Unlike commercial SIEMs such as ManageEngine Log360, open-source SIEM tools commonly lack core SIEM capabilities including event correlation, log analytics, alerting, or require combining with other tools.
However, several network defensive tools (e.g., intrusion detection and prevention systems and network monitoring tools) can be used as SIEM tools with fine tuning. For example, OSSEC, an intrusion detection and prevention system, includes core SIEM capabilities: it collects data and analyzes it, but requires hand-rolled modifications for log analytics.
Here are the free open source and SIEM tools to build your own solution from the ground up:
Open source SIEM tools
| Tool | GitHub stars | Primary use case | Pricing |
|---|---|---|---|
| Wazuh | 11,000+ | SIEM | ✅ Free (on-prem version) |
| Graylog | 7,600+ | SIEM | ➕ Freemium |
| OSSEC | 4,600+ | SIEM | ➕ Freemium |
| SecurityOnion | 3,600+ | SIEM | ✅ Free |
| AlienVault OSSIM | 120+ | SIEM | ✅ Free |
| The ELK Stack | 17,000+ | Logging repository and analytics | ➕ Freemium |
| Fluentd | 13,000+ | Logging repository and analytics | ➕ Freemium |
OpenSearch | 10,000+ | Logging repository and analytics | ➕ Freemium |
| Apache Metron | 800+ | Logging repository and analytics | ➕ Freemium |
| Suricata | 5,000+ | Intrusion detection | ➕ Freemium |
| Snort3 | 2,800+ | Intrusion detection | ➕ Freemium |
| ZABBIX | 4,700+ | Monitoring | ➕ Freemium |
| Nagios | 1,600+ | Monitoring | ➕ Freemium |
These tools typically store logs in Elasticsearch indices for a configurable retention period based on storage and data policies. For long-term storage, additional archival procedures or integrations may be needed.
SIEM capabilities
| Tool | Agentless log collection | Built in log correlation |
|---|---|---|
| Wazuh | ✅ | ✅1 |
| Graylog | ❌* | ✅ (In paid version) |
| OSSEC | ✅ | ✅ |
| SecurityOnion | ❌ | ✅ |
| AlienVault OSSIM | ❌ | ✅ |
| SIEMonster | ❌ | ✅ |
| The ELK Stack | ✅ | ❌ With Yelp/elastalert integration |
| Fluentd | ❌ | ❌ |
OpenSearch | ❌ | ❌ With security analytics plugin |
| Apache Metron | ✅ | ✅ |
| Suricata | ✅ | ✅ |
| Snort3 | ✅ | ✅ |
| ZABBIX | ✅ | ✅ |
| Nagios | ✅ | ❌ |
*❌: Requires third-party agent integrations (e.g. Elastic Agent).
Insights come from user experiences shared in Reddit1 , and G22 .
How to select the best open-source SIEM tool?
There is no all-in-one open source SIEM system. Current solutions either lack essential SIEM features like event correlation and reporting or require to be integrated with other tools.
- SIEM-focused tools: Provide most core SIEM capabilities like built-in log correlation, alerting, visualization of log data, compliance reporting, etc.
- Logging repository and analytics-focused tools: Provide a collection of tools for collecting and processing logs; however, they lack some core SIEM capabilities like built-in log correlation.
Some organizations use OpenSearch, Fluentd, Apache Metron as a local logging repository for security data. (ELK stack can be used for SIEM, it provides a full suite of tools (Kibana, Elasticsearch, Logstash) to perform SIEM).
- Monitoring-focused tools: ZABBIX and Nagios can parse logs; however, they are not useful for log correlation and searching. Some organizations integrate these systems with their SIEMs to:
- Monitor infrastructure and networking equipment.
- Get notifications of any issues (e.g., via Microsoft Teams using webhooks).
- Use a dashboard to visualize logs.
If you prefer not to build the SIEM functionality yourself—such as creating ready-made dashboards, preconfigured searches, and point-and-click hunt-pivoting—and want to avoid paying for features, it’s likely more efficient to integrate free SIEM tools (e.g. Security Onion) with logging repositories and analytics frameworks like the ELK stack, OpenSearch, or SELKS.
