Historically, companies handled their security workload with manual security processes or within proprietary code, causing challenges such as likelihood of human error, and scalability issues.
SOAR software helps organizations define incident analysis and automation methods. This enables triage utilizing a combination of human and machine power and contributes to the prioritization of standardized incident response operations. In this article, I have outlined the most common SOAR use cases:
1. Phishing detection and response
Problem: Analysts face bottlenecks in manually handling phishing alerts, largely due to the high volume of false positives and the repetitive nature of triage actions.
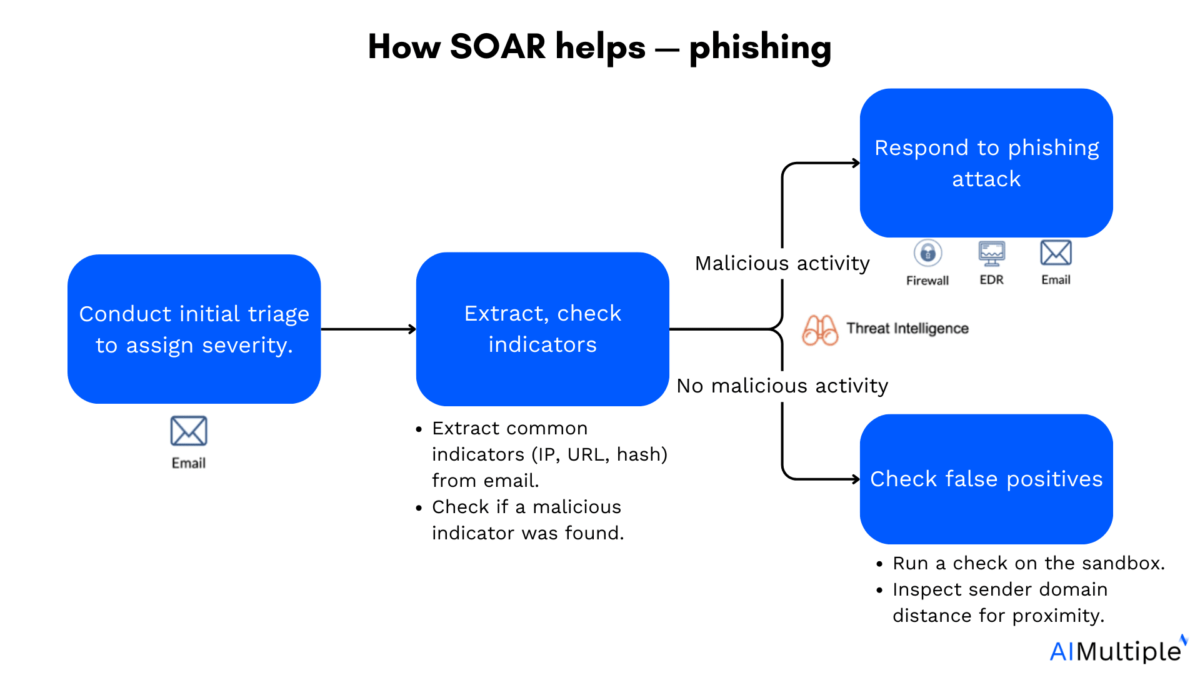
How SOAR helps identify and responding phishing attacks:
- Triage phase: SOAR receives phishing alerts and automatically sorts them based on severity, source, and risk level
- Indicator extraction and validation: Key indicators (such as URLs, IP addresses, and file hashes) are extracted from the phishing file
- Malicious or not:
- If malicious activity is detected, the playbook triggers an active response. This could involve blocking the sender, isolating endpoints, or deleting the malicious file.
- If no clear malicious indicators are found, the system proceeds to validate the alert further to rule out false positives.
- False positive analysis:
- The malicious file is run in a sandbox to analyze how the malware operates.
- The sender’s domain is analyzed for similarity to trusted domains.
Video: Real-life demonstration —phishing playbook demo
Source: Palo Alto Networks1
Real-life example: Zensar’s Cybersecurity Team uses SOAR for faster email phishing attacks & incident response. Technologies used by Zensar:
- Codeless playbooks
- +200 integrations and thousands of automated actions integrated in SOAR
- Email threat intelligence2
2. Endpoint detection and response (EDR)
Problem: Although EDR tools help detect suspicious endpoint activity, they often generate a high volume of alerts—many of which may be false positives.
