As a CISO in a highly regulated industry with ~2 decades of cybersecurity expertise, I listed the top 5 open-source security orchestration, automation, and response (SOAR) tools based on their features, usability, and user feedback:
| Tool | What is it | Focus |
|---|---|---|
| n8n | Workflow engine for SOAR | Customizable, API-driven automation |
| StackStorm – st2 | Event-driven SOAR infrastructure | Infrastructure-level auto-remediation and DevOps automation |
| Shuffle | Full SOAR platform | No-code security response orchestration for SOC teams |
| TheHive Project – Cortex | Threat intel & case management tool | IOC analysis and structured case management |
| Tracecat | Full SOAR platform | Scalable, multi-tenant SOAR playbooks |
Features
| Tool | Python-to-no-code | Mitre mapping | No-code builder | Trigger workflows |
|---|---|---|---|---|
| n8n | ✅ | ✅ | ✅ | ✅ |
| StackStorm – st2 | ❌ | ❌ | ✅ | ✅ |
| Shuffle | ✅ | ✅ | ✅ | ✅ |
| TheHive Project – Cortex | ❌ | ✅ | ✅ | ✅ |
| Tracecat | ✅ | ❌* | ✅ | ✅ |
*MITRE ATT&CK labels are available.
n8n
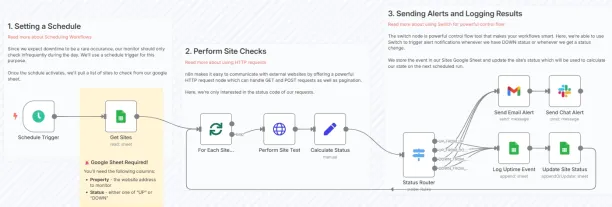
n8n is a self-hostable automation platform designed to accelerate the development of security workflows with a visual low-code interface.
n8n can be used Security Operations (SecOps) to automate detection, response, and enrichment tasks by integrating across their existing stack — including SIEMs, ticketing systems, and threat intelligence platforms.
Licensing model: Source-available, but not fully open source While n8n offers a free Community Edition with source code available, it’s not considered fully open source under the Open Source Initiative’s definition due to its Sustainable Use License.1
✅What the n8n community edition includes:
- Debug in the editor: Copy and pin execution data while working on a workflow.
- One day’s workflow history: 24 hours of workflow history allows you to revert to earlier workflow versions.
- Custom execution data: Save, find, and comment on the execution metadata.
❌What is restricted to pro & enterprise plans:
- External storage: Offload execution data to external services like S3 or GCS.
- Log streaming: Stream real-time logs to observability tools (basic logging is included).
- Single sign-on (SSO): Integrate with identity providers such as SAML or OAuth.
- Workflow sharing: Only the instance owner and the creator can access workflows and credentials; team collaboration requires an upgrade.
- Git integration: Manage workflows with version control using Git.
- Extended workflow history: The community edition provides only 24 hours of history with registration.
SOAR use cases with n8n:
| Use case | Example workflow in n8n |
|---|---|
| SIEM Alert Enrichment | Enrich alerts using MITRE ATT&CK and Qdrant to accelerate triage. |
| CrowdStrike Alert Handling + Jira | Detects, enriches, and creates incident tickets from CrowdStrike alerts. |
| Phishing Email Analysis (URLScan.io + VirusTotal) | Analyzes reported emails for malicious links or indicators. |
| Analyze Suspicious Emails with ChatGPT Vision | Uses LLMs to inspect suspicious email content and automate decisioning. |
| Exposed AWS IAM Key Detection on GitHub | Scans GitHub commits to detect and alert on exposed secrets. |
| Authentication IP Monitoring | Flags anomalous login IPs from SaaS alerts for immediate attention. |
| Suspicious Login Detection | Detects login anomalies and helps trigger downstream investigations. |
Source: N8n2
Pros
- Developer-friendly:
- It supports JavaScript and Python for workflow customization, and it can use the external library for JavaScript in self-hosted setups.
- Provides a “Code Node” for writing custom logic in JavaScript, offering flexibility for developers.
- Integration capabilities: Works seamlessly with APIs and supports importing cURL commands for transferring data specified with URL syntax.
- Scalable pricing: The cloud pricing model doesn’t charge based on the complexity of workflows.
- Deployment: Works seamlessly with Docker for straightforward setup and scalability.
- No-code: n8n’s backend offers no-code features.
