An effectively equipped SOC team holds significant importance in countering cybersecurity threats and promptly addressing security incidents. A Security Operations Center (SOC) team uses a range of security tools, methodologies, and protocols to identify and prevent security incidents. This article offers insights into leading SOC tools that enable security teams to optimize operations and protect vital assets with efficiency.
Top 7 Security Operations Center tools
Vendors are arranged alphabetically, with the exception of products from the sponsors of the article, which are accompanied by links to their websites.
| Vendors | Solution type | Operating system | Deployment | Starting price | Free trial |
|---|---|---|---|---|---|
| Invicti | Vulnerability scanner | Windows, macOS, and Linux | Cloud & On-demand Fire-and-forget On-premises | Custom | ✅ |
| Heimdal XDR | XDR | Windows, macOS, and Linux | On-premises Self-hosted | Custom | ✅ |
| LogRhythm | SIEM | Windows, macOS, UNIX and Linux | On-premises & Cloud Hybrid | Custom | N/A |
| Rapid7 MSS | XDR and SIEM | Windows, macOS, UNIX and Linux | On-premises & Cloud Hybrid | Custom | 30-day |
| SolarWinds Security Event Manager | SIEM | HPUX, Linux, macOS, IBM AIX, and Windows | On-premises Self-hosted | 2.44€ | 30-day |
| Splunk | SIEM | Windows, macOS, UNIX and Linux | On-premises & Cloud Hybrid | Custom | 14-day |
| Sprinto | TIP | N/A | Hybrid Virtual appliance On-premises & Cloud | Custom | N/A |
What is a SOC tool?
A SOC tool, also known as a Security Operations Center tool, is software that assists security teams in identifying, examining, and addressing cybersecurity threats and incidents. These tools commonly interface with various technologies such as firewalls, IPS tools , and endpoint security solutions.
SOC tools often include features like security information and event management (SIEM), threat intelligence integration, vulnerability management and incident response automation.
1. Invicti

Invicti, previously named Netsparker, provides a web application security scanning tool that can be useful for Security Operations Center (SOC) teams in identifying vulnerabilities like SQL injection and cross-site scripting (XSS). Invicti can integrate with SIEM solutions to provide alerts and notifications regarding identified vulnerabilities. It combines Dynamic Application Security Testing (DAST) and Interactive Application Security Testing (IAST) techniques to detect security vulnerabilities.
Main features:
- Proof-based vulnerability scanning: It verifies vulnerabilities by exploiting them in a non-destructive manner, reducing the occurrence of false positives and negatives.
- Continuous Integration (CI): Integrates with CI systems like Jenkins, Travis CI, and CircleCI, facilitating the integration of automated security checks within the CI workflow.
- Various deployment options: Suitable for both on-premises and cloud installations. Organizations can also opt for a hybrid deployment model.
2. Sprinto

Sprinto is a security compliance automation platform, providing capabilities like device supervision, alert generation, and gathering of evidence. It accommodates both on-premise and cloud installations.
Main features:
- Vulnerability and incident management: Sprinto features its own integrated incident management system and seamlessly connects with a range of other incident management tools to ensure ongoing monitoring of deviations. Incident management tools enable security teams to detect weaknesses in systems, networks, applications, or processes. Following identification, vulnerabilities are classified according to their severity, potential for exploitation, and potential impact.
- Role-based access controls: Sprinto provides access control through role-based and ticket-based mechanisms, enabling the monitoring of access through both automated and manual workflow validations.
- Tiered remediation: Enables tiered remediation depending on the status of controls, whether they pass, fail, or are critical.
- Baked in MDM (mobile device management): Sprinto features an integrated mobile device management (MDM) tool called Dr. Sprinto, and it also seamlessly integrates with multiple other MDM solutions for endpoint monitoring. Dr. Sprinto conducts automated compliance checks on devices, triggering alerts automatically if any deviations are detected.