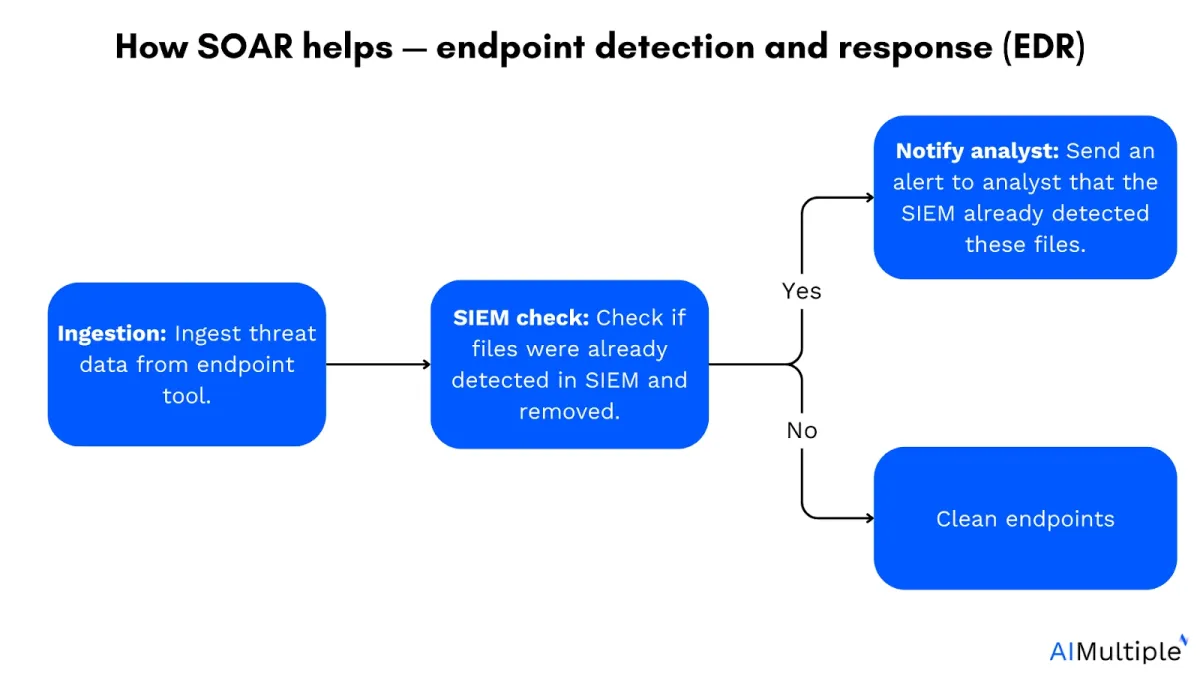
How SOAR helps endpoint detection and protection:
SOAR tools streamline EDR activities by automatically investigating, and responding to alerts, while filtering out non-threats to reduce analyst workload.
- Ingestion of endpoint data: SOAR systems ingest data from endpoint detection tools (like antivirus or EDR) to monitor real-time activity and identify potential threats.
- SIEM check: Check to see if any files were previously identified in SIEM.
- Notification to analysts: If a potential threat is detected, SOAR alerts security analysts, providing them with a detailed overview, including context and the severity of the threat.
- Automated response and endpoint cleaning: If no threat is confirmed (false positive), SOAR can automatically clean and restore the endpoint, removing any suspicious files.