Cons
- Not a full-fledged SOAR:
- No native case management
- No built-in alert correlation or entity behavior profiling
- Steeper learning curve: Setting up OAuth clients for services like Google Sheets is more complex than SaaS products like Zapier and Make.
- Limited cloud features: The cloud version of n8n lacks certain functionalities available in the self-hosted version, such as node package manager.
StackStorm – st2
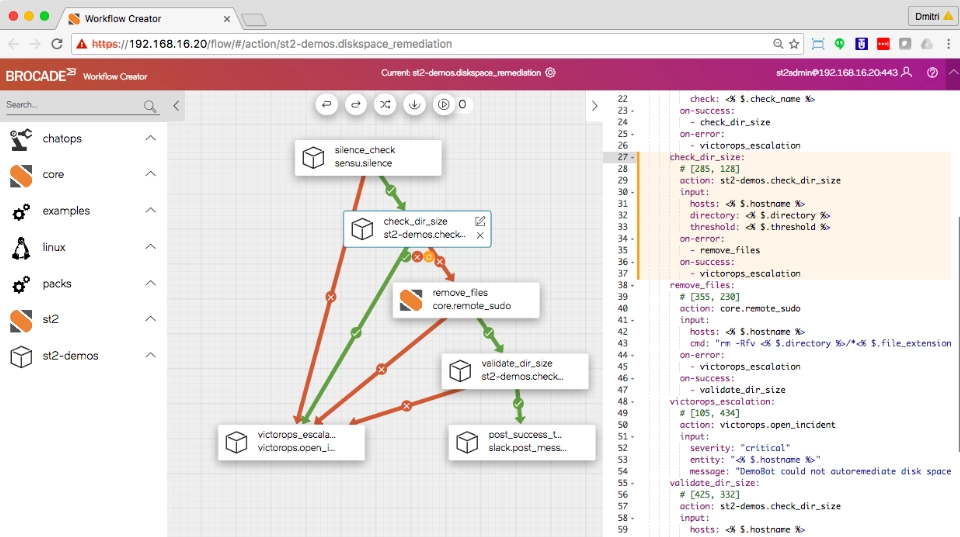
Source: GitHub3
st2 automates auto-remediation, incident responses, troubleshooting, and deployments for DevOps. St2 offers a rule automation engine, workflows, and 160 integration modules.
St2 is used by enterprises, including Cisco, Target, and Netflix. For example, Netflix used StackStorm, a remediation platform, to host and execute its runbooks.4
Integration costs: The total monthly costs st2 for the following third-party integrations are ~$28 such as AWS, PackageCloud, stackstorm.com, forum.stackstorm.com, Zoom account, Packet.net, Domain Certificates, and OpenVPN license.5
Open-source version features:
- Slack integration: ✅ Available
- AWS integration: ❌ Not available
- Workflow designer: ❌ Not available
- Professional support: ❌ Not available
- Network automation suites: ❌ Not available
Pros
- Custom workflows: Users say they can effectively integrate any script you or others have created into custom workflows.
- Strong plugin ecosystem: StackStorm supports several integrations with third-party tools such as NetBox, Splunk, and more.
Cons
- Kubernetes support: St2 has no native Kubernetes support.
- Steep learning curve: Requires a solid understanding of Python and YAML to create and manage workflows, which might be a barrier for teams with limited coding expertise.
- Limited active updates: The frequency of updates and maintenance is low.
Read more: Most common SOAR use cases.
Shuffle

Source: Medium6
Shuffle is an open-source SOAR. It helps automate workflows and move data throughout a company via 200+ plug-and-play Apps.
Shuffle utilizes OpenAPI, an existing Web API standard, and provides access for creating apps with over 11,000 endpoints.
Key features:
- SIEM to ticket: Send your SIEM alerts to Shuffle. Network logs are transmitted to the SIEM and sent to your case management system.
- 2-way ticket synchronization: Sync tickets between two systems. Different stakeholders (e.g. supplier or department) and your internal team will have restricted access to particular tickets.
It’s a strong choice for organizations with small to mid-sized teams looking for a free plan with unlimited workflows, apps, and users. Its on-prem enterprise version plan starts at $960/mo for 8 CPU cores.
Free edition vs paid edition (cloud-hosted):
| Free version | Paid version | |
|---|---|---|
| Plan | Free | Pay as you go |
| App runs/mo | 10k | 100k |
| Workflows | 10 | No limit |
| Apps | 50 | No limit |
| Users | 5 | No limit |
| Customer service | – | No limit |
Pros
- Workflows and playbooks: Reviews show that workflows and playbooks are easy to deploy and use.
