SIEM systems have evolved to become more than log aggregation tools. Some vendors developed unified product suites with UEBA, SOAR, and EDR capabilities, claiming they are “next-gen” SIEMs. Others offer products focused on traditional event and log management (e.g., SolarWinds SEM).
Below is an overview of leading SIEM tools based on their next-gen SIEM and security capabilities:
Next-gen SIEM capabilities
| Vendor | UEBA | SOAR | EDR |
|---|---|---|---|
| ManageEngine Log360 | ✅ | ✅ | ❌ |
| Exabeam Fusion | ✅ | ✅ | ✅ |
| IBM QRadar SIEM | ✅ | ❌ | ❌ |
| LogRhythm | ❌ | ❌ | ❌ |
| Rapid7 InsightIDR | ✅ | ✅ | ✅ |
| Microsoft Sentinel | ✅ | ✅ | ❌ |
| FortiSIEM | ✅ | ✅ | ❌ |
| Splunk Enterprise Security | ❌ | ❌ | ❌ |
| Sumo LogicCloud SIEM | ✅ | ❌ | ✅ |
| SolarWinds SEM | ❌ | ❌ | ❌ |
| Elastic Stack | ❌ | ❌ | ❌ |
| Datadog | ✅ | ❌ | ✅ |
Vendors (marked with “❌”) require integrations to provide the given feature.
- UEBA helps analyze and correlate data in context. By focusing on behaviors rather than just raw logs, SIEMs with UEBA provide a more granular view of an attack’s progression, helping security teams view not just the raw event data, but the patterns.
- SOAR enhances traditional SIEM capabilities by automating security responses, orchestrating security tools for seamless coordination, and providing structured case management through predefined playbooks, enabling faster incident resolution.
- EDR enables SIEMs to gain comprehensive visibility across your network for in-depth analysis at the endpoint level. Correlating EDR findings with SIEM data strengthens the context for network-wide investigations and threat hunting.
Buyers already using UEBA software or SOAR software can integrate machine and log data into their SIEM for context-based log analysis.
Security capabilities
| Vendor | Lateral movement detection | Nonrepudiation | STIX/TAXII threat feeds |
|---|---|---|---|
| ManageEngine Log360 | ✅ | ❌ | ✅ |
| Exabeam Fusion | ✅ | ❌ | ❌ |
| IBM QRadar SIEM | ✅ | ✅ | ✅ |
| LogRhythm | ❌ Requires integrations | ❌ | ✅ |
| Rapid7 InsightIDR | ✅ | ❌ | ❌ |
| Microsoft Sentinel | ✅ | ✅ | ✅ |
| FortiSIEM | ✅ | ❌ | ✅ |
| Splunk Enterprise Security | ❌ Requires integrations | ❌ | ✅ |
| Sumo Logic | ✅ | ❌ | ✅ |
| SolarWinds SEM | ❌ | ❌ | ❌ |
| Elastic Stack | ✅ | ❌ | ✅ |
| Datadog | ✅ | ❌ | ❌ |
- Lateral movement detection: SIEM’s ability to automatically detect and alert on unauthorized movement of attackers across the network.
- Nonrepudiation (principle): Involves encryption, and digital signatures, ensuring that security event logs and data are stored in a tamper-proof manner, thus the parties involved in a digital transaction cannot later deny their authenticity or their involvement. It can be implemented in any SIEM via additional deployment.
- STIX/TAXII format threat feeds: Standardized threat intelligence for real-time identification and blocking of IOCs.