3. Detecting suspicious user login from IP address locations
Problem: Suspicious user logins are difficult to identify due to the following reasons:
- User behavior is complex and variable
- Companies have multiple sources of geographical locations and cloud users to track
- Monitoring suspicious logins is manual and repetitive
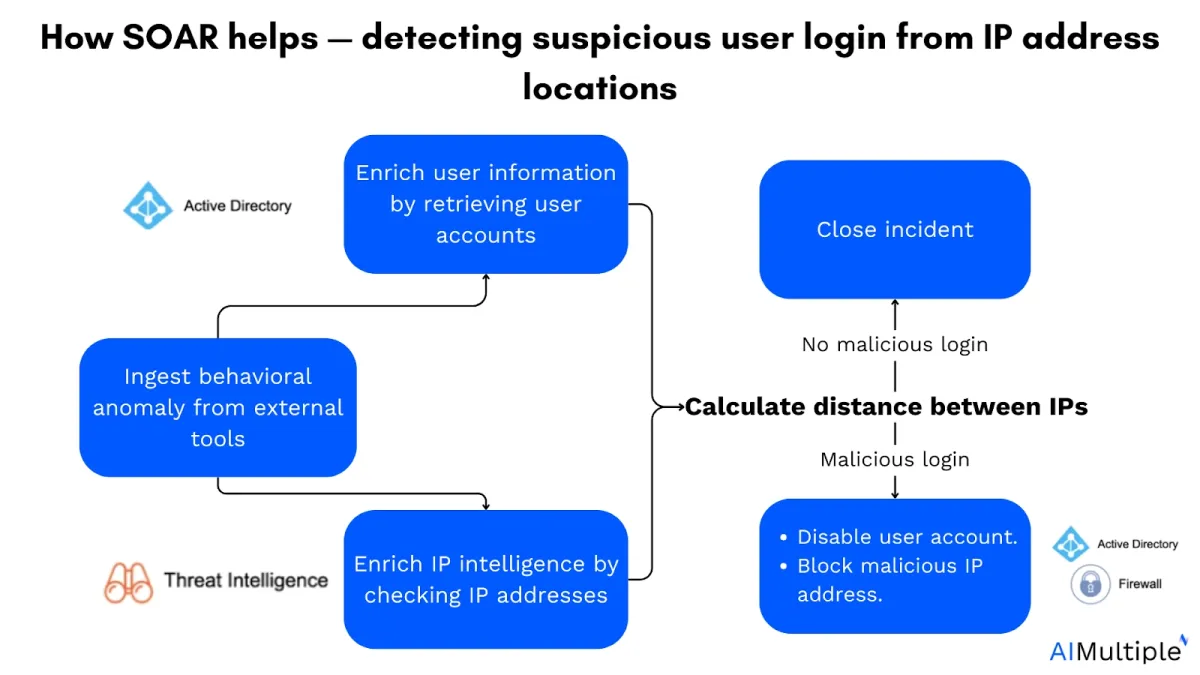
How SOAR helps detect suspicious user logins:
- Ingest behavioral anomaly: SOAR collects login data from external tools (e.g. SIEMs or authentication systems) to identify unusual login anomalies.
- Enrich user information: SOAR retrieves detailed user account information (e.g. past login history, role, permissions) to help assess whether the login behavior is legitimate.
- Enrich IP intelligence: SOAR cross-references IP addresses associated with the login attempt with threat intelligence databases to check for known malicious IP addresses.
- Determine threat status: Based on user behavior and IP intelligence, SOAR automatically decides whether the login attempt is likely malicious or safe.
- Automated response – close or act:
- No threat: If no malicious activity is detected, SOAR can automatically close the security incidents.
- Detected threat: If malicious activity is confirmed, SOAR takes automated actions, such as blocking the malicious IP address.
Video: IP address investigation with SOAR
Source: Palo Alto Networks3
4. Zero day threat response
Problem: Zero-day threats are cyberattacks that exploit unknown security flaws before a fix exists. Since antivirus tools don’t detect them, they often bypass traditional defenses.
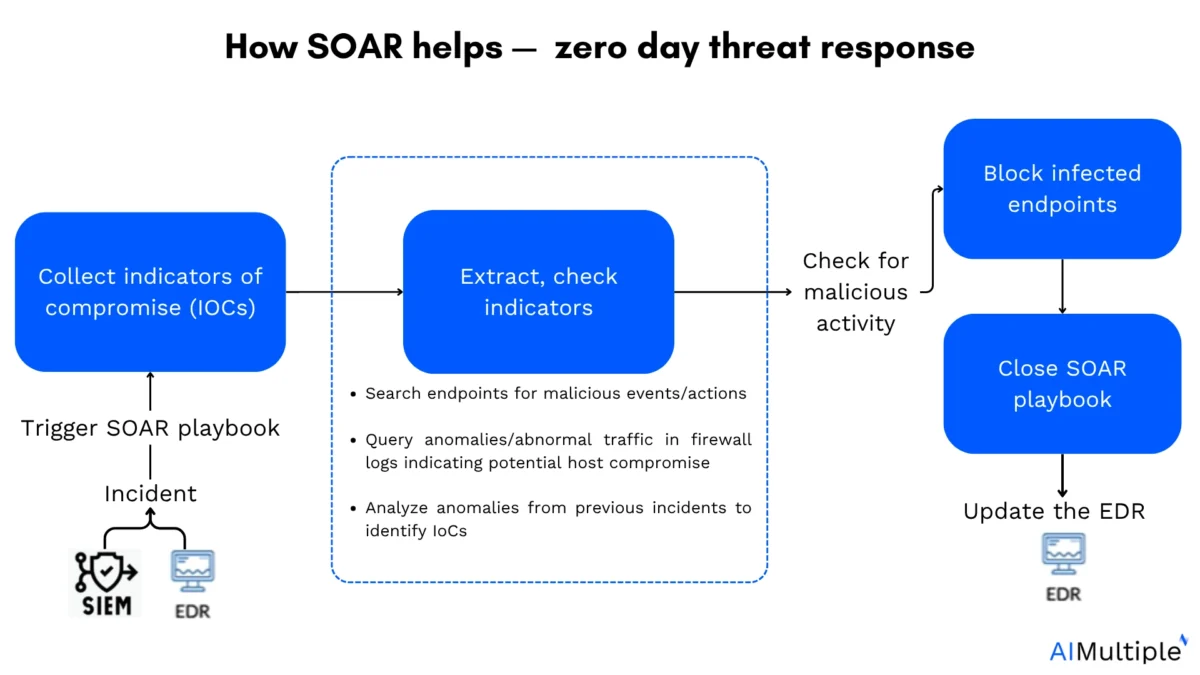
How SOAR helps respond to zero day threats:
When a SIEM or EDR flags suspicious behavior resembling a zero-day exploit, SOAR automatically:
- Collect indicators (IOCs) and files: Pull threat artifacts such as file hashes, malicious URLs, IP addresses.
