We spent three days testing and reviewing popular Privileged Access Management (PAM) solutions. We used the free trials and admin consoles of BeyondTrust, Keeper PAM, and ManageEngine PAM360. For solutions that required registration, we relied on official product documentation and user experiences to assess their capabilities.
When selecting the best PAM solutions, we considered common buyer needs, such as DevOps & infrastructure integrations, access & automation capabilities.
Best 8 commercial PAM vendors
Vendor | Best for | Starting price | Contract term |
|---|---|---|---|
Enterprise-level integration | $98,690 | 36 months | |
Enterprise-level integration | $44,712 | 12 months | |
Small to medium businesses looking for a cost-effective PAM | $7,995 / year + maintenance | Annual license | |
DevOps and cloud-native teams needing fast, dynamic access | $840–1,200 / user per year | 12 months | |
Managing remote access | No public information | 12 months | |
Cloud-first organizations using Okta for identity | Small orgs: $2–15 / user / month Large orgs: $72,000 / year (+ $8,000 for MFA/API, $2,000 for PAM add-on) | – | |
SMBs and distributed teams needing a simple cloud PAM | $490 / year (~$2–85 / user / month) | Annual | |
Enterprises focused on identity governance | $825,000 | 36 months |
Pricing insights come from AWS Marketplace and official vendor websites.1
Recommendations to buyers
PAM solutions’ pricing scales per user, per managed asset, or through subscription bundles that combine credential vaulting, session monitoring, and automation capabilities, etc.
Users report that license costs and operational overhead are the main barriers to adoption. For example, CyberArk and BeyondTrust are high-priced platforms, with annual per-user costs exceeding those of Microsoft M365 E5 licenses. 2
Mid-tier vendors such as ManageEngine, Keeper, and StrongDM offer more accessible pricing models like subscription-based or admin-based licensing rather than full user-based metrics, lowering entry costs for smaller environments.
Buyers should also factor in ongoing maintenance and administrative overhead, not just licensing. PAM systems require constant policy tuning, account onboarding, and integration management. While basic password vaulting and rotation can be implemented quickly, achieving full value through Just-in-Time access or continuous session auditing demands long-term operational commitment and internal process maturity.
PAM maturity comparison
All reviewed PAM solutions include a common set of core features, explained below. Where they begin to diverge is in the depth of automation, context-aware access control, and full-stack integration capabilities that enable:
- Just-in-Time (JIT) access, which grants temporary, time-bound privileged access only when needed and automatically revokes it afterward.
- Dynamic access, which expands JIT principles with adaptive, context-driven access across users, machines, APIs, and applications.
DevOps and infrastructure integrations
* Supports secrets management usable with Kubernetes (no explicit full orchestration support.
Environments span on-premises, hybrid, and multi-cloud infrastructures, with privileged access extending to endpoints, servers, SaaS platforms, and containers. A strong PAM solution should discover all privileged identities, not just administrative accounts. This includes managing service accounts, API keys, and machine identities that are integral to CI/CD, containers, APIs, Kubernetes, and Terraform for automation and integration.
Compliance and reporting capabilities
The vendors we selected offer out-of-the-box reports and mappings to major regulatory frameworks. Regulations such as PCI DSS, ISO 27001, and HIPAA all require strict controls over privileged access to ensure accountability and data protection.
Most leading PAM platforms, including BeyondTrust, CyberArk, Delinea Secret Server, ManageEngine PAM360, Okta, and Keeper Security, provide built-in reporting templates and policy mappings aligned with these frameworks. For example, you can review WALLIX’s compliance-reporting capability here.5
For some vendors, such as StrongDM, WALLIX, and SailPoint, we could not find detailed public information confirming predefined compliance reports.
Real-world PAM implementation considerations
Can PAM manage heterogeneous systems (e.g., firewalls, switches, routers, Linux servers, off-domain servers, SQL databases)?
Yes, most PAM systems can manage a wide variety of systems, including firewalls, routers, switches, Linux servers, off-domain servers, SQL databases, and other critical infrastructure. However, the depth of integration can vary:
- Out-of-the-box connectors exist for common enterprise systems (Windows, Linux, AD, network devices, databases), but custom integrations are often needed for niche or legacy systems.
- Some PAM platforms, like CyberArk and BeyondTrust, provide marketplaces with predefined integrations or API connectors to extend their reach to more specialized systems.
- If a direct connector isn’t available, API-based integrations can be built, allowing PAM systems to manage and rotate credentials for a variety of devices that expose command-line or REST API access.
How well do PAM systems integrate with APIs and services? Can a PAM system replace the use of secrets and certificates in scheduled tasks or scripts?
PAM systems can integrate with APIs and services to manage secrets, certificates, and credentials for scheduled tasks or scripts. Most enterprise-grade PAMs (e.g., CyberArk, Delinea, ManageEngine) support integrations with DevOps tools like Ansible, Jenkins, and Terraform, along with API calls to automate credential retrieval for applications, scripts, or services.
- Credential retrieval from a vault: For scheduled tasks, scripts, and automation pipelines, listed PAM systems provide REST APIs and secrets management tools to dynamically retrieve passwords or certificates.
