An ASM software needs to meet the following requirements:
- Asset discovery to identify internet-facing hardware, software, and cloud assets.
- Prioritization to classify and filter risks.
- Remediation to fix ASM issues following the risks that have been prioritized.
- Monitoring to track vulnerabilities across network assets.
Based on the key features and market presence, I identified the top 10 open source attack surface management (ASM) software:
Market presence of top 10 open source ASM software
| Software | Specialization | # of stars on GitHub (k) | Supported languages |
|---|---|---|---|
masscan | Internet-scale port scanner | 23 | C |
| amass | Network mapping | 12 | Go, Lua |
| Nmap | Network mapping | 10 | C, Lua, C++, Shell, Python |
| cloudmapper | AWS attack surface mapping | 6 | JavaScript, Python, CSS, HTML |
| aquatone | HTTP-based attack surface management | 6 | Go, HTML, Shell |
| openvas-scanner | Vulnerability scanner | 3 | Rust, C |
| Findomain | Subdomain discovery (e.g. port scan, HTTP check) | 3 | Rust, Roff |
| assetfinder | Subdomain discovery | 3 | Go, Shell |
| dismap | Network mapping | 2 | Go |
| EasyEASM | Network mapping | 0 | Go |
Software are listed based on # of stars on GitHub (k) in descending order.
5 open source ASM software deep-dive
Tracking your asset inventory through traditional methods is nearly impossible due to constantly changing attack surfaces and distributed IT ecosystems. Open source ASM offers can help companies discover and govern these assets real-time visibility into attack vectors as they appear.
See real-life vendor demonstrations with examples:
Masscan
Masscan is a mass IP port scanner, which allows for extensive scanning of several computers, however, the solution does not provide in-depth scanning of single machines.
Masscan examples: See some commands to observe Masscan in action:
- Scan a single IP port: Execute an IP and single port scan of the targeted IP addresses by writing “./masscan 198.134.112.244 -p443” in the command line.
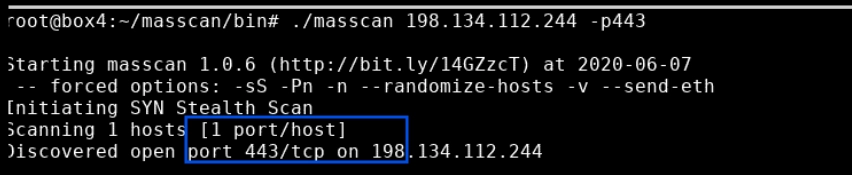
Masscan verified that port 443 is open at the specified IP address.1
- Multiple port scanning: Users can examine multiple ports or a set of ports on an IP subnet by running the following code at Masscan:
- ./masscan 198.134.112.240/28 -p80,443,25 # Multiple Ports
- ./masscan 198.134.112.240/28 -p1000-9999 #Port Range
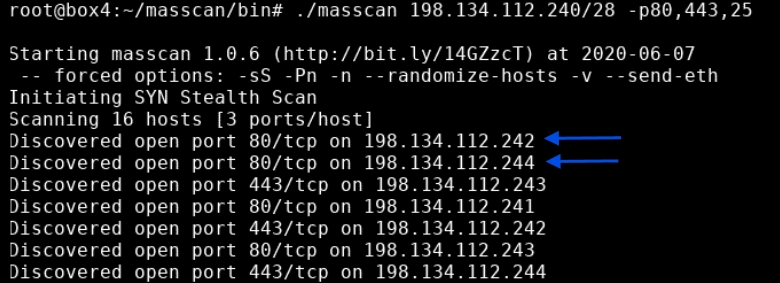
Masscan shows the number of hosts discovered, 7 in this example, and the ports open on which IP addresses.2
Amass
Amass is a command-line program that collects information from an organization’s websites utilizing open source information collecting technologies and active reconnaissance methods (e.g. monitoring network traffic and logs).