Metrics
| Vendor | Max EPS | # Integrations | # Pre-built detection rules | # MITRE coverage |
|---|---|---|---|---|
| ManageEngine Log360 | 25,000 | 10+ | 30+ | – |
| Exabeam Fusion | 1M+ | 549 | 1,800 | 101 |
| IBM QRadar SIEM | 1M+ | 186 | 900 | – |
| LogRhythm | – | 200+ | 1,100+ | – |
| Rapid7 InsightIDR | – | – | 900 | – |
| Microsoft Sentinel | 1M+ | 66 | 450 | 87 |
| FortiSIEM | 1M+ | – | 3,000 | 900 |
| Splunk Enterprise Security | 1M+ | 2,200+ | 1,400 | 300+ |
| Sumo Logic | 19,100 (With 90% CPU usage) | 100+ | 900 | 900 |
| SolarWinds SEM | 2,500 | 1,500+ | 700 | 0 |
| Elastic Stack | 4,000 | 300+ | 1,100+ | 92 |
| Datadog | 500,000 | 800 | 250+ | 27 |
| SentinelOne | 23,000+ | 160+ | 2,000+ | – |
- Max EPS: Maximum ‘Events Per Second’ that can be used. EPS is a metric that measures the rate at which the SIEM system processes and analyzes security events or logs. Using a maximum # of EPS may require additional vendor licenses.
- # Integrations: Number of external systems (e.g., firewalls, servers, EDRs) the SIEM can integrate.
- # Pre-built detection rules: Number of predefined detection rules in the SIEM that help identify common security threats and incidents based on known attack patterns.
- # MITRE coverage: Number of MITRE ATT&CK framework techniques that the SIEM can detect or map to, helping identify and mitigate specific tactics used by threat actors.
Do I need a SIEM in my SOC?
The decision to implement a SIEM solution in your security operations center (SOC) depends largely on the size, complexity, and regulatory requirements of your organization, as well as the resources available to manage and maintain the system.
When a SIEM is needed:
SIEM would be a later, more mature stage investment. In-house SIEMs are resource-intensive and require an internal security team, an alternative could be outsourcing to an MSSP provider or a log management tool for log aggregation and analytics.
Organizations with:
- Large and complex IT Infrastructure: Need a SIEM for real-time monitoring, event correlation, and incident response across a diverse and extensive IT environment.
- Compliance requirements: Need a SIEM to ensure continuous monitoring and provide detailed audit trails that meet regulatory requirements like PCI-DSS, HIPAA, or GDPR. It helps in real-time detection of security events, ensuring compliance with security standards and regulatory mandates.
When a SIEM is not necessary:
- Smaller organizations with limited infrastructure: A full-fledged SIEM may not be practical for organizations with less than 100 endpoints or a cloud-based/BYOD setup.
- Lack of expertise or resources: SIEMs require skilled resources for configuration and continuous monitoring. SIEMs would not be effective for small businesses with limited personnel or expertise to monitor the SIEM solution.
Alternatives to a full-fledged SIEM:
- Open source log management tools: A central log management solution provides a centralized view of log data across the organization.
- Managed security services (MSS) or managed detection and response (MDR) services: Outsourcing to an MSSP or MDR service can provide security visibility without the overhead of managing a full-fledged SIEM.
- Open source SIEM tools: Open-source SIEM tools can offer log aggregation and basic analytics capabilities without heavy internal investment.
ManageEngine Log360
ManageEngine Log360 is a unified SIEM solution that offers DLP, UEBA, and SOAR capabilities. It integrates seamlessly with other ManageEngine products like ADAudit Plus and EventLog Analyzer.
Log 360 can collect and process log data from over 700+ sources, including applications such as IIS web servers, Apache web servers, Oracle, MS SQL, and vulnerability scanners.
Distinct feature: In a SIEM context, Log360 detects and analyzes security events. Once a threat is identified (such as malicious logs), its SOAR capabilities execute Cisco ASA firewall commands, such as adding inbound and outbound rules without needing to manually switch between different security tools.
This positions Log360 as a strong tool for proactive troubleshooting.
Distinct feature: Log 360 can also integrate with cloud access security brokers (CASBs) to regulate access to sensitive data in the cloud, track the use of sanctioned and unsanctioned applications, and detect shadow IT applications in your infrastructure.