- Replacing secrets in scripts: PAM systems can replace hardcoded credentials in scripts or applications by storing secrets in the vault and referencing them programmatically when required.
However, PAM systems often require significant setup and testing to fully replace manual secrets management in scripts or scheduled tasks. Expect some integration work to get everything functioning smoothly.
Do you strip all admin access from in-scope systems once PAM is onboarded?
This varies by organization and the specific PAM deployment strategy. While the goal of any PAM implementation is to remove standing administrative access (to reduce the risk of unauthorized access), many systems still maintain break-glass accounts for emergency access in case of PAM failure or critical incidents.
- Emergency access accounts: These are emergency accounts that provide direct access to systems if PAM becomes unavailable. Typically, these accounts should be managed and stored securely (e.g., using smart cards or hardware security modules).
- JIT PAM approaches: Some PAM tools offer Just-in-Time (JIT) access, which means privileges are provisioned only when necessary and revoked once the task is complete, reducing the need for persistent administrative access.
- Recommendations: It’s not recommended to strip all access immediately, as failover mechanisms (like break-glass accounts) should be tested and ready for use if needed.
Free PAM solutions
A few vendors provide free solutions with PAM capabilities, which are a good fit for small-scale deployments. Some, such as Devolutions Password Hub, also offer paid business plans that include enterprise features, such as approval workflows and compliance reporting.
We reviewed these tools based on their level of PAM functionality. Below, we provide some of the key solutions. For more details, see our article on free PAM Solutions.
PAM for secure credential storage (vault-based tools):
- Thycotic Secret Server – Free Edition (now Delinea): For using basic credential vaulting and RDP/SSH session launching, without full PAM features.
- Devolutions Password Hub Free: For leveraging a cloud vault with access tracking, but no session control.
- KeePassXC (with KeeAgent): For managing local-only passwords and SSH keys.
PAM for dynamic secrets management tools:
- Vault by HashiCorp (Community Edition): For DevOps teams managing machine-to-machine secrets, dynamic credentials, and automation workflows.
BeyondTrust
We used the admin console of BeyondTrust to test how access approvals and session requests work in practice. Below, we will highlight our experience:
System & interface overview:
List of privileged accounts this user has permission to access
You can initiate a session to these target systems using your existing tools with Direct Connect or right from the Password Safe Web Console.
- Users can launch sessions directly from the vault, with credentials automatically injected.
- It supports cross-platform access (Windows via RDP, Linux via SSH) from a unified interface.
- These sessions can be recorded, monitored, and terminated according to policy.
Based on our experience, two use cases stood out for BeyondTrust: remote access and credential storage & management.
Remote access (privileged remote access):
BeyondTrust’s privileged remote access is built for giving admins and vendors controlled access to restricted parts of your network. Think of it as a secure remote jumpbox where you can grant access on demand or require approval first, convenient for external contractors. It also includes session recording and playback tools for audit and compliance.
Requesting access to the WS20 system:
In this view, we are requesting access to the WS20 system. The console allows setting the start date, access window, and duration, as well as choosing between retrieving a password or launching an RDP session directly. This flexibility is part of BeyondTrust’s granular access control, where you can define who gets access, when, and for how long.
In this case, the system required manual approval before initiating the RDP session. Earlier sessions on other systems were auto-approved because the user was marked as trusted.
This demonstrates BeyondTrust’s ability to enforce dynamic access policies based on system type, trust level, or risk conditions.
You can also link access requests to a ticketing system (like ServiceNow) and specify a ticket number for tracking. The console provides the ability to set just-in-time (JIT) access durations, for example, two hours, ensuring privileged credentials aren’t left active longer than necessary. Once approved, the session can be launched immediately, along with all related actions.
For more, you can see JIT auditing documentation.
Overall, the admin console provides clear visibility and strong policy enforcement, though initial configuration can be complex. Once set up, however, the workflow offers a controlled and auditable process for managing privileged sessions and credential retrieval.
Credential storage & management (Password Safe):
BeyondTrust’s Password Safe handles credentials such as service accounts, local application logins, and admin passwords. The Team Passwords option helps when you need to share credentials without full automation.
This is a more automation-heavy approach compared to other vendors’ approaches (ManageEngine or Delinea), which provide smoother manual onboarding experiences.
Team members can create a folder structure to manage team passwords
Integration and onboarding:
You can integrate BeyondTrust with ticketing and ITSM systems like ServiceNow, but most teams start off doing things manually before automating approvals. The integration is powerful but takes effort to get right. BeyondTrust relies on vendor assistance for setup and expansion.
Automation and password rotation challenges:
BeyondTrust’s password automation is powerful but requires caution early on. Services can get locked out if cached credentials aren’t updated before rotation. Start by onboarding built-in admin accounts and rolling out automation slowly. Also, if your Active Directory has special password age or complexity rules, make sure BeyondTrust’s policies match to avoid rotation failures.
CyberArk, Delinea, and ManageEngine face similar challenges.
Strengths
- Granular access control: Detailed approval workflows for internal admins and third parties.