- Third-party integrations: Connecting Wazuh notifications with Jira is seamless.
- Installation: Easy-to-install setup, especially with Docker.
Cons
- Backend procedures: Navigating backend procedures in the docker environment can be difficult.
- Containerized environment integrations: Integrations with containerized environments are problematic.
- Performance issues: Shuffle has server capacity constraints, which slowed workflow execution.
TheHive Project – Cortex
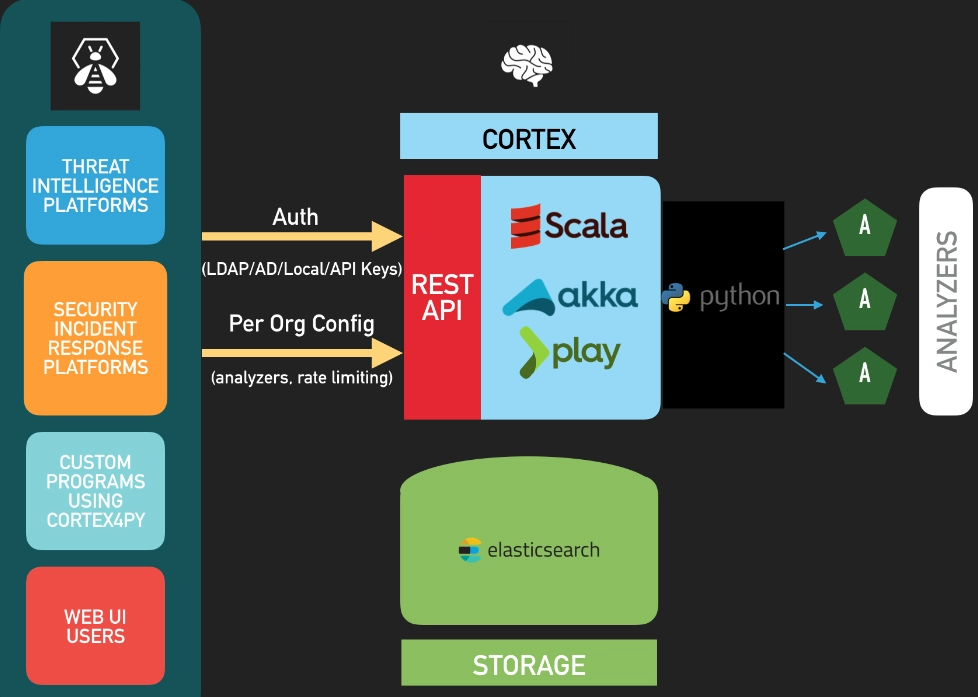
Source: GitHub7
Cortex streamlines threat intelligence, digital forensics, and incident response by providing a unified tool for analyzing observables at scale.
These observables—such as IP addresses, email addresses, URLs, domain names, files, and hashes—can be assessed either individually or in bulk through an intuitive web interface.
Free edition vs paid edition:
| Feature | Open-source | Paid: Gold | Paid: Platinum |
|---|---|---|---|
| Number of users | 2 | Pay per user | Pay per user |
| Number of organizations | 1 | Pay per organization (up to 5) | Pay per organization (no limit) |
| Multi-tenancy | ❌ | ✅ | ✅ |
| Cortex servers | 1 | up to 5 | No limit |
| MISP servers | 1 | up to 5 | No limit |
| Define custom views | ❌ | ✅ | ✅ |
| Custom knowledge base | ❌ | ✅ | ✅ |
| Clustering support | ❌ | ✅ | ✅ |
Pros
- Network monitoring: Cortex can monitor and analyze massive monitoring information at scale.
- Database integrations: Cortex seamlessly integrates with MongoDB for data analysis and forecasting of current trends.
- Integration with threat intelligence tools: Strong integration capabilities with Cortex and MISP (Malware Information Sharing Platform).
Cons
- Transition to paid model: The Hive5 release has moved to a commercial licensing model, potentially alienating users who relied on the fully open-source framework.
- Steep learning curve: The platform configurations can be complex to operate for beginners
- Community support: The open source community has limited support and updates.
- UI: The interface could be more user-friendly.