For example, Apache Metron integrates with the ELK stack’s data visualization tool, Kibana, to provide data visualization with pre-built templates for monitoring your Metron deployment. This integration reduces the need for hand-rolled log analytics.3
Who needs a SIEM?
Who should not use SIEM:
If you do not have regulatory requirements, a full-fledged SIEM could indeed be unnecessary for a smaller setup with just ~50 endpoints since
- The log data generated might be manageable without the need for a dedicated SIEM.
- Small organizations might lack personnel to manage and actively monitor the SIEM.
SIEM would be a later, more mature stage investment. Organization with minimal infrastructure, such as small businesses using a BYOD model and relying on SaaS applications, a SIEM may not provide much value. There is limited data to collect and send to the SIEM in these cases.
A SIEM may not be necessary on its own, but it might be required to meet a specific goal or compliance need. For example, if adhering to the NIST CSF, using a SIEM to fulfill PR.PT-4 (communication and control networks are protected) would be a logical step, as it helps monitor and protect network traffic.
An alternative could be outsourcing to an MSSP provider or open-source SIEM tool with log aggregation/analytics capabilities, which might offer greater value than maintaining an in-house SIEM.
Who should use SIEM:
If you have a large and complex IT infrastructure, subject to regulatory frameworks like PCI-DSS, HIPAA, or GDPR, and a dedicated security team or SOC (security operations center), you should consider commercial alternatives.
Commercial alternatives
Open source SIEM tools commonly lack intuitive rule creation interfaces in commercial tools. Additionally, their correlation functionalities are more basic and mostly do not offer the out-of-the-box capabilities like:
- ready-made dashboards for log management
- compliance reports (e.g., PCI-DSS, HIPAA)
- integrations with other enterprise tools, such as firewalls, endpoint protection systems,
Commercial SIEM tools provide core SIEM capabilities including:
- event correlation, log analytics
- ability to do risk scoring
- providing recommended actions based on risk scores
- long-term retention up to 12 months
- user and entity behaviour analytics with pre-built machine learning models
Who is it for: Commercial alternatives are best suited for large-scale organizations with a SOC looking for a ready-made solution.
Commercial SIEM tools also provide various orchestration and response functions, and ways to automate SOC tasks. Some SIEM vendors have incorporated SOAR capabilities to be more responsive. This is typical as more security tools add more automation features to make them easier to use and more productive. In some cases, this moves these products into the SOAR category.
Example vendors
- ManageEngine Log360 is a unified SIEM, SOAR solution. It can ingest logs from 700+ sources, including applications such as web servers, Oracle, MS SQL, and vulnerability scanners.
- Exabeam Fusion’s long-term search includes 12 months of log retention. Its Security Analytics/UEBA offers over 1,800 detection rules, including those for cloud threat detection, along with 800 behavioral models. It also integrates security orchestration, automation, and response (SOAR) with pre-built playbooks and a no-code editor.
- Microsoft Sentinel is a cloud-based SIEM and SOAR solution offering 100+ threat-hunting queries, workbooks, and playbooks. It includes a free trial with 10 GB of daily usage for 31 days and free log storage up to 90 days.
- IBM QRadar offers key SIEM capabilities such as risk-based alert prioritization, endpoint detection and response, and SOAR to orchestrate and automate incident response (IR) across your workflows.
- Splunk Enterprise Security stands out from open-source SIEM tools with its integrated feature set. While open-source SIEM tools often lack SIEM capabilities like risk-based alerting (RBA), drag-and-drop customizable dashboards, and user and entity behavior analytics (UEBA), Splunk provides these features out-of-the-box.