It runs from the command line with the following subcommands:
- amass intel – Discover targets for enumerations (listing all items in a collection)
- amass enum – Perform enumerations and network mapping
- amass viz – Visualize enumeration results
- amass track – Track differences between enumerations
- amass db – Manipulate the Amass graph database
Amass example:
- See how to run the “amassed Intel function” to list all of the elements in an organization (e.g. domains): The Amass intel subcommand can help you collect open source information about the organization and locate further root domain names. To view the possible choices for this subcommand, you type it into the terminal:
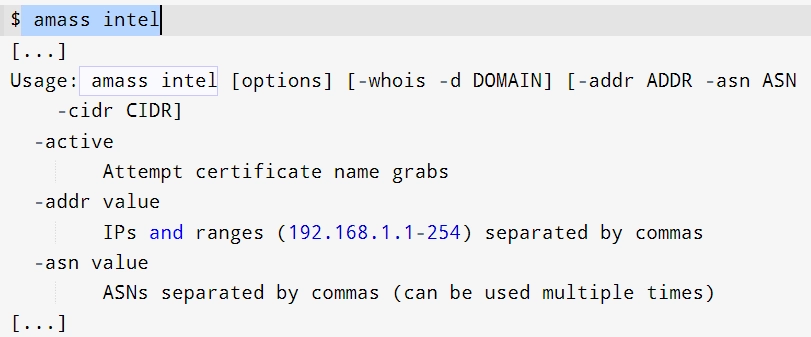
This subcommand will use information collecting techniques and data sources such as “WHOIS” (queries databases to find information about internet resources, such as IP addresses and domain names).
See data sources below: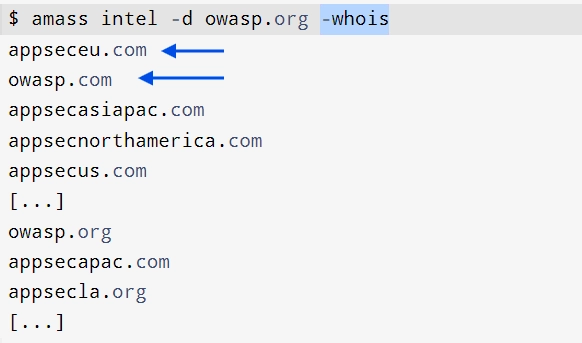
Nmap
Nmap is a network mapper that has become one of the market’s most widely used, free network discovery tools.
Nmap can:
- Identify active IP addresses, allowing you to differentiate between legitimate services and attackers.
- Provide data on your network, including live hosts, open ports, and each connected device’s operating system.
- Scan your server to simulate how a hacker would attack your website.
Nmap examples:
- Open port and domain name scanning: “scanme.nmap.org” will perform a scan for open ports on the domain name scanme.nmap.org.
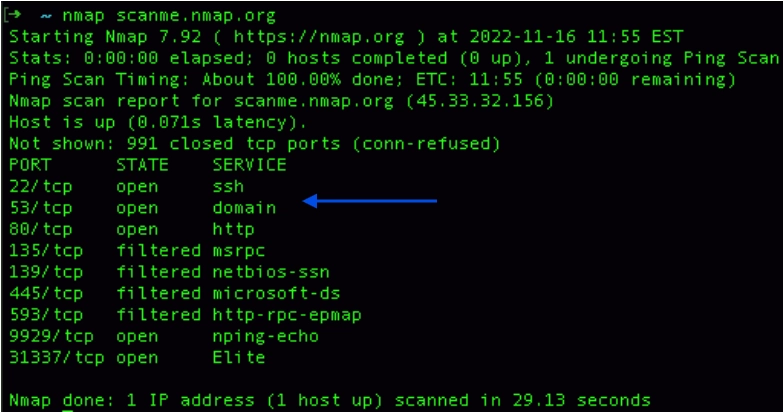
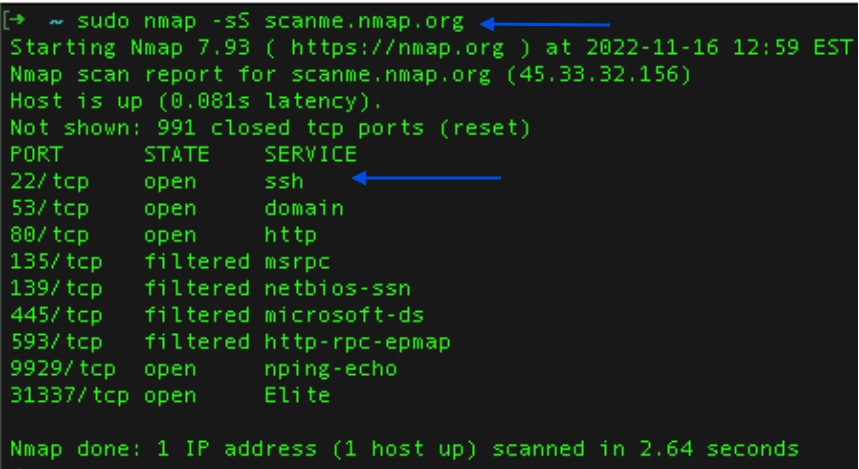
- Syn scanning (half-open scanning): For a basic syn scan, use “nmap -sS scanme.nmap” or “sudo nmap -sS scanme.nmap”.
