Network security statistics show that 85% of responders from large companies with 5,000+ employees said they use microservices. These companies should protect their services across API communications; however, traditional segmentation regulations based on IP addresses and ports will not protect microservices.
CISOs commonly search for open source micro segmentation tools that can:
- enforce network security policies between APIs to block the network traffic flow,
- enable role-based access controls (RBAC) within a mesh to define user & device permissions.
Discover the top 10 open source micro segmentation tools based on GitHub stars and our analysis:
Top 10 open source micro segmentation tools
Table 1: Market presence
| Vendor | # of GitHub stars | # of GitHub contributers | Supported languages | Key integrations | Source code |
|---|---|---|---|---|---|
| Istio | 35,098 | 1,025 | Go, Shell, Makefile, CSS, HTML, Python | cert-manager, Grafana, Jaeger, Kiali, Prometheus, SPIRE, Apache SkyWalking, Zipkin, Third-party load balancers | Istio |
| HashiDays | 27,874 | 910 | Go, MDX, SCSS., JavaScript, Handlebars, Shell | CloudKinetics, Insight, 3Cloud, Atos, Microsoft Azure, Oracle Cloud Infrastructure, AWS, ACCUKNOX | Consul |
| Cilium | 18,731 | 745 | Go, C, Shell, Makefile, Dockerfile, Smarty | AWS, Google Kubernetes Engine (GKE), Dataplane V2, Anthos, Azure CNI | Cilium |
| Linkerd | 10,453 | 354 | Go, Rust, JavaScript, Shell, Smarty, Makefile | ExternalDNS, Consul, Istio, Knative | Linkerd2 |
| Flannel | 8,530 | 235 | Go, Shell, C, Makefile, Dockerfile | Not specified | Flannel |
| Tigera | 5,536 | 345 | Go, C, Python, Shell, Makefile , PowerShell | OpenStack, Flannel | Calico |
| Meshery | 4,927 | 605 | JavaScript, Go, Mustache, CSS, Makefile, Open Policy Agent | AWS, Kong . OpenEBSMesh. SPIFFE. Prometheus | Meshery |
| Kumahq | 3,535 | 101 | Go, Makefile, Shell, Mustache, JavaScript, HTML | Native API management solutions | Kuma |
| Open Service Mesh | 2,583 | 374 | Go, Shell, Makefile, C++, Starlark | Dapr, Prometheus, Flagger, Pyroscope | osm |
| Traefik Mesh | 2,004 | 31 | Go, Makefile, Dockerfile | Amazon EKS, K3S, Azure Kubernetes Service, Google Kubernetes Engine | mesh |
Vendor selection criteria:
- Number of GitHub stars: 2,500+
- Number of GitHub contributors: 30+
- Update release: At least one update was released in the last week.
- Sorting: Sorted based on GitHub Stars in descending order.
Read more: Micro segmentation examples, micro segmentation use cases, micro segmentation in cloud, open source network security software.
1. Istio
Istio is an open platform that helps companies control API communication by connecting microservices.
Users can leverage RBAC capabilities with Istio, which enables micro segmentation of services within an Istio mesh by setting:
- Roles — to define user permissions (or a combination of permissions) that specify the activities a user may execute on a system. This enables organizations to categorize roles depending on jobs and identities.
For example, administrators may describe the role as “user Mert calling from Bookstore frontend service”, resulting in a combined role identity of the calling service (Bookstore frontend) and the end user (Mert).
- Access restrictions — to create RBAC concepts.
For example, a database administrator may create access restrictions that state DB admins have full access to the database’s backend services, but a web client can only view the frontend service.