For more details:
- Top 10+ SIEM systems: How to Choose the best solution
- Top 10+ SOAR software & open source alternatives
Open source SIEM tools explained
Wazuh
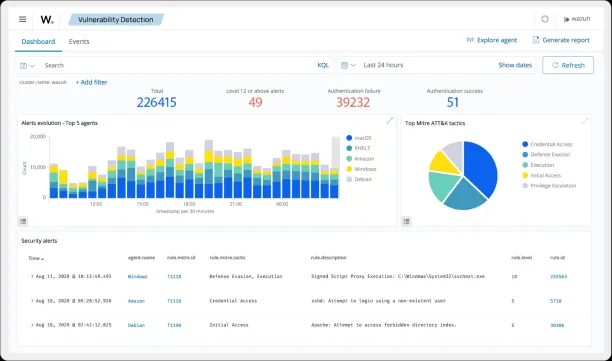
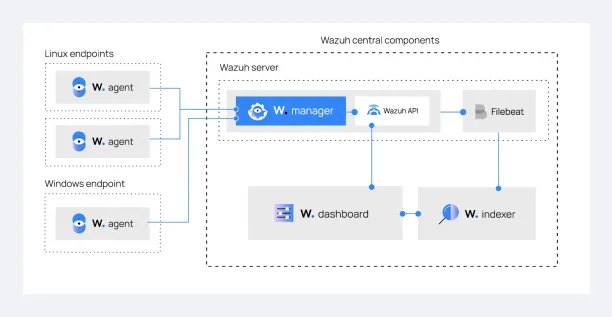
Wazuh includes four main components:
- Indexer: The Wazuh indexer indexes and stores notifications. It also has a search engine for sorting through alerts.
- Server: This is the core component of this SIEM solution; it collects logs from agents and can analyze events to identify indicators of compromise.
- Dashboard: This is Wazuh’s graphical interface, which allows you to visualize events and threats across the network.
- Agent: This component runs on the end devices and sends events to the server.
Wazuh utilizes OpenSearch and OpenDashboard, the Amazon-led open-source forks of Elasticsearch and Kibana, for centralized log management, security monitoring, and data visualization.
Capabilities:
- Security log analysis
- Vulnerability detection
- Security configuration assessment
- Regulatory compliance
Features:
- Alerting and notification
- Reporting insights from SIEM events
See Wazuh’s concept:
Graylog

Graylog collects all your logs in one central location, enabling you to create alerts and dashboards. However, several SIEM features, such as log search filtering, log archiving, and anomaly detection, are part of the paid offerings.
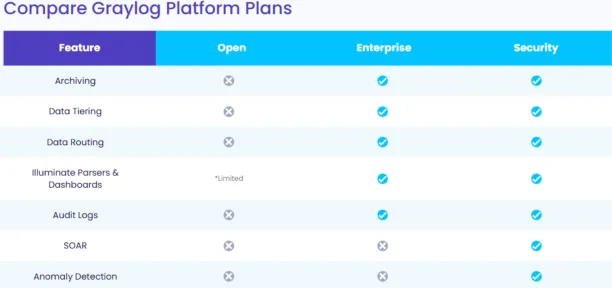
The paid Graylog Security version offers additional SIEM capabilities, such as pre-built log data visualizations, predefined reports, and minimal configuration effort, making it a better fit for organizations seeking these automated SIEM capabilities.
OSSEC
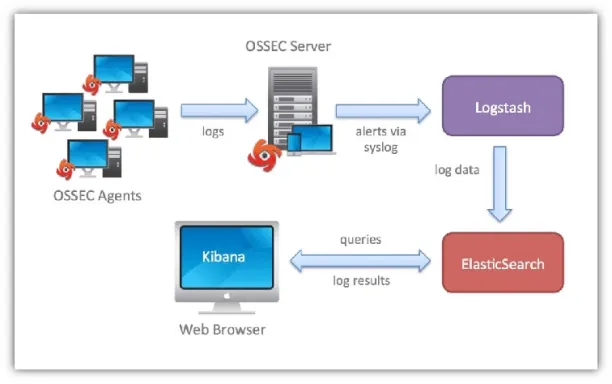
OSSEC is an open-source Host Intrusion Detection System (HIDS).
Components:
- Manager: Collects logs from data sources.
- Agents: Collect and process logs.
OpenSearch as a SIEM solution: OSSEC provides core SIEM capabilities: it collects and analyzes data; however, it lacks some of the basic log management and analysis components required.
