AppSec
Top 10 Application Security Metrics: Why Do They Matter?
Application security metrics are essential for providing a clear, quantifiable overview of an organization’s security posture. They assist organizations on: With 25% of all breaches directly coming from application vulnerabilities, monitoring security metrics is necessary. We highlight 10 metrics to help organizations measure, mitigate, and optimize their application security efforts.
Top 5 Vulnerability Scanning Tools in 2025
Considering the variety of vulnerability scanning and management tools, businesses may face challenges in choosing the most suitable solution. When choosing a vulnerability scanning tool, users often consider the tools’: Considering these, we evaluated the leading vulnerability scanning tools and highlighted their main features.
Top 10 Application Security Tools: Features & Pricing in 2025
Application breaches represent 25% of all security incidents.. Based on our extensive research and technical reviewer’s experience, we selected the top 10 application security tools. Within each vendor’s section, we outlined our rationale for our selection.
25+ Application Security Statistics & Trends in 2025
We present an analysis of current statistics in the field of application security. Our focus is on providing a clear and concise overview of the latest data, reflecting key trends and insights in this area of cybersecurity. The statistics compiled here are drawn from reputable, and up-to-date sources.
Vulnerability Testing: Use Cases, Importance & Process ['25]
With cyber threats becoming more common, it’s crucial for organizations to increase their defenses proactively. One of the key strategies in achieving security is through vulnerability testing.
Top 10 DAST Tools: Features & Benchmark Results in 2025
As the CISO of a high-growth company in a highly-regulated industry, application security is my top priority. I selected the top DAST tools based on my experience and our research efforts.
Top 7 Penetration Testing Use Cases with Examples in 2025
According to IBM’s “Cost of a Data Breach Report,” the average financial impact of a data breach has surged to an alarming $4.45 million per incident. With the growing reliance on digital platforms and accelerated digital transformation, penetration testing has become an indispensable tool for businesses seeking to fortify their cybersecurity defenses.
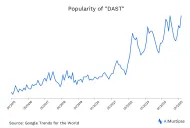
DAST: 7 Use Cases, Examples, Pros & Cons in 2025
DAST’s ability to mimic real-world cyberattacks and expose vulnerabilities in real time makes it a valuable asset in the cybersecurity toolkit. As seen in the graph, the popularity of DAST has increased significantly in the last five years.