Figure 1: Istio micro segmentation with RBAC architecture
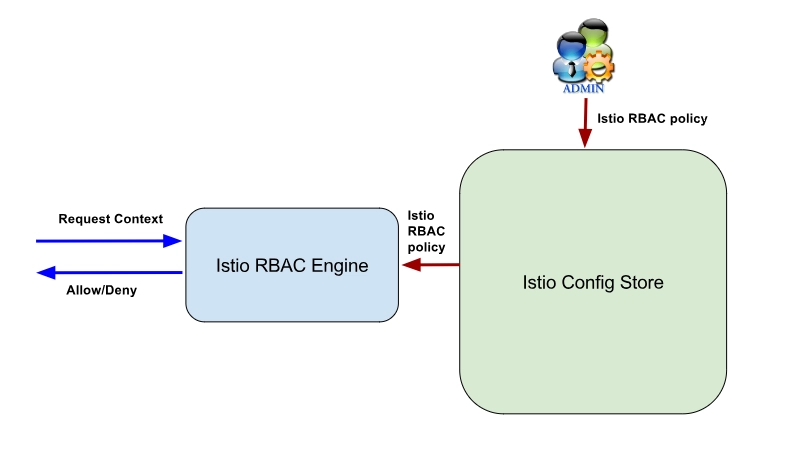
Source: Istio1
Here is a role “products-viewer” with read (“GET” and “HEAD”) access. Thus, a user who is assigned the “products-viewer” role can submit a request and receive a response to the microservice in the “default” namespace.
Figure 2: Microservice query example with Istio
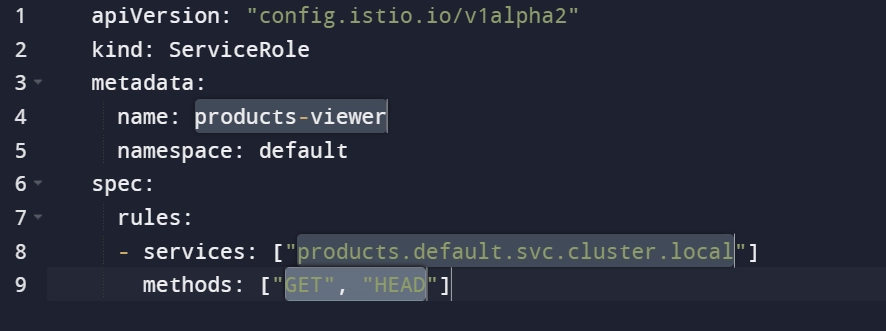
Source: Istio2
Read more: Open source RBAC, RBAC use cases, RBAC examples.
2. Consul
Consul by HashiCorp is a microservice networking solution with micro segmentation features that allow teams to manage API communication. Consul provides services such as microservice discovery and microservice mesh.
With Consul, administrators can manually define data requests using the command line or the API, or can automate the “microservice discovery and microservice mesh” process in Kubernetes. This ensures that service-to-service communication is authorized.
Video 1: Introduction to micro segmentation with mutual proxy authentication to HashiCorp Consul
Source: HashiCorp3
3. Cillium
Cilium can help organizations by enabling multi-cluster Kubernetes deployments for service discovery, micro segmentation, and network security policy management.
Cilium can implement security rules based on service/container identity rather than an IP address for identification. This allows administrators to use policies at various tiers to control traffic within their Kubernetes cluster.
To understand how Cillum can provide hands-on micro segmentation implementations, consider the following example: a couple has decided to go on vacation with other passengers. Some important aspects for the example:
- Namespace “Economy” for people in the Economy class.