This is particularly useful for organizations aiming to enforce cloud security policies and mitigate risks from unauthorized apps.
Exabeam Fusion

Exabeam Fusion primarily functions as a UEBA solution, offering the ability to create static “rules” that define maximum-risk data sources.
It includes the log collection/management component, the SOAR component, and the archive component. Offers 12 months of log retention with correlation rules and dashboards. For compliance, it provides long-term storage with over 10 years of log archiving.
It allows each member to add their notes and store queries used for monitoring Indicators of Compromise (IoCs). This process is similar to LogRhythm’s case management system but without the need to navigate its complex correlation language.
While Exabeam can create static rules, the parsing capabilities may not be fully optimized for all environments. For example, when integrating Exabeam with SIEMs like ELK, the ingested source logs do not align with predefined data formats (e.g., timestamps). The solution may require a custom parser, though this aspect has not been fully explored.
IBM QRadar

IBM QRadar SIEM (Cloud-Native SaaS) solution is part of the IBM QRadar Suite.
It has a modular design that allows for threat identification and prioritization. QRadar is useful for basic, commodity app/system logging and ‘structured data’ management.
Supports different logging protocols including syslog, syslog-tcp, and SNMP. It can read and interpret events from more than 300 log sources. The solution includes a data synchronization app store as an add-on where users copy data (events and flows) and configuration files
Supports open source Sigma rules, allowing organizations to import these rules and automatically convert them to KQL (Kusto Query Language). KQL is an open-source data language designed for ease of use by security analysts
However, IBM QRadar has some drawbacks, including complex pricing plans. Furthermore, another drawback is that IBM QRadar is slow for searching, and their support is offshored.
LogRhythm SIEM

LogRhythm is a SIEM solution that incorporates SOAR capabilities. It also offers threat monitoring, threat hunting, threat investigation, and incident response capabilities.
The solution can collect, normalize, and interpret the event and log data from 1,000+ third-party and cloud sources.
LogRhythm seamlessly contextualizes intricate information into straightforward language with LogRhythm’s Machine Data Intelligence (MDI) Fabric.
Rapid7 InsightIDR
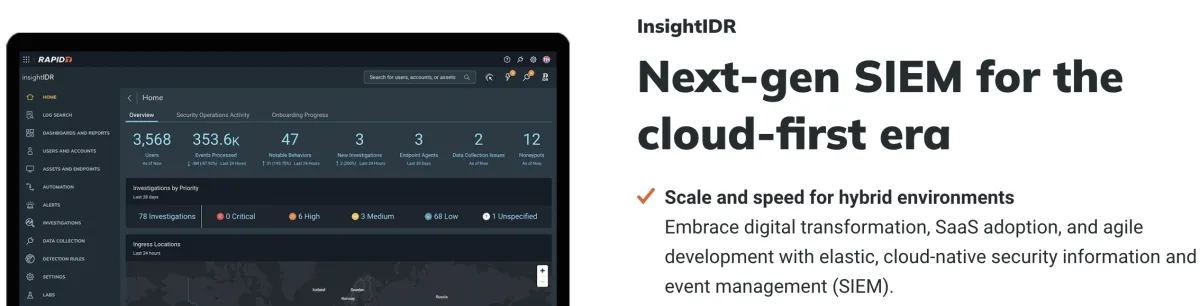
Rapid7’s InsightIDR, a cloud-native SIEM and XDR, offers real-time threat hunting and response by integrating data from diverse sources, including logs, endpoints, and cloud services.
The SIEM tool provides users with 13 months of searchable data storage by default, allowing them to search through normalized events, security incidents, and indicators of compromise.
InsightIDR focuses on real-time threat detection and incident tracking, enabling quicker decision-making.
Microsoft Sentinel
Microsoft Sentinel primarily collects and correlates Microsoft Cloud security logs and events. It is compatible with a limited number of non-Microsoft solutions. The playbooks are extensive and need coding knowledge.