3. Splunk
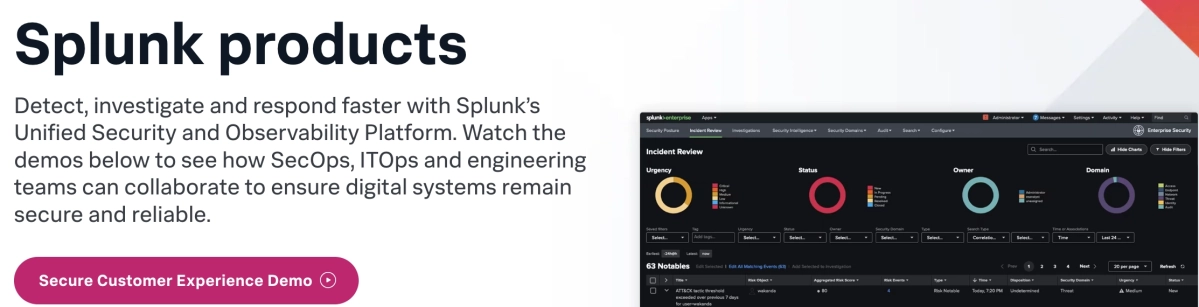
Splunk is an unified solution for detecting, investigating, and responding to threats, supporting Security Operations Center (SOC) activities. It caters to various deployment preferences including on-premises, cloud, and hybrid setups. Among its offerings are:
- Splunk Enterprise Security: Provides a security information and event management (SIEM) solution along with security analytics tailored for SOC needs. It enables the collection of data from diverse sources such as websites, servers, databases, and operating systems. Splunk Enterprise can gather data from any machine within your network, irrespective of whether the data originates locally, remotely, or in the cloud, as long as the machine generating the data is connected to your network. Following data collection, it indexes, segments, and stores the information efficiently.
- Splunk Attack Analyzer: Is a cloud-based application designed to analyze attack chains, identifying threats like credential phishing and malware. It produces actionable insights and minimizes the need for repetitive manual tasks often involved in threat investigation.
- Splunk SOAR: Splunk provides its Security Orchestration, Automation, and Response (SOAR) both as a cloud-based service and as on-premises solutions. With Splunk SOAR (Cloud), security events can be ingested from the Splunk Cloud Platform or various other products like firewalls. These events are then analyzed and tracked within a unified interface.
Main features:
- Data ingestion: Splunk facilitates the intake of data in real-time or batches from diverse sources such as logs, metrics, and events.
- Search: Splunk empowers users to explore, analyze, and visualize extensive data sets in real-time, enabling spontaneous querying and exploration.
- Extensibility: The platform offers APIs and SDKs for custom integrations and extensions, enhancing its adaptability and flexibility.
4. LogRhythm
LogRhythm specializes in cybersecurity solutions, including Security Information and Event Management (SIEM), User and Entity Behavior Analytics (UEBA), and Security Orchestration, Automation, and Response (SOAR). It offers an integrated SOAR solution and supports third-party integrations with both on-premises and cloud-based SIEM products.
- LogRhythm SIEM: This is a locally-hosted SIEM platform equipped with SmartResponse, serving as an embedded SOAR solution. It automates the detection, investigation, and response to cyber threats, reducing manual workload.
- LogRhythm Axon: As a cloud-native SIEM platform, LogRhythm Axon seamlessly integrates with third-party SOAR vendors, enhancing its capabilities. Axon is supported on the Google Chrome, Mozilla Firefox, and Microsoft Edge browsers.
Main features:
- User and entity behavior analytics (UEBA): Monitors user actions, utilizing both deterministic and anomaly analytics to identify various security risks, including both known and unknown threats.
- Various deployment options: LogRhythm offers cloud-based solutions, software package and network appliance deployment options.
5. Rapid7
Rapid7 provides managed security services equipped with its SIEM and XDR platform for SOC teams. These services include:
- Managed Detection and Response (MDR): Offers active monitoring to detect and respond to live threats.
- Managed Vulnerability Management (MVM): Handles scan operations to offer actionable suggestions, prioritizing risk mitigation across network environments.
- Managed Application Security Testing: Offers insights into vulnerabilities within web application layer in real-time, aiding in risk mitigation during the development phase.
Main features:
- Log data collection: InsightIDR converts raw data into JSON format to augment user behavior and potential malicious activities with additional context.
- Attack Behavior Analytics (ABA): Utilizes Attack Behavior Analytics (ABA), a repository of documented hacker attack methods, to automatically compare and analyze your data in real-time.
