The increasing prevalence of misinformation, deepfakes, and unauthorized modifications has made content verification important. In the United Kingdom, 75% of adults believe that digitally altered content contributes to the spread of misinformation, underscoring the need for reliable verification methods.1
Content authenticity addresses this challenge by employing secure metadata and digital signatures to attach provenance data, which records who created the content, how it was modified, and whether AI tools were involved in its production.
Learn the top tools and technological foundations to achieve content authenticity.
What is content authenticity?
Content authenticity is the ability to verify the origin, integrity, and history of digital content such as images, videos, audio, and documents. It ensures that a piece of digital content is genuine, unaltered, and traceable to a trustworthy source.
This verification process relies on technologies such as secure metadata, digital signatures, and open standards like the Coalition for Content Provenance and Authenticity (C2PA).
When content authenticity is applied correctly, every content carries a verifiable record, sometimes called content credentials, that functions like a nutrition label for digital work.
These credentials include details such as who created the content, when and where it was designed, what device or software was used, and whether it has been edited or generated by AI. This record allows users to view content credentials and make informed decisions about what they see online.
Why content authenticity is essential
Combating misinformation and manipulation:
Since generative AI can create realistic but fabricated media, it has become difficult to distinguish real information from fake. False images, videos, and audio clips can spread rapidly on social media, misleading audiences and damaging trust.
Content authenticity helps counter this problem by attaching verifiable information to each file, showing how it was created and whether it has been altered.
Protecting creators and creative integrity:
For creators who share images, videos, or designs online, content authenticity ensures proper attribution. By applying content credentials, creators can connect their verified identity, social media accounts, and creative process directly to their work.
Content authenticity tools help protect originality and authorship while maintaining transparency about any edits or AI-generated elements.
Establishing trust in journalism and media:
Journalists and media organizations depend on authentic visuals and documents to inform the public accurately. Content authenticity allows editors and consumers to verify the source, time, and history of photos or videos before they are published or shared online.
It is particularly valuable in breaking news or crisis reporting where misinformation spreads quickly.
Maintaining transparency in AI-generated content:
As generative AI models become more common, labeling and identifying AI-generated content are crucial. Content credentials can include a clear indication that a file was created or modified using AI tools.
This level of transparency allows consumers to recognize AI involvement without assuming the content is deceptive.
Enhancing accountability for organizations:
Companies can use content authenticity to maintain brand trust and protect intellectual property. By embedding secure metadata and provenance information, they can demonstrate that their visual assets, marketing materials, and public communications are genuine.
It also helps them address misuse or impersonation attempts online.
Supporting digital literacy and informed decision-making:
When users can inspect a file through content authenticity tools, they gain insight into the content’s provenance.
This encourages critical evaluation of media and helps build an informed digital audience capable of identifying reliable information.
The ecosystem of content authenticity
Coalition for Content Provenance and Authenticity (C2PA)
The C2PA is a joint project established under the Linux Foundation’s Joint Development Foundation. It unites the Adobe-led Content Authenticity Initiative, Microsoft, and the BBC’s Project Origin. Its main goal is to create and promote an open standard for content provenance, allowing anyone to verify the origin and edit history of digital content.
Objectives
- Identify and document requirements for content provenance.
- Develop open technical specifications for embedding authenticity data into media files.
- Promote global adoption of these standards by publishers, media platforms, and device manufacturers.
- Ensure that provenance data remains accessible while respecting privacy.
- Encourage social media platforms to support content credentials to make authenticity verification available to users.
Key concepts
- Content credentials act like a nutrition label for digital content. They store verifiable metadata that records who created the file, when it was created, and what tools were used.
- The C2PA specification defines how this data is cryptographically signed and embedded, ensuring tamper-evident provenance.
- The manifest structure records assertions made by the creator or the app about the content’s origin and editing actions.
- A trust list governs valid certificates used in signing processes, ensuring interoperability and security.