It provides unique features not available in other platforms, such as preprocessing logs at the ingest level, which allows non-security-relevant events to be filtered out before reaching the SIEM.
Raw logs can be stored in inexpensive Azure storage, they remain fully accessible for detailed investigations within Sentinel.
FortiSIEM

FortiSIEM is a security operations platform that includes a built-in configuration management database (CMDB), which helps to discover both physical and virtual infrastructure, whether on-premises or in public/private clouds.
FortiSIEM’s user and device risk scoring capabilities are highly useful for an SIEM system as they provide a dynamic, data-driven approach to threat detection and response since it :
- assigns risk scores to both users and devices
- prioritizes security alerts based on the level of risk associated with a particular user or device
This enables proactive identification of users or devices that might pose a security risk, allowing for quicker remediation actions before potential breaches occur.
Splunk Enterprise Security
Splunk Enterprise Security is a SIEM solution with application, and network monitoring capabilities. In addition to its SIEM capabilities, Splunk Enterprise Security can help SOCs monitor network or application topologies to identify bottlenecks, hence it can be used as a debugging solution for enterprise-wide actions.
However, Splunk Enterprise Security’s integrated behavioral analytics and automation capabilities are limited, making it difficult to detect modern threats and strategies like lateral movement.
The solution does not offer built-in SOAR and UEBA. and requires extensive customization.
Sumo Logic

Sumo Logic offers seamless search capabilities to quickly retrieve and analyze logs using new search patterns. For example, you can analyze checkout data by counting page visits, sorting results, and generating a funnel graph in minutes. Its ease of use makes it ideal for developers and real-time dashboards.
Its cloud SIEM automation service enables you to execute playbooks either manually or automatically when an insight is created or closed.
Offers two pricing options that include SIEM solutions: enterprise suite and flex pricing.
SolarWinds Security Event Manager
SolarWinds Security Event Manager (SEM) is an on-premises Security Operation Center tool (SOC). It collects log and security data from the network intrusion detection system (NIDS) and uses this security event data to optimize existing IDS security systems and protocols.
SEM does not have a cloud-based deployment option. The SIEM software offers subscription or perpetual licensing, there is no detailed and publicly available pricing plan.
Elastic Stack
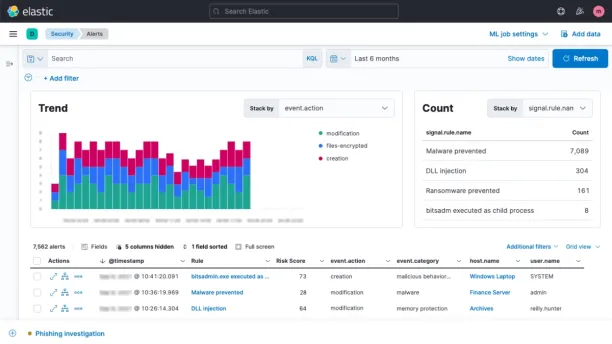
Elastic Security, part of the Elastic Stack (ELK).
It provides several out-of-the-box integrations, however, customizing them requires technical skills. Some users mentioned it took over 300 hours to tune the system to their needs, although those with Elastic expertise in-house may find it easier to manage.
Components of the ELK Stack:
- Elasticsearch: A search and indexing engine optimized for time-series data.
- Logstash: A tool for collecting, processing, and refining data from various sources.
- Kibana: A visualization platform that enables interactive exploration of data within the stack.
- Beats: Lightweight agents that collect and forward data to the stack.
ELK Stack as a SIEM solution: While the ELK Stack offers log aggregation, processing, and visualization, it is not a fully-fledged SIEM system.
Missing features:
- Correlation engine: The free version of the ELK Stack lacks a built-in correlation engine, but open-source alternatives like Yelp/Elastalert can provide this functionality.