- Extract, check for indicators:
- Search endpoint logs for malicious hashes: Analyze EDR logs and other endpoint telemetry for evidence of the identified hashes being executed or downloaded on other machines.
- Query firewall logs for compromised hosts: Examine network logs for traffic to or from known malicious IPs/domains or suspicious lateral movement.
- Link to previous incidents: Cross-reference existing incident records to identify similar TTPs (tactics, techniques, and procedures) from past events.
- Block infected endpoints: Deploy blocking rules across security devices (e.g., firewalls, web gateways, email filters)
- Close playbook: Update and sync to EDR by sending the updated rules or IOCs back into the EDR platform.
5. Vulnerability management
Problem: Manual, time-consuming vulnerability tests that need to be performed regularly. This results in:
- Difficult data collection related to vulnerabilities
- False positives on vulnerabilities.
- Lack of network visibility (e.g. unmanaged assets)
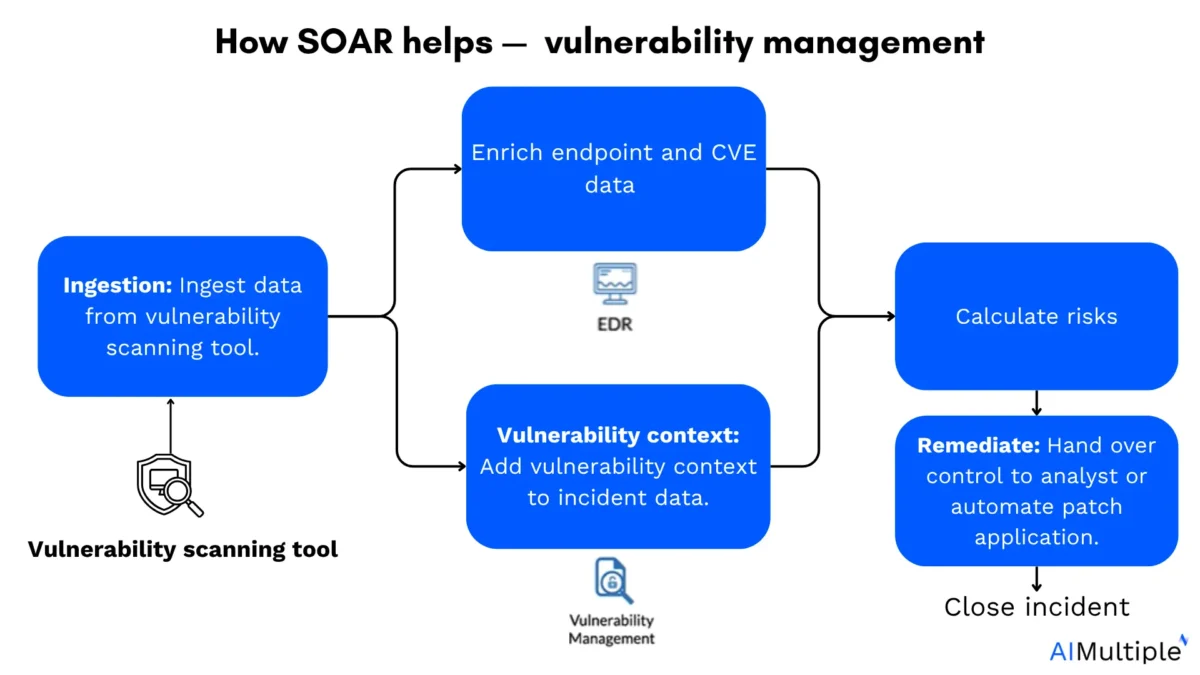
How SOAR helps vulnerability management:
- Collection of vulnerability data: SOAR transfers vulnerability data from external vulnerability management tools, such as CVE databases.