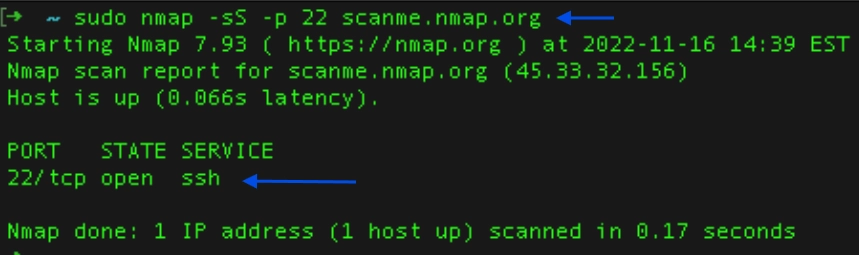
- Checking a specific port: Assume you expect to check if SSH (port 22) is open on your firewall. Then you can add -p (for port) and provide the port number to check: “Nmap -sS -p 22 scanme.nmap.org”.
Source: Blumira3
Cloudmapper
CloudMapper helps you analyze your Amazon Web Services (AWS) environments.
CloudMapper allows usERS to answer a variety of queries, including:
- Which resources are publicly available?
- Which resources can interact internally with each other?
- Is your architecture robust in the case of an availability zone failure?
- How many network regions does an account use? How complicated is it?
CloudMapper enables our engineers to double-check their understanding of what they’ve created and grasp alternative settings.
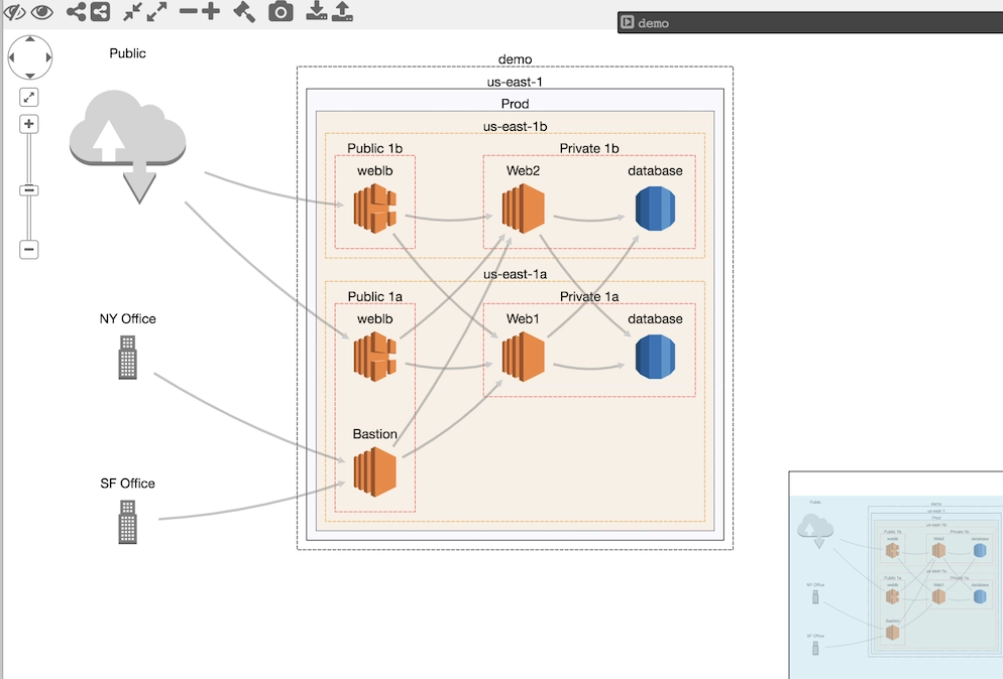
CloudMapper can help decrease security threats on our AWS infrastructure by creating audit reports.
