Global cost of cybercrime is expected to reach $10.5 trillion annually by 2025, highlighting the need for stronger cybersecurity strategies. 1 Cyber threat intelligence (CTI) tools, also known as strategic threat intelligence tools, are crucial in modern cybersecurity since they provide detailed insights into both potential and active threats, enable faster and more effective incident responses, and ensure that organizations implement necessary network security measures.
This article explores the evolving landscape of cyber threat intelligence tools, defining the scope and capabilities of these tools.
Compare cyber threat intelligence platforms
| Vendors | Rating* | Deployment options | Starting price | Free trial |
|---|---|---|---|---|
| ManageEngine Log360 | 4.5 out of 22 | Cloud-Based On-Premises Hybrid | 300$/year | 50 GB free |
| Recorded Future | 4.5 out of 13 reviews | Cloud-Based On-Premises Hybrid | N/A | ✅ |
| ThreatConnect | 4.5 out of 4 reviews | On-Premises Air-gapped | N/A | N/A |
| Anomali ThreatStream | - out of 1 reviews | On-premises Air-gapped Cloud-Based | N/A | N/A |
| CrowdStrike | 4.6 out of 36 reviews | Cloud-Based On-Premises Hybrid | N/A | ✅ 15-day |
| Mandiant Advantage | 5.0 out of 1 reviews | Cloud-Based On-Premises Hybrid | N/A | ✅ 30-day |
| Rapid7 Insights | 4.4 out of 4 reviews | Cloud-Based On-Premises Hybrid | $175/mo | ✅ 30-day |
| Palo Alto Cortex XSOAR | 4.8 out of 19 reviews | Cloud-Based On-Premises Hybrid | N/A | ✅ 30-day |
| Bitdefender | 4.8 out of 4 reviews | Cloud-Based On-Premises Hybrid | €89.99/mo | ✅ 30-day |
Top cyber threat intelligence solution providers
1. ManageEngine Log360
ManageEngine’s Log360 is part of their comprehensive suite of IT management solutions, primarily focused on security information and event management (SIEM). It helps organizations secure their infrastructure by monitoring, managing, and analyzing network logs in real-time.

Key features:
- STIX/TAXII Feed Support: Log360 incorporates threat intelligence feeds from two well-known STIX/TAXII-based services:
- Hail A TAXII and AlienVault OTX.
- These threat feeds are downloaded daily from the cloud using HTTPS and updated on the local Log360 instance.
- Log Collection and Analysis: Collects logs from all network devices and correlates this data with updated threat feeds in real-time.
- Real-time Threat Detection: By correlating log data and threat intelligence, Log360 provides real-time detection and alerts for any suspicious or malicious activity within the network.
2. Recorded Future
Recorded Future provides a Threat Intelligence Cloud Platform that allows organizations to automate the gathering, assessment, and reporting of threat data for Security Operations Center (SOC) teams. The threat intelligence platform provides a free browser extension named Recorded Future Express. This extension provides real-time intelligence through risk scores and contextual information regarding IP addresses, domains, URLs, and CVEs.

Key features:
- Threat scoring: It relies on a series of risk guidelines. These guidelines draw from various sources including Recorded Future’s technical data gathering, threat feeds, and insights from sources like security researchers, social media, and forums. Each guideline is assigned a severity level. The overall risk score for an entity is determined by the highest severity level of the active risk guideline.
- MITRE ATT&CK mapping: Offers a uniform method for categorizing and detailing the different tactics and techniques utilized by adversaries throughout various phases of a cyberattack.
- Detection Rule API: Enables security professionals to systematically search for and download YARA, Sigma, and Snort rules developed by Recorded Future’s Insikt Group.
- Alerts: Offers real-time email notifications sourced from the Recorded Future API.
3. ThreatConnect
ThreatConnect provides a Threat Intelligence Operations Platform, serving as a centralized hub for collecting, correlating, and distributing threat intelligence data sourced from diverse sources. This platform, known as ThreatConnect TI Ops Platform, is versatile, offering deployment options that include on-premises, air-gapped, or AWS private cloud instances.