- Business class passengers- namespace “Business”
- First-class passengers – namespace “First”
- Passengers can only access services for their class (e.g. namespace)
Figure 3: Administrators creating three distinct namespaces with Cillium
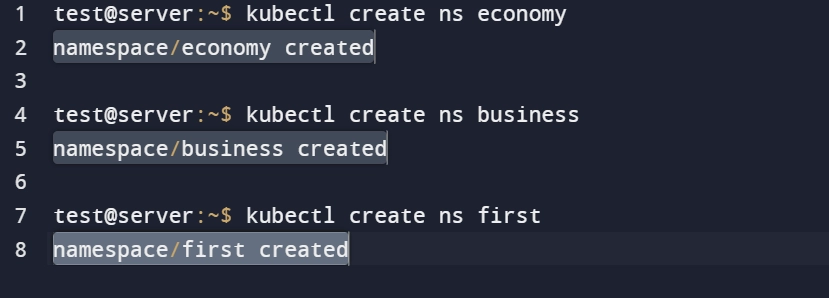
Figure 4: Administrators creating the services each user accesses in that namespace (e.g.economy) with Cillium
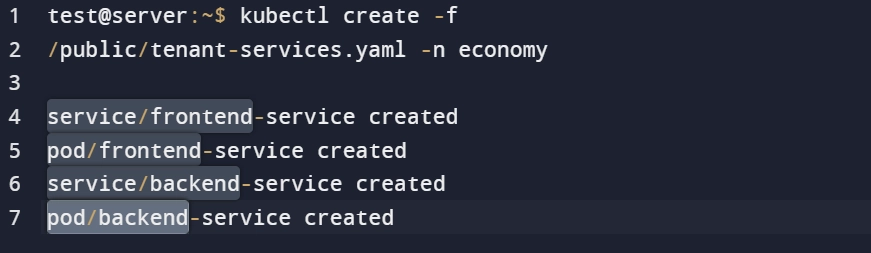
Using the network editor, administrators can manually accept the following communication patterns:
- Ingress from workloads inside the same namespace (economy).
- Egress to workloads inside the same namespace (economy).
Thus, when an economy-class customer requests a service within the same namespace, Cillium will give a permit.
Figure 5: Micro segmentation policy in action with Cillium
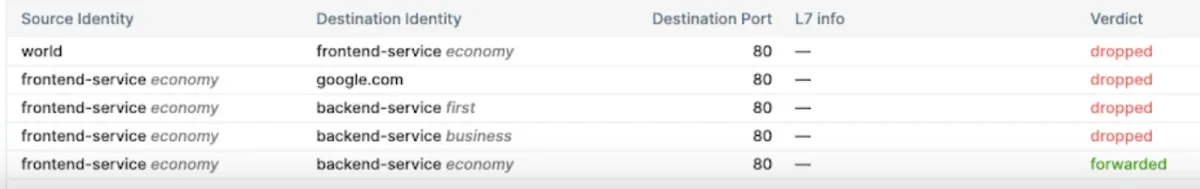
Source: Isovalent4
4. Linkerd
Linkerd is a service mesh software layer with micro segmentation capabilities that facilitates service-to-service communication between services or microservices via a proxy.
Video 2: What is Linkerd
Source: Linkerd5
5. Flannel
Flannel is an open source virtual network project built for Kubernetes. Flannel enables administrators to enforce policies based on how traffic is routed between containers.
Note: Flannel is more focused on segmenting networks; it does not provide a policy enforcement feature for regulating how containers are networked to the host, However, it provides a plugin container network interface (CNI) for configuring containers.
6. Calico
Calico by Tigera is an open-source networking project that allows Kubernetes and non-Kubernetes/legacy workloads to maintain isolated networks based on zero trust architecture. Users who need to segment containerized systems in their business can use Calico’s network policies to isolate, protect, and secure numerous security domains, including Kubernetes workloads, namespaces, tenants, and hosts.
Calico offers microservices for controlling API communications to stop unauthorized communication at three levels: workload isolation, namespace isolation, and tenant isolation. Calico’s components include:
- Calico CNI — is an L3/L4 networking control plane that allows administrators to configure microservers.
This helps to build isolated environments across host-to-host communication flows. Thus companies that use Calico CNI can create policy-based smaller segments between communication protocols to protect containers, Kubernetes clusters, virtual machines, and native host workloads.
- Calico network policy suite — is designed to enable setting policies while configuring microservices. With the Calico network policy suite, administrators can:
- Use “namespace” to assign permissions to certain IP addresses across isolated containers or virtual environments.