Tracecat
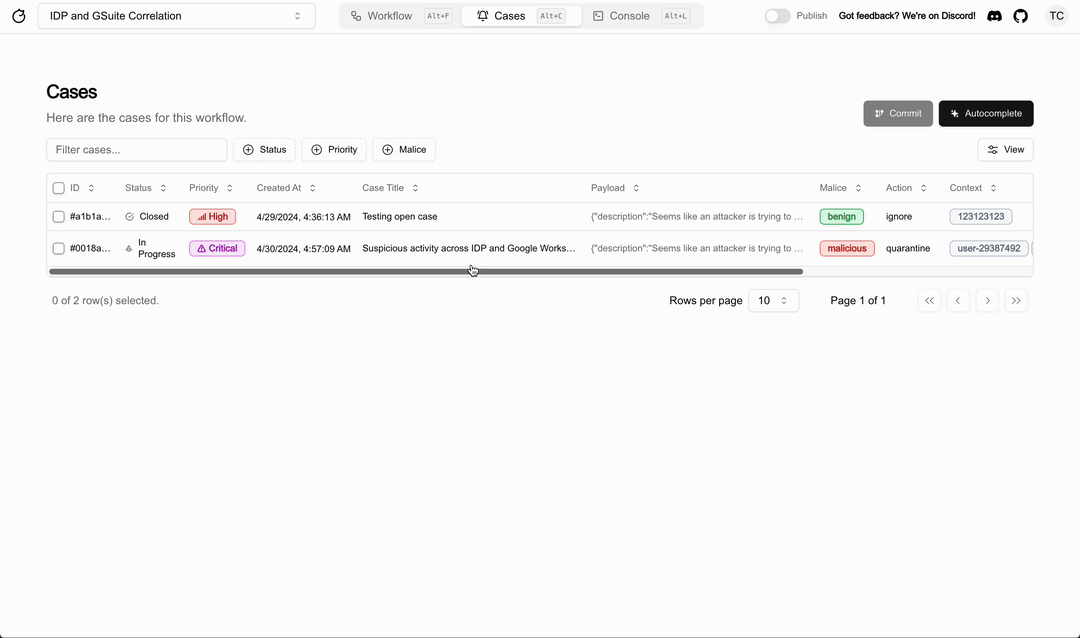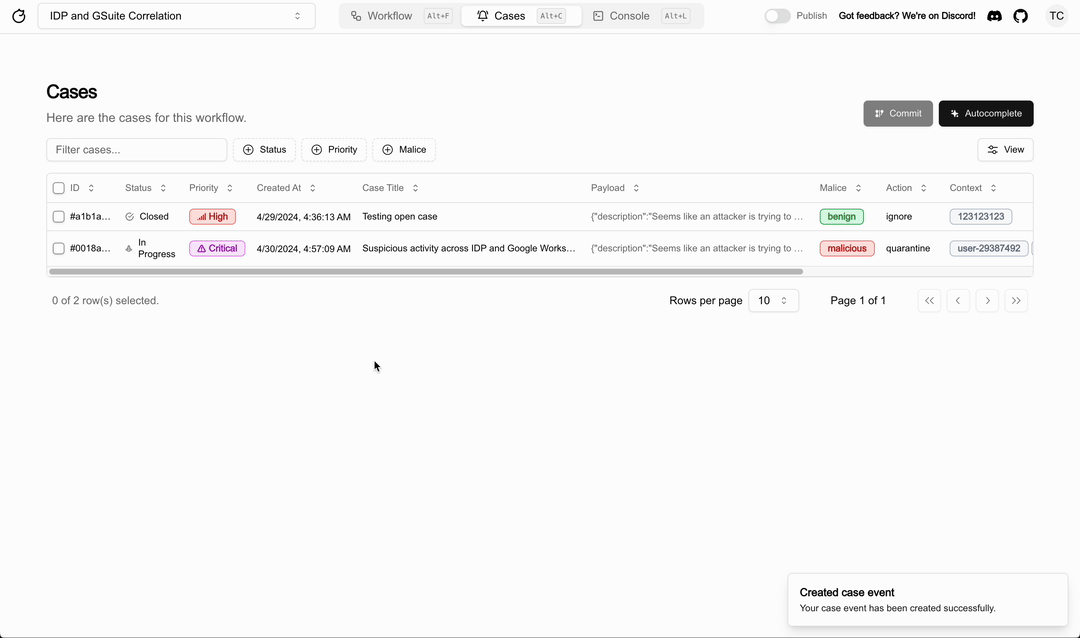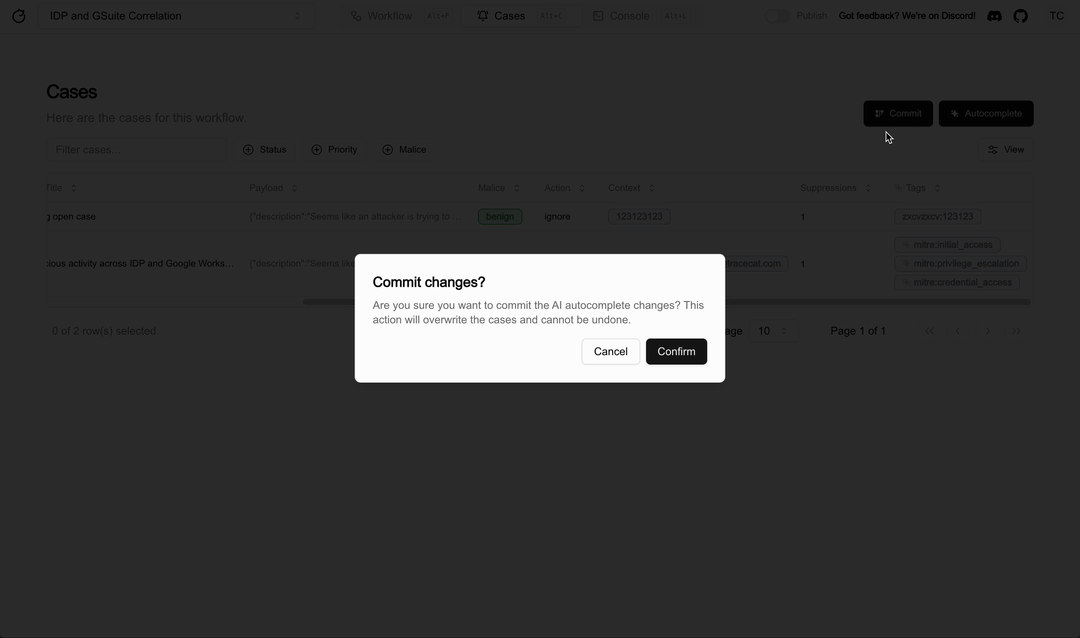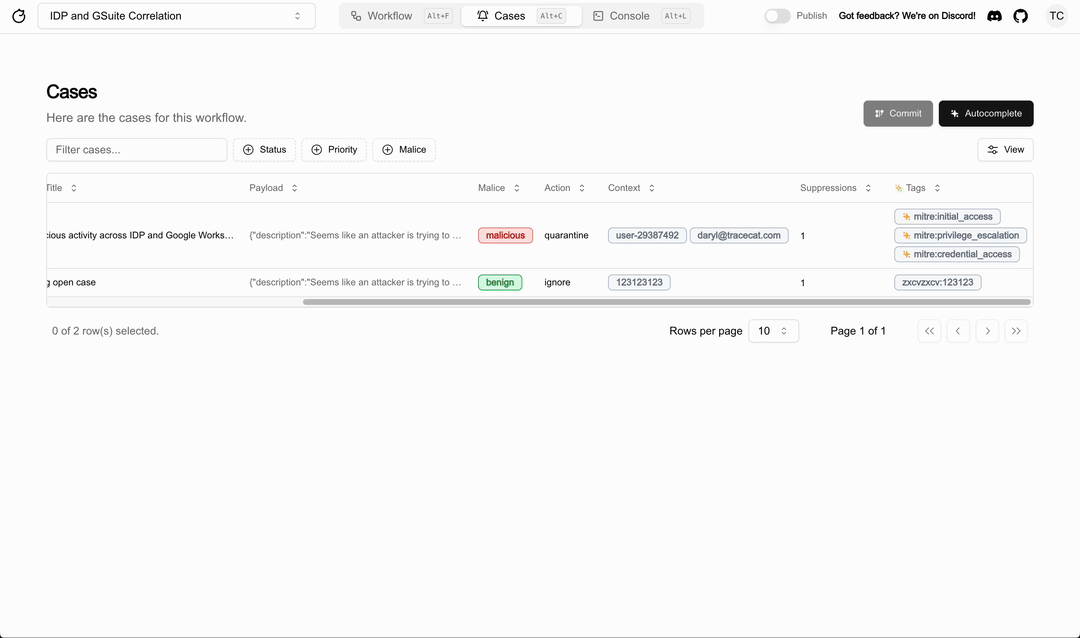
Source: 8
Tracecat is an open-source Tines/Splunk SOAR replacement for security engineers. Its Managed Detection and Response (MDR) feature integrates work processes into any security solution.
Tracecat enables security users to build automation using both:
- No-code drag-and-drop UI
- Configuration-as-code (e.g. Ansible / GitHub Actions)
Key considerations: The developers focus on making Tracecat available to understaffed small- and medium-sized organizations.