Key features:
- Incident response: ThreatConnect’s Playbook and Task Automation feature simplifies automation of tasks and procedures used by incident response (IR) teams through a low-code interface, allowing for drag-and-drop functionality.
- Risk assessment: Risks are prioritized in order of severity, considering both how likely they are to occur and the potential impact they could have.
- MITRE mapping: The MITRE ATT&CK App provides system-generated ATT&CK Tags, which help in identifying techniques and sub-techniques linked with Intrusion Set, Malware, Tactic, and Tool Groups. This feature allows users to utilize the ThreatConnect ATT&CK Visualizer for a deeper examination of the tactics, techniques, and procedures (TTPs) related to these specific Groups.
4. Anomali ThreatStream
Anomali ThreatStream offers a threat intelligence platform aiding security teams in identifying and addressing security threats. It achieves this by gathering and enhancing raw data from various threat intelligence sources, including curated feeds from Anomali Labs, open-source OSINT feeds, and information sharing and analysis centers (ISACs).
ThreatStream offers flexible deployment options, including software-as-a-service (SaaS) solutions, on premises within their own infrastructure, or in an air-gapped environment where network access to the internet is restricted.

Key features:
- AI engine: Provides a learning-based threat-scoring engine known as Macula. This engine is designed to analyze, predict, and categorize domain, IP, and URL observables that are fed into the ThreatStream platform.
- Sandbox: Automatically import IOCs from a Sandbox into ThreatStream and automate the detonation of phishing emails.
- Integrations: Integrates with various Endpoint Detection and Response (EDR), Security Information and Event Management (SIEM), and firewall products.
5. CrowdStrike
CrowdStrike’s threat intelligence combines automated technology with the expert insights. It monitors more than 230 adversaries, offering comprehensive profiles that detail their specific strategies, tactics, and procedures (TTPs).

Key features:
- Real-time threat detection: Leverages AI and conducts continuous threat hunting to identify and address security threats in real-time.
- Adversary intelligence: Offers insights on over 230 adversaries, such as nation-states, eCrime groups, and hacktivists, detailing their operations and strategies.
- Vulnerability intelligence: Prioritizes updating security patches by analyzing the specific threats targeting particular industries and regions, enabling targeted vulnerability management.
6. Mandiant Advantage
Mandiant Advantage provides a combination of threat intelligence, attack surface management, and managed defense services. Mandiant Advantage provides a range of threat intelligence products, including Mandiant Advantage Threat Intelligence Fusion, Mandiant Advantage Threat Intelligence Security Operations, and Mandiant Advantage Threat Intelligence Free.
Mandiant Advantage Threat Intelligence Free delivers insights into threat indicators. It also includes descriptions of publicly known vulnerabilities, featuring both Common Vulnerability Scoring System (CVSS) ratings and the more dynamic Exploit Prediction Scoring System (EPSS) severity metrics.