Conformance and governance
The C2PA Conformance Program verifies that software, hardware, and services adhere to the content credentials specification. Certified implementations are added to a public trust list. This helps ensure that when creators apply content credentials, the metadata remains consistent and secure across apps and devices.
The transition from the Interim Trust List (ITL) to the official C2PA Trust List represents a move toward a more transparent and accountable ecosystem. Certificates are managed under clear policies, with time-stamping authorities providing additional verification layers.
Content Authenticity Initiative (CAI)
The Content Authenticity Initiative is a global community founded by Adobe in 2019. It includes media organizations, technology companies, and civil society groups. The initiative develops open source tools to implement C2PA standards and make content transparency an industry standard.
How it works
The CAI provides a secure end-to-end framework for recording and verifying the provenance of digital content. It integrates open source tools that help capture, sign, and display metadata during all stages of the content lifecycle: from creation to publishing.
- Creation: Tools record and store details about the file, such as the creator’s name, device, time, and editing history.
- Editing: When content is modified, the changes are recorded in the manifest, maintaining a continuous provenance chain.
- Publishing: The content credentials remain attached when files are shared online, allowing anyone to view content credentials using an inspect tool or browser extension.
Examples of implementation
- Leica M11-P camera: The first camera with built-in Content Credentials.
- Nikon Z6III: Embeds credentials for authenticity in photojournalism.
- The ProofMode app: Allows users to record verifiable photos and videos on mobile devices using digital signatures and secure metadata.
- Qualcomm Snapdragon 8 Gen3: Supports content credentials at the chip level for smartphones.
Core values
- Transparency: All provenance data is open and inspectable.
- Privacy: Users can choose which information to include and redact sensitive details if needed.
- Accessibility: Tools are open source and available to developers and creators.
- Education: The initiative promotes media literacy to help consumers interpret provenance data.
Adobe Content Authenticity
Adobe Content Authenticity extends these standards into practical tools that creators can use in Adobe apps such as Photoshop, Lightroom, and Firefly. It allows users to apply content credentials to their digital work, ensuring attribution and protecting against unauthorized use.
Features and process
- Users can apply content credentials to multiple files and download them back with durable metadata.
- Credentials can include the creator’s verified name, social media accounts, and usage preferences such as requests not to allow generative AI models to train on their content.
- When users share their work online, the credentials remain accessible through an interactive pin or icon on supporting websites.
- Invisible watermarking and digital fingerprinting make credentials recoverable, even if removed or screenshotted.
Durability and verification
Content credentials are stored both in the file and in Adobe’s public Content Credentials cloud. This ensures that even if a platform strips metadata, the credentials can be retrieved through Adobe’s Inspect Tool or the Content Authenticity Extension for Google Chrome.
The credentials are verified by the app or device that recorded them, and they are cryptographically signed to ensure authenticity. This allows consumers to view content credentials, understand a file’s origin, and edit history.
Clarifications
- Content credentials are not a copyright or digital rights management system. They do not control permissions or ownership but serve as a transparency mechanism.
- Adobe does not claim ownership over content authenticated using its tools.
- Applying credentials is currently free, promoting widespread adoption among creators.