SecurityOnion
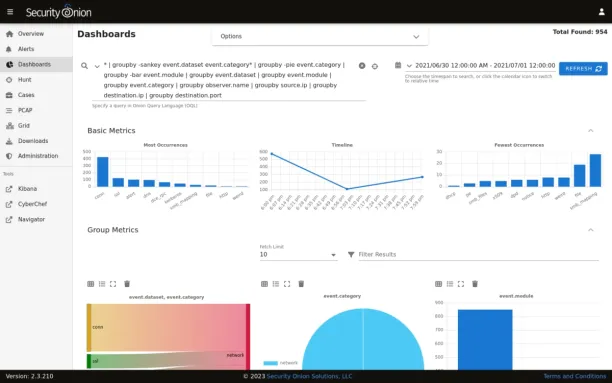
SecurityOnion functions as a SIEM and intrusion detection system (IDS). It integrates other open-source tools like Snort, Suricata, and Wazuh to offer comprehensive monitoring and detection features for network and host-based intrusion.
SecurityOnion includes useful tools for deep analysis, such as Wireshark for network traffic analysis and Network Miner for packet capture and network forensics.
SecurityOnion as a SIEM solution:
- Host-based & network-based IDS: Monitors and detects suspicious activity on hosts and networks.
- Fullpacket capture (FPC): Captures network traffic with netsniff-ng to detect data exfiltration, malware, phishing, and other attacks.
- Threat detection: Uses SGUIL in SecurityOnion to identify malicious activity, including failed logins to firewalls and domain controllers, enhancing visibility and insights.
AlienVault OSSIM
OSSIM is the open-source version of AlienVault’s Unified Security Management (USM) offering. It offers essential SIEM features such as event collection, processing, and normalization.
AlienVault OSSIM as a SIEM solution: A key strength of OSSIM is the inclusion of OpenVAS (an open-source vulnerability scanner). This allows OSSIM to correlate IDS logs (from tools like Snort and Suricata) with vulnerability scanner results.
OSSIM offers:
- Event collection and processing.
- Correlation of security data from multiple sources.
- Vulnerability assessment with OpenVAS integration.
- Alerting based on security events.
Missing key features:
The open-source version of OSSIM lacks some SIEM features available in the commercial version, such as:
- Reporting
- Real-time event response or alerting console
- Ability to tag and separate logs
ELK Stack
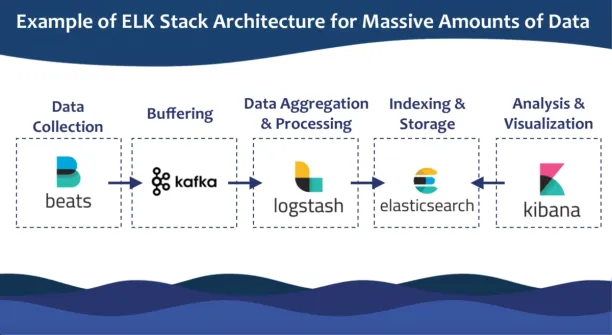
The ELK stack, which was previously open-source, is no longer completely open-source. The stack is still available in a free edition for compatibility with legacy systems, but it is no longer fully open-source.
Components of the ELK Stack:
- Elasticsearch: A storage and indexing engine designed for time-series data.
- Logstash: A log aggregator that collects, processes, and refines data from multiple sources.
- Kibana: A powerful tool for visualizing the data within the stack.
- Beats: Lightweight log shippers that gather data and forward it into the stack.
ELK Stack as a SIEM solution: ELK stack provides log aggregation, processing, and visualization, however, is not a complete SIEM system.
- Missing key features:
- Correlation engine: ELK Stack’s free version does not include a built-in correlation feature. However, there are open-source alternatives, such as Yelp/Elastalert, that can be used for correlation.
- Built-in reporting or alerting: This is a significant drawback for SIEM use and general IT operations.
- Built-in security rules: This increases the stack’s resource and operational requirements.