6. SolarWinds Security Event Manager
SolarWinds Security Event Manager is an on-premise SIEM offering that incorporates a log manager and ensures compliance with regulations such as HIPAA, PCI DSS, and SOX. SolarWinds extends its SIEM capabilities by integrating a threat intelligence feed, aggregating threat detection insights from all SolarWinds clients. This combination of a threat intelligence feed, log management, and threat detection capabilities enhances its overall security posture. SolarWinds Security Event Manager (SEM) is deployed on-premises or in a self-hosted environment, but does not offer a Software as a Service (SaaS) version.
Main features:
- Log management: Collect log data from various origins, extract their information, and standardize it into a unified, understandable format, establishing a centralized repository.
- Active response: It is a SEM action triggered automatically in response to suspicious activities. Active response actions include functionalities such as the block IP, disable networking, and log off user actions.
- Integrated threat intelligence: SolarWinds’ SEM incorporates a built-in threat intelligence feed, offering behavioral monitoring capabilities to detect behaviors associated with known malicious actors.
7. Heimdal XDR

Heimdal Extended Detection & Response (XDR) leverages advanced analytics, artificial intelligence (AI), machine learning (ML), and behavioral analysis to address security threats. XDR solution is equipped with Heimdal’s Threat-Hunting and Action Center.
Main features:
- Sandbox testing: It monitors activities like changes to the file system, and network interactions. The SOC software analyzes the file or program’s conduct in real-time to detect potential malicious behavior, cross-referencing it with known attack patterns or behavioral anomalies.
- User and entity behavior analytics: The system distinguishes individual user accounts, external sources, and endpoints, documenting their typical activities over time. When there’s a deviation, such as a user behaving differently or unusual activity from an endpoint, it flags a security event.
Types of tools and technologies used in SOCs
SOC tools can be categorized based on their main functionalities:
- SIEM tools: SIEM is a collection of tools and services that merge two distinct technologies: Security Information Management (SIM) and Security Event Management (SEM). SIM focuses on data collection from log files to analyze and report on security threats and incidents, while SEM involves real-time system monitoring, alerting network administrators about potential threats.
- EDR (Endpoint Detection and Response) tools: Endpoint detection and response tool is a cybersecurity technology aimed at monitoring and safeguarding endpoint devices like workstations, servers, laptops, and mobile devices from malicious activities. They collect and analyze security related information. EDR tools employ diverse detection methods such as signature-based detection, behavioral analysis, anomaly detection, and indicators of compromise (IOCs) to identify known and unknown threats aimed at endpoints.
- Network traffic analysis tools: Network traffic analysis tools observe and evaluate the traffic flowing through a network, capturing and examining network packets as they transit through network interfaces. These packets carry details regarding device communication, such as source and destination IP addresses, protocols utilized, and packet dimensions. Following capture, these tools perform deep packet inspection to analyze their contents.Their aim is to identify irregularities, intrusions, and potential security risks.
- UEBA (User and Entity Behavior Analytics) tools: UEBA tools leverage behavioral analytics, machine learning algorithms, and automation to detect security threats or attacks. Within security operations centers (SOCs), UEBA is employed to ingest and analyze high volume of data from diverse sources, establishing a baseline understanding of the typical behavior of privileged users and entities.
- Vulnerability management solutions: Vulnerability management solutions enable organizations to conduct scans on their network infrastructure, including systems and applications, including devices like routers, switches, and firewalls. After detecting vulnerabilities, these solutions categorize them according to severity and allocate risk scores to prioritize remediation actions based on the associated level of risk.
- Threat intelligence platforms: Threat intelligence platforms (TIPs) analyze both external threat feeds and internal log files to provide contextualized intelligence aimed at enhancing an organization’s security stance. These platforms gather information from various origins, including open-source intelligence (OSINT), commercial threat feeds, and internal security telemetry. The collected data undergoes normalization and enrichment processes to uncover emerging threats, trends, and patterns.
- Incident response orchestration platforms: Incident response orchestration is a key component within the security operations center (SOC), automating the management and response to security incidents. These platforms empower SOC teams to automate routine response tasks, such as isolating compromised endpoints, blocking malicious IPs, quarantining suspicious files, and updating firewall rules.
- Extended detection and response (XDR) tools: XDR solutions integrate data from various origins such as endpoints, networks, email, cloud services, and applications. Through the analysis of behavioral patterns, unusual activities, and recognized indicators of compromise (IOCs), XDR platforms detect both known and unknown threats.
If you have questions or need help in finding vendors, reach out:

Comments
Your email address will not be published. All fields are required.