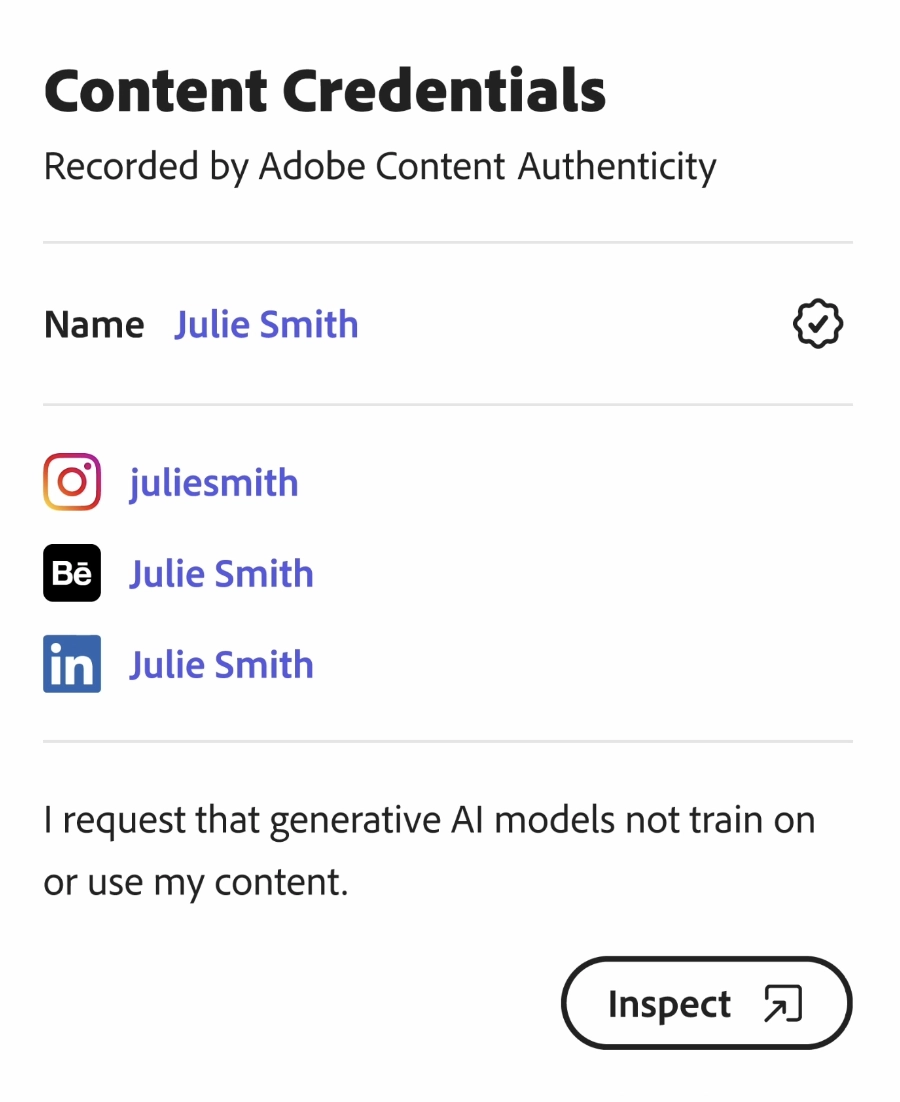
Figure 1: An example from Content Credentials, which are persistent metadata added to digital content that include information about the creator and how the work was produced.2
Technological foundations
Metadata and digital signatures
C2PA standards use secure metadata and digital signatures to protect the integrity of provenance information. Each file carries a manifest that links assertions about creation and editing to a cryptographic hash of the content. Any alteration invalidates the signature, signaling tampering.
Figure 2: An example of metadata showing the details of an image including its origin and discovery date, condition and location.3
In-sensor cryptography
In-sensor cryptography is a security approach that embeds cryptographic functions directly within sensor hardware. Instead of encrypting or authenticating data after it is captured, the process happens inside the sensor itself at the point of capture. This allows the sensor to generate encryption keys, secure the data it records, and bind those keys to the captured signal or image.
By integrating cryptography into the sensing stage, the data is protected before it leaves the device, significantly reducing the risk of interception or tampering.
Key characteristics
Traditional systems separate the sensor, which captures data, from the cryptographic unit, which secures it. This separation leaves data exposed during transmission or storage. In-sensor cryptography merges these two functions, ensuring that encryption and authentication occur immediately within the device.
The cryptographic binding is made in situ, meaning that the generated key is tied to the unique properties of the captured image or signal. This direct association improves the ability to detect unauthorized changes and enhances overall data integrity.
Examples and research developments
Researchers demonstrated in-sensor cryptography within neuromorphic vision sensors using AOC memristors, which can store, encrypt, decrypt, and even erase images internally without external processing.4
Another project employed a molybdenum disulfide phototransistor array to generate physically unclonable cryptographic keys that were bound to captured images.5
These developments highlight how optical and semiconductor innovations can enable encryption and authentication directly in hardware.