Fluentd
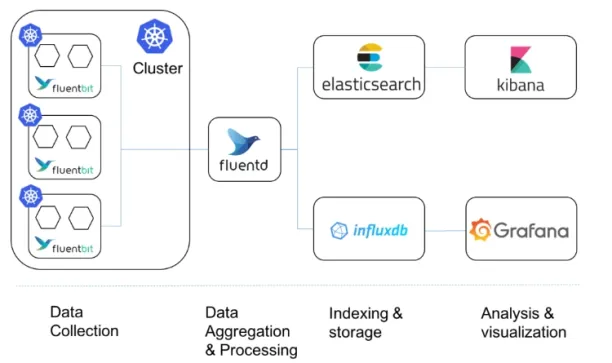
Fluentd, by itself, is not a full-fledged SIEM tool, it functions as a data collector and log forwarder for collecting logs, metrics, and event data and then routing them to other systems for processing and analysis.
Fluentd as a SIEM Solution
- Log collection and forwarding: Fluentd is highly efficient in gathering logs from several sources and forwarding them to SIEM platforms for further analysis.
- Integration: Fluentd integrates seamlessly with popular tools like Elasticsearch, Splunk, and Snowflake, as an essential log ingestion component.
- Real-Time Data Processing: Fluentd processes logs in real time, enabling the immediate forwarding of log data.
Missing key features:
- Threat detection: Fluentd does not perform threat detection or analysis, a core capability of SIEM systems.
- Log correlation: It cannot correlate events across multiple data sources to identify complex security incidents.
- Alerting and reporting: Fluentd does not include built-in alerting or reporting features typically found in SIEM solutions.
- Long-term data storage: Fluentd does not offer storage solutions for logs; it simply forwards data to external systems.
OpenSearch

OpenSearch, launched in 2021 as a fork of Elasticsearch and Kibana, is an open-source software project led by AWS. It includes OpenSearch (the database) and OpenSearch Dashboards (for visualization and analytics).
OpenSearch as a SIEM solution: While not a full SIEM, OpenSearch can be used by organizations to store and analyze security data. However, like the ELK stack, it requires hand-rolling core SIEM features such as security detections and analytics.
Apache – Metron
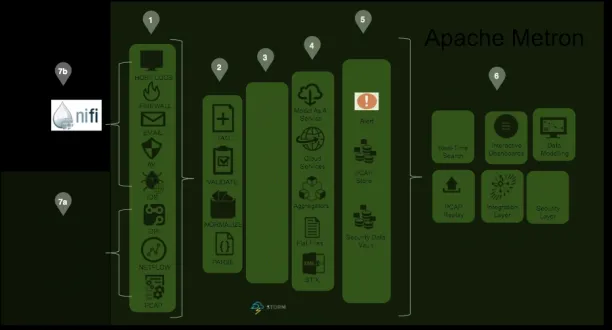
Apache Metron provides a centralized platform for managing security telemetry. Metron provides standard SIEM like capabilities (alerting, threat intel framework, agents to ingest data sources) but also has packet replay utilities, evidence store and hunting services commonly used by SOC analysts.
To use Metron, you need to deploy it on your infrastructure (either on-premise or in a cloud environment) and configure it for your specific needs.
Apache Metron as a SIEM solution:
- Data collection: Metron uses Apache Nifi and Metron probes to collect security data from various sources. Data is streamed into Apache Kafka topics for further processing.
- Event normalization: Security events are parsed, normalized into standard JSON format, and enriched for analysis.
- Alerting: Alerts can be triggered based on specific event types, enabling real-time threat detection.
- Visualization: Metron can integrate with Kibana for data visualization, enabling quick access to security insights.
- Data storage: Events are indexed and stored in Apache Hadoop, with data stored in Elasticsearch or Solr, depending on the user’s preference.
Suricata
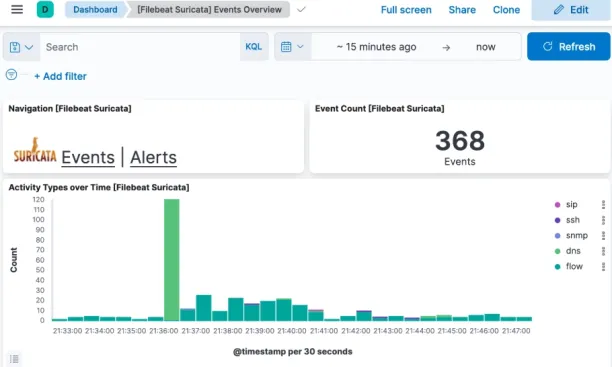
Suricata is a network intrusion detection and prevention system (IDS/IPS) that provides deep packet inspection and network monitoring. Suricata is not a complete SIEM solution.