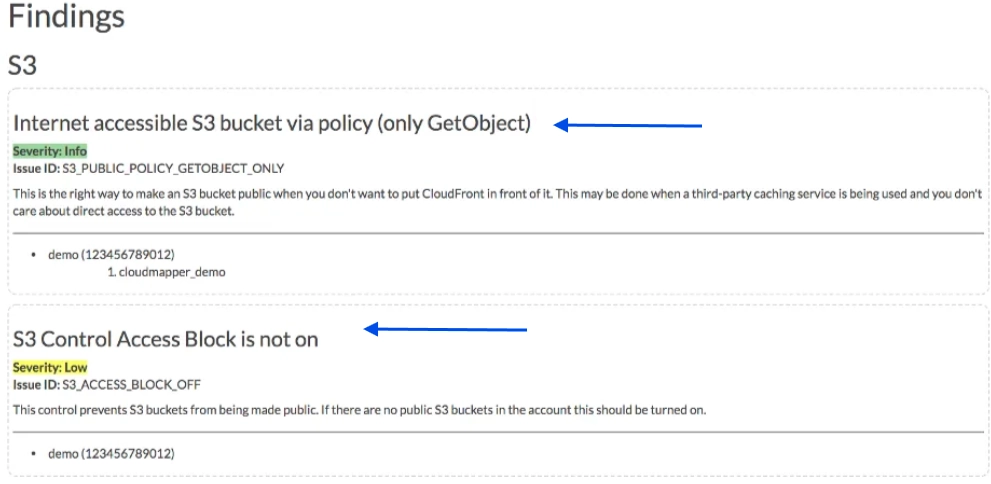
Source: Medium4
Findomain
Findomain provides a subdomain monitoring service for port scanning and vulnerability scanning. Monthly plans start at $150 for 150 targets to monitor.5
Findomain:
- Monitors your target domains with various common tools (such as OWASP Amass, Sublist3r, Assetfinder, and Subfinder)
- Receive notifications via Discord, Slack, Telegram, Email, or push notifications (Android/iOS/Smart Watch/Desktop) when new subdomains are discovered.
- Uses Certificate Transparency logs (an Internet security standard for attack surface monitoring and auditing) and different APIs to identify subdomains associated with a specific domain across numerous platforms, including Linux, Windows, macOS, and Android.
Installation: They provide ready-to-use binaries for the following systems (all are 64-bit only):
- Linux
- Windows
- MacOS
- Aarch64 (Raspberry Pi)
- NixOS
Findomain is beneficial in numerous aspects of attack surface management, including:
- Subdomain discovery: Findomain helps security experts locate subdomains connected with the target domain. Thus, discovering these subdomains gives them a better grasp of the organization’s attack surface and possible vulnerabilities.
- Asset inventory: Findomain generates an asset inventory and continually scans internet-facing assets for vulnerabilities, giving enterprises access to their external ecosystem.
- Automation: Findomain can send data to webhooks (an HTTP request) for automation.
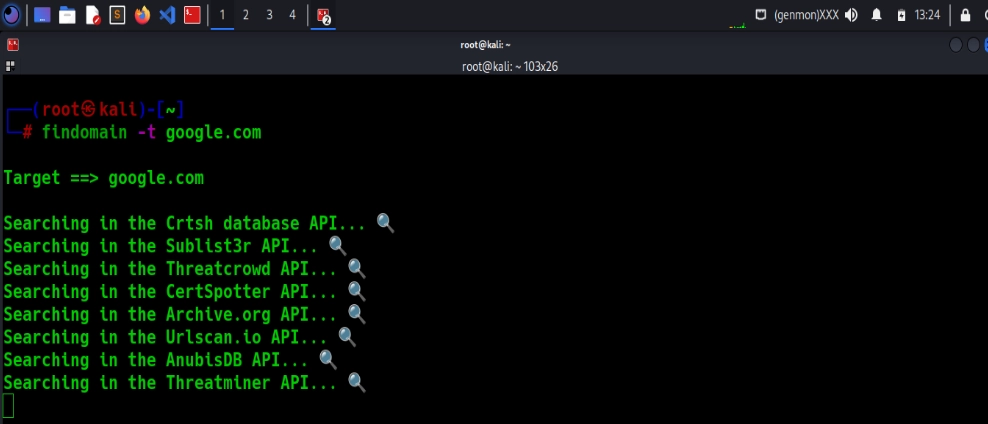
Source: BlackHat6
What is attack surface management?