- Built-in reporting or alerting: This absence limits the ELK Stack’s effectiveness for SIEM and general IT operations.
- Pre-configured security rules: The lack of built-in security rules adds to the resource and operational overhead of using the stack for security monitoring.
Datadog
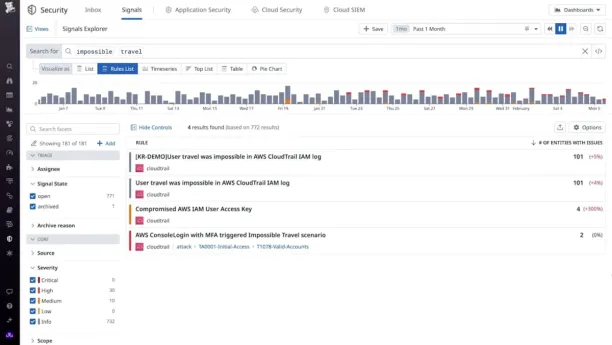
DataDog does offer log ingestion, but it is not its primary focus.
DataDog emphasizes its integration with other parts of the platform, which can be useful, though it is not frequently used between application performance monitoring (APM), Metrics, and logs.
Datadog ingests logs into specific fields for searchability, which allows users to filter and analyze logs effectively. For example, you can quickly identify which application is producing the most ERROR logs by applying filters before making a detailed query. This filtering process helps in narrowing down the data to what is most relevant.
However, a key limitation is that once a subset of logs is filtered, DataDog lacks capabilities for creating visualizations or plots from the data, limiting the ability to generate complex, customizable reports or dashboards directly from the logs.
While Datadog Logs is functional and works well for log management, it does not offer much beyond what can be achieved with an ELK stack setup.
Key features of SIEM solutions
A strong SIEM solution consists of several essential parts that work together to provide thorough security monitoring.
1. Log management
SIEM systems gather and analyze logs from various sources across the organization, such as servers, network devices, firewalls, and cloud applications. The goal is to identify unusual patterns that could signal a potential threat. Many SIEM tools also use threat intelligence feeds to help detect and block new cyber threats.
2. Event correlation
SIEM tools combine data from multiple systems and look for patterns. For example, if there’s suspicious activity from a compromised account and unusual network traffic, the SIEM can link these events and trigger an alert for security teams to investigate. Event correlation helps uncover hidden threats that might not be obvious on their own.
3. Incident response and monitoring
SIEM systems continuously monitor digital and on-premises environments to detect threats early and minimize damage. The analysis is displayed on a central dashboard, and alerts are sent to security analysts based on preset rules.
Some SIEM solutions also include automated response features. For example, if malware is detected, the SIEM can automatically isolate the infected system, allowing analysts to focus on more complex tasks. Automation helps speed up responses and improves overall efficiency.
SIEM use cases
Security teams use SIEM solutions for a wide variety of applications.
Threat detection and response
One of the primary uses of a SIEM solution is detecting and responding to security threats. SIEM systems enable security teams to identify and address even the most sophisticated attacks, including insider threats, and multidomain attacks, which span multiple areas of an organization’s infrastructure.
Forensic analysis
Forensic analysis in SIEM involves reviewing and analyzing logs and data after a breach to understand the attack’s scope, tactics, and timeline. It helps security teams trace back the activities to identify how the attack was carried out and which systems were affected.
Real-time security data visualization
Presenting security data in visual formats such as dashboards, graphs, and charts to make it easier for security teams to monitor and respond to threats.
SIEM solutions with real-time data visualization present security events in a way that allows security teams to quickly assess potential threats, identify trends, and react more efficiently.
Compliance management
Compliance management is one of the key functions of SIEMs. It helps organizations meet regulatory requirements by automating the collection of relevant logs and generating compliance reports for GDPR, HIPAA, and PCI-DSS.


Comments
Your email address will not be published. All fields are required.