.
-
What is a DLP endpoint?
DLP endpoint refers to the component of a data loss prevention strategy that focuses on securing sensitive data at endpoint devices such as computers, mobile devices, and servers within a private computer network. It involves implementing data loss prevention policies and tools to monitor, control, and protect data access and movement directly on these endpoints.
-
What is DLP risk assessment?
DLP risk assessment is a vital part of any effective cybersecurity strategy, as it identifies and evaluates potential risks related to the management, access, and movement of sensitive data within an organization. This assessment involves a thorough analysis of data storage, how the data is accessed, and how it is transmitted across both physical and digital platforms, pinpointing vulnerabilities that could lead to data leaks, unauthorized access, or other threats. Utilizing data loss prevention tools to monitor data streams and filter data files enables organizations to safeguard sensitive information, such as personally identifiable information and intellectual property, against insider threats, external threats, and accidental data loss.
A robust DLP strategy emphasizes data protection by implementing comprehensive data loss prevention measures and crafting controls specifically tailored to the organization’s unique risk profile. This includes extending data identification and encompassing both structured and unstructured data, and enhancing data visibility across all endpoints, including cloud-based systems. DLP solutions play a crucial role in enforcing compliance regulations and adhering to corporate policies by managing data access and data movement through the use of technologies such as multi-factor authentication and robust access control systems.
Overall, DLP risk assessment is integral to detecting potential security incidents early, effectively preventing data leaks, and securing business-critical and proprietary data.
Further reading
- Most Common Cyber Attack Vectors
- Top 12 LLM DLP Best Practices
- Top 15 AI DLP Best Practices with Case Studies
External resources
- 1. 2023-Annual-Data-Breach-Report. ITRC.
- 2. Number of data breaches and victims U.S. 2024| Statista. Statista
- 3. The State of Email Security 2023, page 16. Mimecast.
- 4. Threat of security breaches and data leaks worldwide 2023| Statista. Statista
- 5. Threat of security breaches and data leaks worldwide 2023| Statista. Statista
- 6. Remote work employee security habits UK & U.S. 2020| Statista. Statista
- 7. Business Data loss and Disaster Recovery Statistics.
- 8. Data loss prevention market revenue worldwide 2025| Statista. Statista
- 9. Data loss prevention market revenue worldwide 2025| Statista. Statista
- 10. Worldwide Data Replication and Protection Software Forecast, 2023–2027: Steady Demand. IDC.
- 11. 2024 Data Protection Trends Report - Veeam.
- 12. Frequency of data loss protection methods worldwide 2021| Statista. Statista
- 13. 2022 Cloud Security Survey, page 8. SANS.
- 14. Security controls for cloud data protection worldwide 2022| Statista. Statista
- 15. If 70% of Data Loss Incidents Occur at the Endpoint, Why Would Your DLP Be Anywhere Else? | Endpoint Protector. Endpoint Protector Blog
- 16. Time to identify and contain data breaches global 2024| Statista. Statista
- 17. Gartner Forecasts Global Security and Risk Management Spending to Grow 14% in 2024.
- 18. Global information security spending by segment 2024| Statista. Statista

Comments
Your email address will not be published. All fields are required.