Benefits
- Immediate protection: Data is encrypted at capture, minimizing opportunities for interception.
- Enhanced binding: Encryption keys are linked to the original signal, making tampering easier to detect.
- Efficiency: Reduces reliance on external processors, which is valuable for lightweight or edge devices.
Challenges
- Complexity: Integrating cryptography into hardware increases design difficulty.
- Limited resources: Sensors operate with constrained energy and processing capacity, restricting cryptographic options.
- Lack of standardization: The field is still emerging, and global standards for interoperability are under development.
In-sensor cryptography is closely related to content authenticity, but it functions at an earlier stage in the content lifecycle. Both aim to ensure the trust, provenance, and integrity of digital content.
In-sensor cryptography secures the data the moment it is created, while frameworks of secure metadata and digital signatures are applied after capture to document provenance and editing history. When used together, these technologies create a chain of authenticity.
For example, a camera that employs in-sensor cryptography can encrypt image data at capture, producing a hardware-level signature that verifies the origin of the file. When the same image is processed in Adobe apps that support content credentials, this signature can be integrated into the C2PA manifest.
The result is both hardware-level assurance and software-level transparency, enabling users to view content credentials and confirm that the content has been captured and handled authentically.
AI detection and compatibility
Content authenticity systems complement AI detectors that identify synthetic or manipulated media. Content credentials can indicate whether a file was created by generative AI models, providing transparency without labeling such content as inherently harmful.
Digital watermarking and fingerprinting
Watermarking techniques embed identifiers directly into images, video, or audio files. These identifiers persist even if the file is resized or compressed. Fingerprinting allows the system to match altered versions of content with their original credentials.
Blockchain and distributed storage
Some CAI members use blockchain to maintain immutable provenance records. For example, Numbers Protocol and Starling Lab store content credentials on decentralized ledgers, enhancing transparency and auditability.
Applications of content authenticity
Journalism and media
Authenticity verification strengthens trust in news reporting. Major publishers such as Reuters, BBC, and AFP use C2PA and CAI tools to verify photo and video provenance. These standards help audiences distinguish between factual reporting and manipulated imagery.
Creative industries and brands
For artists, designers, and brands, content authenticity provides a verifiable link between their identity and their work. By using content authenticity apps and open standard frameworks, creators can ensure that their attribution data is preserved when their content is shared online.
Digital asset management
Organizations integrating content credentials into their digital asset management systems can track provenance across the content lifecycle. This improves archiving accuracy and helps distinguish between originals and derivatives. Tools that support content credentials will enable users to inspect authenticity automatically upon ingestion.
Human rights and legal documentation
Human rights organizations use provenance tools to record verified video and image evidence. This information can be used in investigations or court proceedings while maintaining the privacy of contributors.
Challenges in implementation
- Metadata stripping: Many social platforms remove metadata during uploads, which can erase provenance data unless the platform supports content credentials.
- Adoption gap: Not all software and websites currently support the open standard, limiting the reach of authenticity verification.
- Scalability: Processing and verifying content credentials at a global scale requires coordinated technical infrastructure.
- Intent and interpretation: Content credentials provide data, but users still need to interpret context and decide whether to trust the source.
- Privacy balance: Systems must protect sensitive information while maintaining traceability.
Future of content authenticity
As digital content continues to evolve, the role of content authenticity will expand.
- Global standardization: The C2PA open standard is positioned to become the foundation for digital provenance across industries.
- Integration with generative AI: Future tools will include automatic provenance tagging for AI-generated outputs, aligning with new generative AI training disclosure requirements.
- User empowerment: Consumers will increasingly rely on provenance data to evaluate online information.
- Platform responsibility: Websites and social networks are expected to adopt mechanisms to support content credentials, promoting consistent transparency.
- Educational efforts: Expanding awareness of authenticity indicators will help users interpret provenance data accurately.

Be the first to comment
Your email address will not be published. All fields are required.