- Create network settings for divided networks that restrict IP addresses.
Video 3: Enabling workload micro segmentation with Calico
Source: Tigera6
7. Meshery
Meshery is an open source, cloud native microservice manager. While managing microservices administrators can create:
- Logical grouping — to segment environments to logically group relevant connections and credentials. This makes it easy to manage, resources rather than dealing with all of your connections separately.
- Resource sharing — to connect environments to allocate Workspaces. Thus, team members may share resources.
Video 4: Meshery design
Source: Meshery7
8. Kuma
Kuma is an open-source control plane for service mesh that provides microservice communication and routing.
With Kuma, organizations can service meshes based on identity and encryption. For example, administrators can allow/deny incoming requests in Kubernetes.
Figure 6: Kuma user interface
Source: Kuma8
9. Open Service Mesh (OSM)
Open Service Mesh (OSM) is a cloud-native service mesh that enables users to manage microservices.
OSM runs an Envoy-based control layer on Kubernetes, can be configured using APIs. With OSM users can:
- Send deny/allow requests for network traffic communication between APIs.
- Secure service-to-service communication across clusters.
- Define fine-grained access control policies for services.
Video 5: Defining fine-grained access control policies for services with Open Service Mesh (OSM)
Source: Microsoft Azure9
10. Traefik Mesh
Traefik Mesh is an open source service mesh with micro segmentation features. It is container-native and runs in your Kubernetes cluster.
Video 6: Traefik Enterprise demonstration of microservices
Source: 10
How to select an open source micro segmentation tool: 3 factors to consider
Key factors to consider while selecting an open source micro segmentation tool:
- Evaluate the tool’s reputation: The number of GitHub stars and contributors shows the popularity of open-source technology. Tools with higher popularity will receive more up-to-date industry news, trends, and developments and your organization will get more community assistance.
- Analyze the tool’s features: Most open source micro segmentation solutions include microservice management, policy enforcement, and login options. However, if your business intends to utilize the micro segmentation tool for several applications, you should search for a more comprehensive solution. For example, a company seeking identity-based access restrictions may select a system with role-based access control (RBAC) capabilities.
- Compare open-source vs closed-source alternatives: While open-source solutions often have limited integrations with less advanced functionality, deploying a more tailor-made solution with more comprehensive features (e.g., cloud security posture management (CSPM)) can be more productive for your company.
Here’s a list of closed-source micro segmentation tools that provide network change automation, configuration monitoring, network topology mapping, and cloud discovery and exposure management (CDEM) features.
Further reading
- Top 10 Micro segmentation Tools
- Top 10 NCCM Software: Based on 4,000 Reviews
- Role-based access control (RBAC)
- Network Segmentation: 6 Benefits & 8 Best Practices
- Network Security Policy Management Solutions (NSPM)
- Top 10 SDP Software Based on 4,000+ Reviews
- Top 10 Network Security Audit Tools Based on 4,000 Reviews
AIMultiple can assist your organization in finding the right vendor.
External Links
- 1. Istioldie 0.5 / Istio Role-Based Access Control (RBAC).
- 2. Istioldie 0.5 / Istio Role-Based Access Control (RBAC).
- 3. Introduction to HashiCorp Consul with Armon Dadgar - YouTube.
- 4. Zero Trust Security with Cilium.
- 5. What is the Linkerd service mesh? - YouTube.
- 6. Enabling Microsegmentation with Calico Enterprise. Tigera - Creator of Calico
- 7. Meshery The Kubernetes and Cloud Native Manager - an extensible developer platform | Meshery. The Meshery Authors
- 8. ”Kuma.io“. Kuma. 2024. Retrieved May 21, 2024.
- 9. How to use Open Service Mesh - YouTube.
- 10. Traefik Enterprise Demo: Connect, Secure, and Monitor Microservices at Scale - YouTube.


Comments
Your email address will not be published. All fields are required.