- Enrich: SOAR enriches the vulnerability data with additional information, including details on affected endpoints.
- Add custom fields: SOAR can add custom fields to the vulnerability data to track organization-specific information, such as asset criticality or affected business units.
- Add vulnerability context: SOAR integrates vulnerability context into the incident data, such as exploitation history or known active threats
- Calculate Risks: SOAR calculates the overall risk of each vulnerability by combining the severity of the CVE with the context of the affected system.
- Remediation:
- Analyst review
- Automated remediation
6. Automating the provisioning of new accounts
Problem: Manual user provisioning is error-prone. Human errors in access assignments can lead to over-provisioning (violating least privilege) or under-provisioning (causing productivity loss).
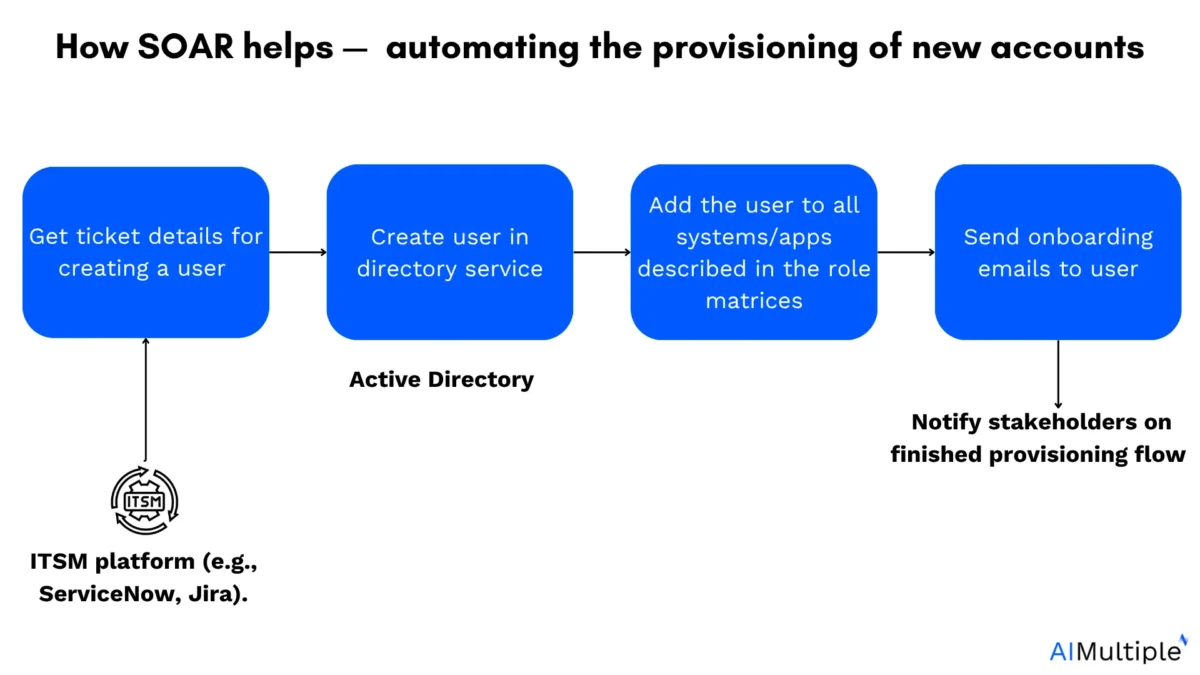
How SOAR helps provisioning of new accounts:
- Get ticket details for creating a user: Retrieves user provisioning request from the ITSM platform and extracts necessary information.
- Create user in directory service: Connects to systems like Active Directory.
- Add user to all tools required by role: Based on the user’s role, SOAR assigns access to tools such as email, HR platforms.
- Send onboarding emails to user: Sends login credentials and setup instructions.
- Deploy required software to endpoint: Initiates software deployment via endpoint management tools to ensure the new hire’s device is ready.