Suricata integrates with the Elastic Stack for SIEM by utilizing Elasticsearch for storing and querying logs, Filebeat for forwarding data, and Kibana for visualizing and analyzing network security events. This setup helps organizations proactively monitor and respond to security threats in real-time.
Suricata as a SIEM solution:
- Primary function: Suricata analyzes network traffic for attacks (similar to Snort), including protocol-specific analysis (e.g., HTTP, DNS, SSH) and application-layer detection.
- Alerting: Suricata generates real-time alerts based on detected anomalies or threats, which can be forwarded to SIEM platforms for further processing.
- Strengths: Provides more detailed application-layer insights, such as HTTP and SSH traffic detection.
Snort
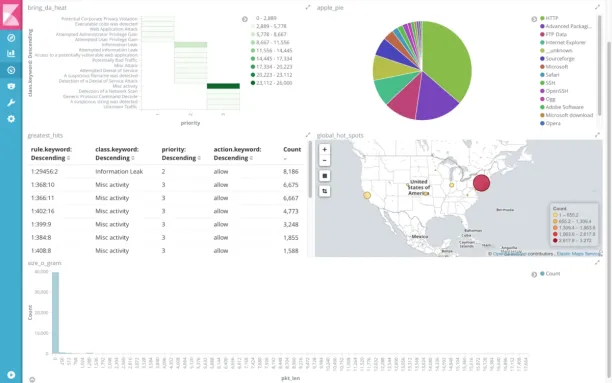
Snort is a widely used network intrusion detection system (NIDS) that primarily focuses on network traffic analysis and threat detection, it is not a complete SIEM solution. Similar to Suricata, it integrates with the Elastic Stack for enhanced security monitoring and analysis.
Snort as a SIEM solution:
- The primary function: Detect network-based attacks such as DDoS, stealth port scans, and OS fingerprinting.
- Alerting: Snort generates alerts based on detected threats and sends them to syslog or other logging systems, which can then be processed and analyzed by a SIEM platform.
- Integration: Snort can integrate with other SIEM tools like Elasticsearch, Logstash, or Splunk for enhanced correlation and analysis of network security events.
- Limitations: As a standalone solution, Snort lacks essential SIEM features like log normalization, centralized storage, or comprehensive incident response management. It focuses purely on network intrusion detection.
Zabbix
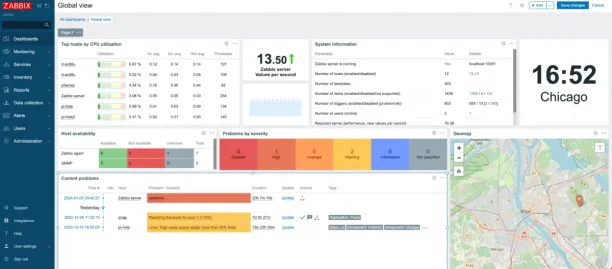
While Zabbix can parse logs from Windows and Linux systems, I wouldn’t consider it a true SIEM.
Zabbix is useful for network monitoring, though, and for collecting historical performance data. I would encourage you to run Zabbix in addition to a SIEM, where the SIEM is used for the log data and for searching and correlating the logs.
Nagios
Nagios is a comprehensive monitoring application that tracks the status of hosts, services, and networks. It allows organizations to monitor the health and performance of their IT infrastructure.
The Nagios log server engine collects data in real time and sends it to a search tool. You can use Nagios as a log archive and monitoring tool that simplifies data collection and makes information available to system administrators.
Key features:
- Monitoring:
- Monitors network services (e.g., SMTP, HTTP, PING) and host resources (e.g., CPU, disk usage).
- User-created service monitoring via plugins.
- Log management:
- Automated log rotation and archiving.
- Filters log data by geographic origin.
- Online interface for network status and log viewing.


Comments
Your email address will not be published. All fields are required.