Attack surface management (ASM) identifies, monitors, and controls all internal and external internet-connected assets for possible attack vectors and vulnerabilities. ASM aims to enhance visibility while lowering risk.
What is an attack surface?
The attack surface is the potential entry point for an attacker to access a company’s systems and data. This includes the following.
- Applications: Web applications, mobile apps, and APIs.
- Websites: Public, internal, and e-commerce sites.
- Networks: Internet, private networks, and cloud networks.
- Devices: Notebooks, phones, servers, and Internet of Things devices.
- Cloud infrastructure: Public, private, and hybrid clouds.
Key threat actors
- Hackers and cybercriminals: Malicious individuals or groups exploit vulnerabilities for personal gain, engaging in activities like identity theft or malware distribution.
- Nation-state actors: State-sponsored entities engage in cyber-espionage or cyber-attacks to achieve political or military goals, often associated with countries like China, Russia, North Korea, and Iran.
- Insiders: Employees, contractors, or partners with internal knowledge misuse their access for personal motives or to harm the organization.
- Hacktivists: Individuals or groups driven by social or political motives who hack into systems to promote a cause or protest against organizations.
What to look for when selecting an open source ASM software
Here are a few things to consider while choosing an open source ASM technology.
- Check the tool’s popularity: The amount of GitHub contributors and community members who respond to user questions indicates the popularity of open-source technology. The greater the community, the more support your organization will receive.
- Review the tool’s features: Open source ASM solutions include asset discovery or monitoring. However, if your business intends to utilize the ASM tool for a variety of applications, you should search for a more comprehensive solution. For example, a company seeking network mapping may select a system that includes detailed topology visualization capabilities.
- Evaluate closed source solutions: Open source solutions often have restricted or add-on functionality; however, deploying a more personalized solution that provides a greater degree of features (for example, vulnerability management) may be more efficient for your company.
Here’s a list of closed source ASM software.
Key benefits of open source attack surface management (ASM) software
1. Cost-effectiveness
- Free to use: Most open source ASM tools are free (with an option to upgrade paid versions for more comprehensive features), which is particularly beneficial for startups, small businesses, or organizations with limited budgets.
- No licensing costs: Unlike proprietary software, open source tools eliminate recurring subscription or licensing fees.
2. Transparency
- Full code access: Open source code offers transparent source codes on websites like GitHub, users can inspect the source code to ensure the software does exactly what it claims.
- Auditability: Open source ASM software enables users to audit codebase, components, license conflicts, and security vulnerabilities.
3. No vendor lock-in
- Freedom to switch: Since the software is open source, organizations are not tied to a specific vendor. If they choose to stop using a tool, they can simply move to another solution or integrate multiple tools.
4. Scalability
- Adaptable to cloud and on-premise environments: Many tools support cloud, hybrid, or multi-cloud environments. For example, OpenVAS may be executed on a single server or in a distributed multi-cloud system.
Further reading
- Top 10 Microsegmentation Tools
- Intrusion Prevention: How does it work? & 3 Methods
- Cybersecurity Risk Management
External Links
- 1. Masscan: A Fast IP Port Scanner for Windows, Linux and MacOS. SecurityTrails
- 2. Masscan: A Fast IP Port Scanner for Windows, Linux and MacOS. SecurityTrails
- 3. How To Use Nmap To Scan For Open Ports | Blumira. Blumira, Inc.
- 4. CloudMapper — Visualizing and auditing AWS infrastructures for free | Medium. Medium
- 5. Advanced, automated and modern vulnerabilities discovery platform.
- 6. Recon Tool: Findomain | Black Hat Ethical Hacking.


Comments
Your email address will not be published. All fields are required.