- Notify stakeholders on finished provisioning flow: Alerts HR, IT, and managers once onboarding is complete, closing the loop.
7. Incident lifecycle case management
Problem: Lack of continuity across incident lifecycle due to the following:
- Siloed security products focused on different security areas
- Lack of standardized processes that help continuity across incident lifecycle
- Slow mean time to response due to silos and lack of network visibility
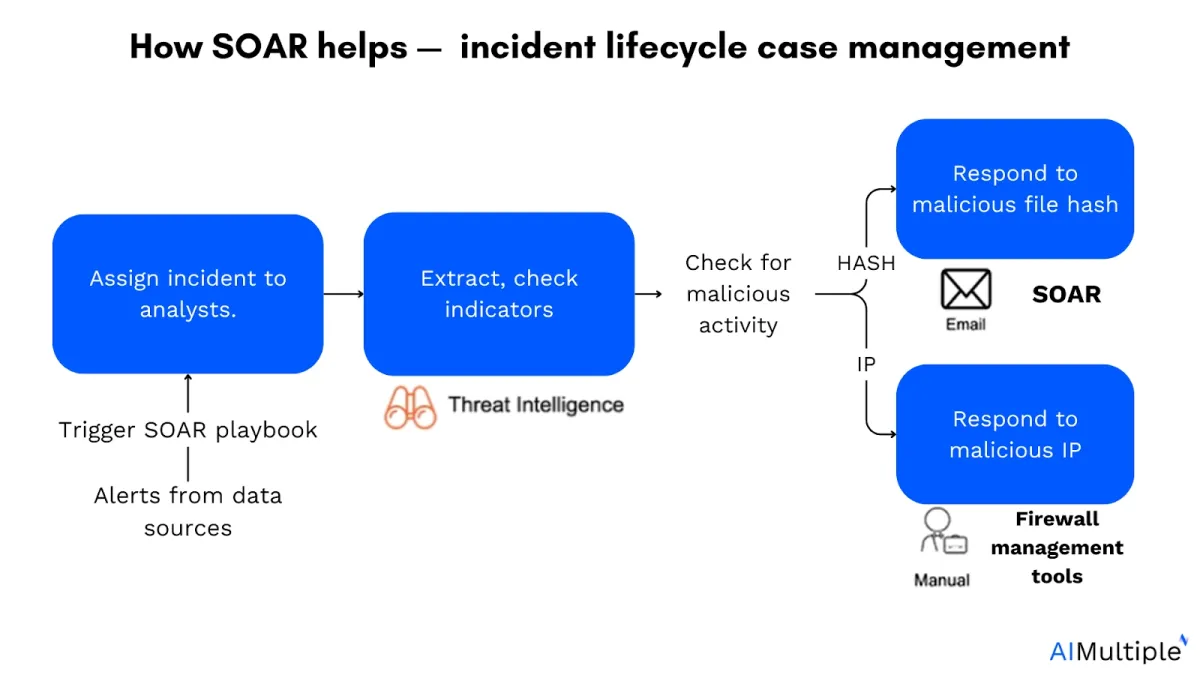
How SOAR helps end-to-end incident lifecycle case management:
SOAR platform leverages lifecycle process management with automating playbooks.
- Retrieve alerts from data sources: SOAR continuously sends alerts from various data sources such as SIEMs, firewalls.
- Trigger SOAR playbook: Upon receiving an alert, SOAR automatically triggers the appropriate playbook, outlining predefined steps to address the specific type of incident (e.g. malware detection or unauthorized access).
- Assign incidents to analysts: SOAR provides enriched data and context to analysts.
- Extract and check indicators with threat intelligence: SOAR extracts indicators of compromise (IOCs) such as file hashes, and IP addresses.
- Check for malicious activity: SOAR determines if the activity is malicious and blocks and isolates the file or IP.