Key features:
- OSINT-based vulnerability views and scoring: Using Open Source Intelligence (OSINT) to collect data on vulnerabilities, the system then evaluates each identified vulnerability and assigns it a score, either numerical or qualitative, based on the level of risk and severity it poses.
- Alert prioritization and triage: Evaluating the seriousness of each. Once alerts are prioritized, alert precedes subjecting them to a triage process, which may involve actions like analyzing network traffic logs and inspecting system configurations.
7. Rapid7 Insights
Rapid7 is a cybersecurity platform offering a suite of security solutions, including SIEM (Security Information and Event Management), cloud security, vulnerability management, threat intelligence, dynamic application security testing, and SOAR (Security Orchestration, Automation, and Response).
Rapid7 Threat Command is a threat intelligence and response solution that collects and analyzes data from various sources, such as proprietary Rapid7 research, contributions from the community, and third-party threat intelligence feeds.
Their vulnerability management tool, InsightVM, is enhanced by Rapid7’s own vulnerability research, insights into global attacker behaviors, and extensive internet scanning data. InsightVM features include real-time security monitoring and the ability to assess assets across cloud, virtual, and container environments.
Rapid7 also offers a SIEM solution called InsightIDR, which delivers real-time threat hunting and response by integrating data from various sources such as logs, endpoints, and cloud services.
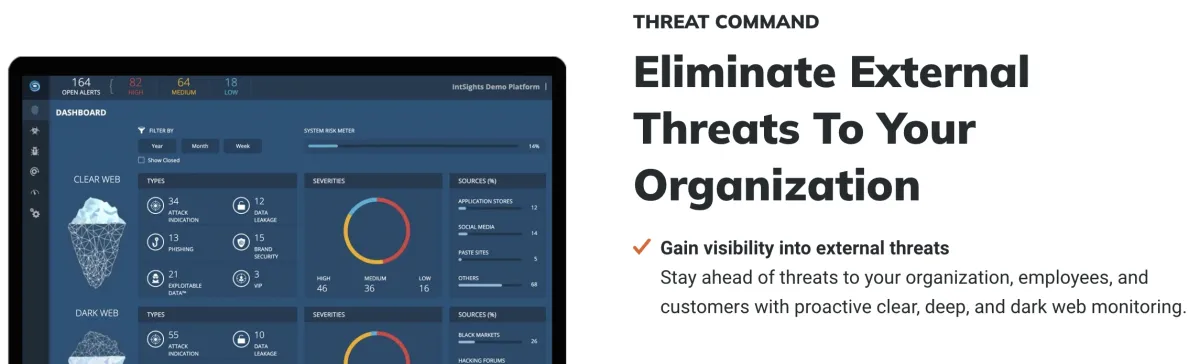
Key features:
- Digital risk protection: Scans the clear, deep, and dark webs for threat actors involved in activities like researching malware, and conducting phishing scams.
- Rapid remediation: Implements security measures to mitigate the threat, including updating security patches and quarantining compromised systems.
- Threat mapping: Provides a flexible asset mapping system to monitor and detect emerging potential attack vectors.
8. Palo Alto Cortex XSOAR
Palo Alto Cortex is a cyber security platform providing security tools tailored for SOC teams, which includes offerings such as Cortex XDR, Cortex XSOAR, Cortex Xpanse, and Cortex XSIAM. Cortex XSOAR provides capabilities for managing threat intelligence and is available for a 30-day free trial.

- Tenant management: Every tenant has the flexibility to configure its own collection of playbooks, integrations, as well as pre- and post-processing rules.
- Data separation: Users can manage child-tenant incidents and indicators from the main account, with each child-tenant’s data stored and encrypted independently in a separate Google Cloud project.
- Automated response to potential threats: Processes alerts from email accounts, activating the relevant playbooks and executing the corresponding actions.
9. Bitdefender
Bitdefender is a cybersecurity company offering various endpoint security solutions such as antivirus, container security, and Endpoint Detection and Response (EDR). The company’s solutions monitor both network and endpoint device environments to quickly detect anomalous activities and cyber threats.

Key features:
- Data collection: Monitors networks and endpoint devices—including desktops, laptops, and servers—to promptly identify and stop cyber attacks early in their development.
- Detection and response: Gathers and analyzes data from security devices such as workstations, servers, and containers, allowing for the correlation of events to identify security incidents.
- Threat investigation: Aids in organizing, analyzing, and addressing all security events noted and logged for the managed company over the previous 90 days.
What is cyber threat intelligence?
Cyber threat intelligence (CTI) is the information organizations use to understand the threats they face—past, present, and future. CTI offers more than just details about specific cyber threats; it also provides insights about the tactics, techniques, and procedures (TTPs) employed by attackers.
What is a threat intelligence tool?
A threat intelligence tool is a software application that helps organizations gather, analyze, and manage data on potential security threats. These tools process raw threat data about existing and emerging threats and the actors behind them, sourced from multiple sources.
They typically integrate seamlessly with other security systems, such as Security Information and Event Management (SIEM) systems, firewalls, and IPS tools, enhancing the organization’s ability to respond to threats effectively.
Important software to combine with cyber threat intelligence tools
Network security audit tools: Identify threats, vulnerabilities, and malicious activity to help companies mitigate cyber attacks and follow compliance with regulations.
NCCM software: Monitor information about your organization’s network devices by documenting network device configurations.
DSPM vendors: Provide network visibility into where to find sensitive data, who has access to it, and how it has been used across the cloud.
Network security policy management solutions (NSPM): Protect network infrastructure using firewalls and security policies against all threats.

Comments
Your email address will not be published. All fields are required.