Security Tools
DAST: 7 Use Cases, Examples, Pros & Cons in 2025
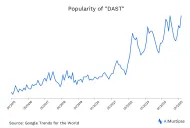
DAST’s ability to mimic real-world cyberattacks and expose vulnerabilities in real time makes it a valuable asset in the cybersecurity toolkit. As seen in the graph, the popularity of DAST has increased significantly in the last five years.
Jul 257 min read