8. Automating firewall policy change requests
Problem: Managing firewall change requests manually is slow, error-prone, and often lacks proper validation. Common challenges include:
- Lack of team efficiency in handling large numbers of requests each week
- Inconsistent rule creation practices, leading to disorganized and overlapping firewall policies
- Limited visibility into the approval and change process, making audit and compliance tracking difficult
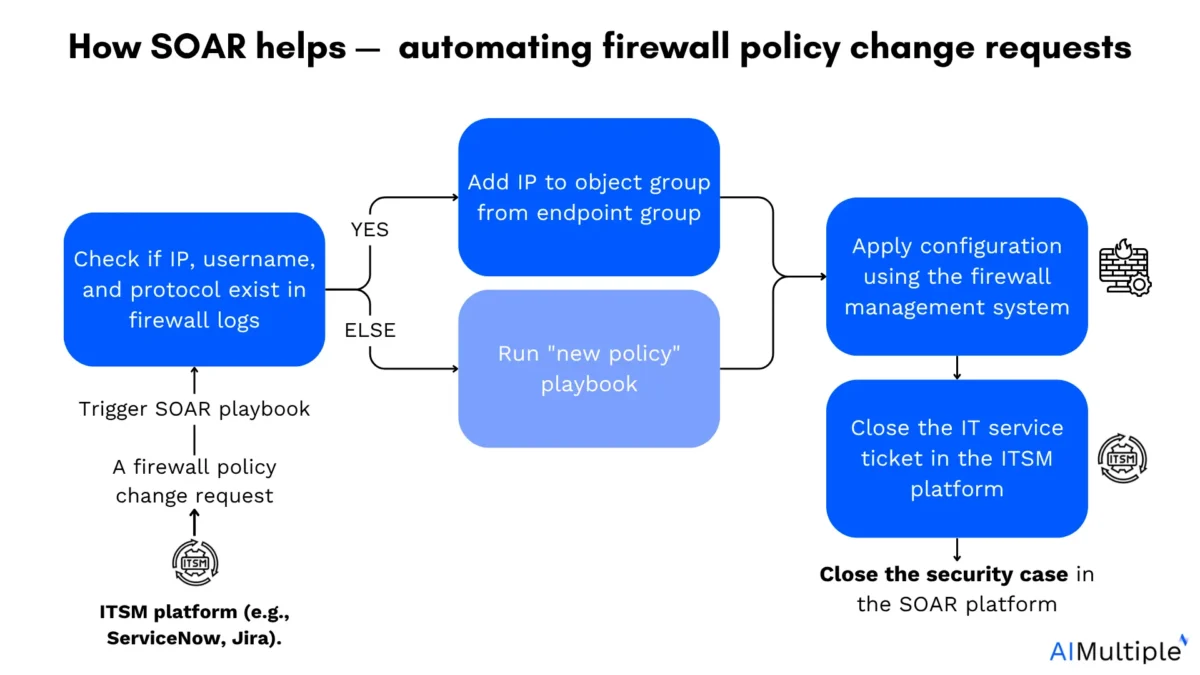
How SOAR helps automate firewall policy change requests:
SOAR streamlines the firewall change process by automating approvals, validations, and policy deployments through integrated playbooks.
- A firewall policy change request: Initiated from an ITSM platform, e.g., ServiceNow
- Trigger SOAR playbook
- Do endpoints role and address exist?
- YES → Add IP address to the existing endpoint group
- ELSE → Call “new policy” playbook: SOAR runs a separate playbook to create a custom rule.
- Apply configuration using the firewall management system
- Close the IT service ticket in the ITSM platform
9. SSL certificate expiration tracking
Problem: When a user attempts to access a site with an expired security certificate, modern web browsers will display warning messages. This can make visitors less likely to return to the site, potentially resulting in a loss of traffic and credibility for the organization.