Thus, it is also user-friendly for nontechnical personnel since it provides Python-to-no-code and no-code workflow builder capabilities.
Additionally, Tracecat is also used by large-scale companies like Datadog, Netflix, and Stripe.
Open source features (self-hosted):
- Automation features:
- Workflow automation
- Pre-built and custom integrations
- REST API for managing workflows
- Security features:
- Role-based access controls
- Single sign-on (SSO)
Enterprise features (self-hosted):
Includes all open-source features, plus:
- Integrations:
- API health monitoring
- Webhooks
- Automation:
- Semantic search and clustering
- Automated entity extraction
- Automated labeling (e.g., MITRE ATT&CK)
- Professional support:
- SLAs with private chat (Slack, Microsoft Teams) and email support
What is SOAR?
Security orchestration, automation, and response (SOAR) tools coordinate, execute, and automate processes between several people and products on a single platform.
This enables organizations to respond quickly to cybersecurity threats while also observing, and preventing future incidents.
For more: Most common SOAR use cases.
Why do organizations need SOAR tools?
Organizations need SOAR tools to enhance their ability to respond to security incidents quickly and efficiently, especially as the cost of a data breach continues to rise.
In 2024, the global average cost of a data breach is ~$4.9M—a 10% increase over the previous year and the highest amount ever.9
Open source security orchestration, automation, and response (SOAR) tools coordinate, execute, and automate tasks between various people and software within a single platform. With these tools:
- Security Operations (SecOps) integrate workflow development between security engineering and SOC teams.
- Security Engineers (SecEngs) create automation with open source connectors, configuration-as-code, and a templating language.
This enables organizations to analyze diverse data to track and respond to data breaches and cyber attack vectors oftentimes manually, resulting in a more proactive approach to security operations.
How to select an open source SOAR tool
- Evaluate the vendor’s reputation. The amount of stars and collaborators on GitHub reflects the tool’s popularity. Tools with more GitHub stars and contributors will get advantages like:
- Stronger community support
- Larger user base: Tools with high GitHub stars typically have a large and active user community, which means more people to ask for help, share knowledge, and discuss best practices.
- More frequent updates: High contributor counts often lead to more frequent updates and improvements, ensuring the tool stays up-to-date with the latest technologies and standards.
- Collaborative problem-solving: A strong community of developers can assist in identifying bugs, sharing solutions, and contributing to feature development of the open source SOAR tool.
- Analyze the software’s features: Most open source SOAR platforms include incident response, threat hunting, and threat intelligence capabilities. However, if the company expects to utilize the network security tool for numerous purposes, consider a more comprehensive solution.
For example, a company looking to identify potential security threats before they disrupt business operations may choose a system with security information and event management (SIEM) features.
Read more: SIEM tools.
- Compare open-source and paid alternatives: Open-source solutions usually have restricted integrations, less specialized capabilities, and lack of expert support. Companies seeking a more personalized paid solution should look for the following in a SOAR platform:
-more comprehensive features (for example, microsegmentation, cloud security posture management)
– extensive documentation
– a dedicated team to promptly address and fix security problems.
Further reading
- Role-based Access Control (RBAC)
- Network Segmentation: 6 Benefits & 8 Best Practices
- 80+ Network Security Statistics
External Links
- 1. Sustainable Use License | n8n Docs .
- 2. https://n8n.io/workflows/categories/secops/
- 3. GitHub - StackStorm/st2: StackStorm (aka "IFTTT for Ops") is event-driven automation for auto-remediation, incident responses, troubleshooting, deployments, and more for DevOps and SREs. Includes rules engine, workflow, 160 integration packs wit.
- 4. Introducing Winston — Event driven Diagnostic and Remediation Platform | by Netflix Technology Blog | Netflix TechBlog. Netflix TechBlog
- 5. StackStorm Expenses · Issue #36 · StackStorm/community · GitHub.
- 6. Getting started with Shuffle — an Open Source SOAR platform part 2 | by Frikky | Shuffle Automation | Medium. Shuffle Automation
- 7. GitHub - TheHive-Project/Cortex: Cortex: a Powerful Observable Analysis and Active Response Engine.
- 8. GitHub - TracecatHQ/tracecat: Open source Tines / Splunk SOAR alternative. All-in-one automation platform (workflows, tables, cases) for security and IT teams..
- 9. Cost of a data breach 2024 | IBM.


Comments
Your email address will not be published. All fields are required.