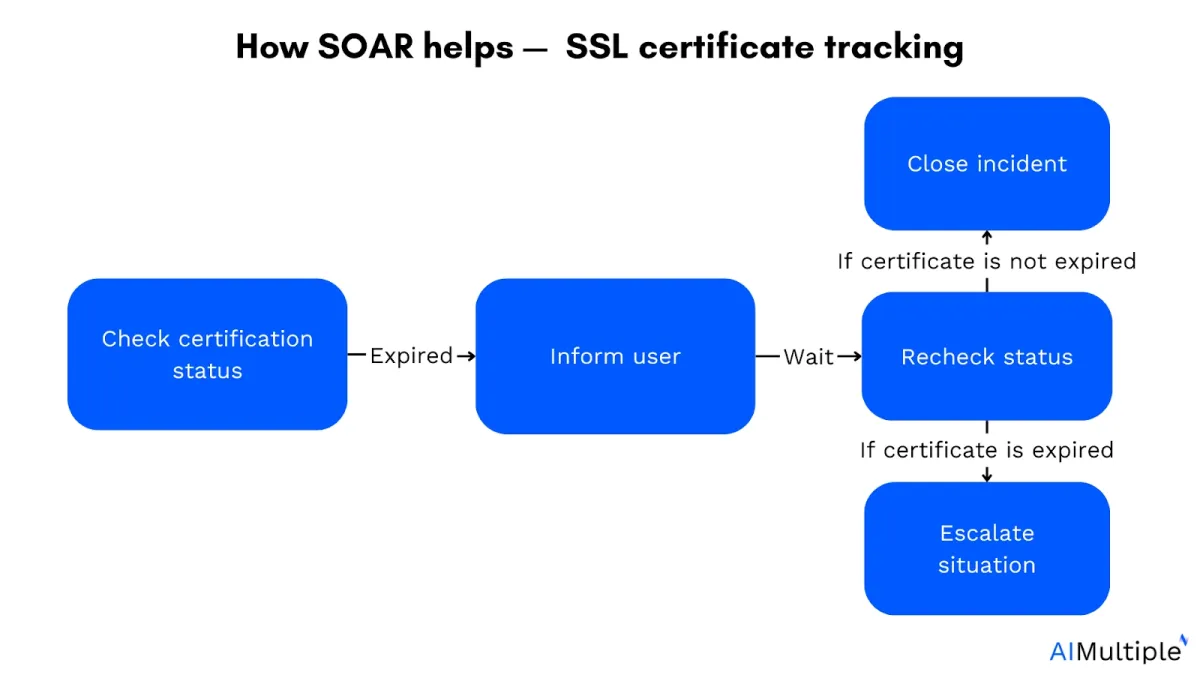
How SOAR helps SSL certificate expiration tracking:
- Check certificate status: SOAR continuously monitors SSL certificates through integration with certificate management tools to check their expiration status.
- Inform user: When a certificate is approaching expiration, SOAR automatically sends notifications to relevant users, alerting them of the upcoming expiration date.
- Recheck certificate status:
- If not expired: SOAR rechecks the status and automatically closes the incident if the certificate is still valid, ensuring that the alert is dismissed.
- If expired: If the certificate has expired, SOAR escalates the incident, sending an alert to the user and other relevant stakeholders in the organization.
- Escalation and communication: SOAR automatically sends detailed emails to the user and includes other important team members, ensuring swift awareness and action.
What is SOAR?
SOAR technology streamlines and automates processes across people and products on one platform, improving organizational security.
Key capabilities of SOAR
- Orchestration
- Playbooks, workflows
- Logically organized plan of action
- Controlling, and activating security product stack from a central location
- Security automation
- Automated scripts
- Extensible product integrations
- Machine execution of playbook tasks
- Response
- Case management
- Analysis and reporting collaboration
SOAR platforms also integrate with various security tools (such as SIEMs, firewalls, endpoint detection, and response systems) to automate repetitive tasks, orchestrate workflows, and improve incident management.
Benefits of SOAR
- Centralization: Integrating security orchestration, intelligent automation, incident management, and interactive investigations into a unified solution.
- Breaking down silos: SOAR increases team cooperation and allows security analysts to perform automated actions on tools throughout their security stack.
- Centralization: Providing security teams with a centralized console for managing and coordinating all company security areas.
- More consistent incident response plans: Optimizing case management, increasing efficiency in ticket opening and closing, and investigating incidents.
- Improved SOC decision-making: SOAR dashboards can help security operations teams make better decisions by providing visibility into their networks and threats. This information can assist SOCs in identifying:
- false positives
- prioritizing alerts
- and selecting the appropriate reaction methods
- Handling more notifications in less time: SOARs can help manage alerts by centralizing security data, enhancing events, and automating replies. As a result, SOCs can handle more alerts.
SIEM vs SOAR vs XDR
- SIEM: SIEM tools gather and aggregate data from internal security tools, centralizing logs and flagging anomalies.
- SOAR: SOAR systems emerged to enhance SIEMs by adding orchestration, automation, and incident response capabilities that standard SIEMs often lack. They focus on automating repetitive tasks, improving incident management, and coordinating security tools.
- XDR (extended detection and response): XDR is a newer and more powerful solution for end-to-end security event management, it is mainly used for addressing issues at internal endpoints. When preparing for an automatic response, XDR uses data captured by SIEM.
Large organizations often use all three tools, but vendors increasingly combine their features.
- Some SIEMs now include response capabilities.
- XDRs are incorporating SIEM-like data logging.
- Vendors such as Microsoft Sentinel and ManageEngine Log360 offer SIEM and SOAR capabilities.
- Some experts predict that XDR may eventually consolidate all these tools.4


Comments
Your email address will not be published. All fields are required.