- Strong session auditing: Reliable session recording, monitoring, and playback.
- Strong ITSM Integration: Deep integration with ServiceNow and other ticketing systems enables access requests to be made directly from incident or change tickets.
- OneClick access: Streamlines password checkouts and session launches without repeating full approval workflows.
- Multi-system checkout & scripted jumps: Allows simultaneous session launches and post-login commands across linked systems.
- Developer integration: REST API and GitHub Action support extend PAM capabilities into DevOps pipelines.
Weaknesses
- Performance overhead: Session startup and authentication can feel sluggish, adding several minutes to tasks.
- Short timeout settings: Frequent reauthentication interrupts workflows.
- Manual onboarding friction: Automation-first design makes manual setup more cumbersome.
- Vendor dependency: Configuration and scaling often need direct vendor support.
- Inconsistent OS performance: Windows deployment runs smoother than Linux in many cases.
CyberArk
CyberArk is a Palo Alto acquired company.6 It is an enterprise password management system. Any systems using secrets used by configuration management, such as Ansible, should probably have the secrets stored in that system. You can likely use Ansible modules to interact with CyberArk.
CyberArk provides an enterprise PAM system. It’s for large enterprises with a hybrid environment, technical staffing, and compliance requirements to fully manage it. For smaller or less-regulated teams, it is overly complex compared to lighter PAM or secrets management tools.
Below, we will walk through its strengths/weaknesses based on admin experience shared at Reddit. Also, here is a full CyberArk administrative tutorial.
Control plane for identities across sources:
Many IAM tools that require you to replicate or sync users between systems, CyberArk’s Adaptive Directory functions as a meta-directory. It integrates Active Directory, LDAP, and cloud users into a single management view, without copying external users into the cloud.
You can see and manage all users (from AD, LDAP, federated IdPs, or the native CyberArk directory) in one place:
The admin portal is where you will manage your Identity Service as well as complete any desired customization for identity management.
Credential management & rotation:
CyberArk’s Privileged Account Security (PAS) suite revolves around the Enterprise Password Vault (EPV), which stores and rotates credentials across servers, databases, and network devices. Passwords and SSH keys can be rotated automatically based on policy or usage.
Admins can enforce checkout periods, approval workflows, and automatic reconciliation if credentials fall out of sync. For Linux environments, CyberArk can rotate passwords and integrate with AD accounts through LDAP synchronization, reducing static credential exposure. This functionality is particularly valuable in large estates (500+ servers), where manual password hygiene becomes unmanageable.
Session management & auditing:
CyberArk lets you connect to servers directly from the vault without ever seeing or typing the password. All activity during those sessions can be recorded and logged for auditing and compliance.
However, connecting to systems through CyberArk is slower than using standard SSH or RDP tools, especially in Linux environments. Some admins also mention that they can only open one session at a time, which can slow down daily operations. 7
Deep, policy-based security and granularity:
Policies can target roles, devices, applications, endpoints, and even authentication flows. Each policy is modular to control one aspect (like app access, user self-service, or endpoint restrictions). The policy hierarchy lets you manage conflicting or overlapping rules predictably (top-down precedence).
Integration with DevOps & automation
CyberArk provides APIs and SDKs for integration with configuration management and CI/CD tools such as Ansible, Terraform, and Jenkins. However,:
- Some teams have successfully pulled credentials into Ansible using CyberArk modules.
- Others report poor vendor support or difficulty testing integrations, especially in automated pipelines:
Implementation & administration experience:
Deploying CyberArk isn’t plug-and-play. Full implementation can take months and requires dedicated expertise. Misconfiguration is a recurring theme in user feedback; many installations leave key features disabled simply because teams can’t test or validate them.
When built properly, though, CyberArk provides strong control, auditing, and scalability.8
Strengths
- Comprehensive PAM platform: Full lifecycle coverage: credential vaulting, rotation, session control, and audit.
- Robust security controls: Credentials never reach endpoints; supports granular access and multi-step approvals.
- Enterprise audit trail: Session recording, keystroke logging, and searchable transcripts meet strict compliance standards.
- Strong AD integration: Synchronizes with Active Directory and automates password reconciliation.
- Scalability: Built for large, complex, multi-domain environments.
- Integration Ecosystem: APIs, SDKs, and modules for CI/CD, ITSM, and SIEM systems.
Weaknesses
- Complex deployment: Requires specialized expertise; typical rollout can take months.
- Performance Lag: Session initiation (especially SSH) can take 15–30 seconds or longer.
- Limited Linux experience: PSM client and session control are less smooth than in Windows.
- Vendor support variability: Support responsiveness and integration guidance can be inconsistent.
- Overkill for small teams: Smaller organizations may find the platform too heavy and costly for their scale.
ManageEngine PAM360
ManageEngine PAM360 is a cost-effective privileged access management (PAM) solution for small to mid-sized organizations that need core PAM features without the steep costs of tools like CyberArk or BeyondTrust. The product is licensed based on the number of administrators rather than the number of assets.
It offers PAM features including password vaulting, session monitoring, and access control, but its interface and integration quality can be less refined compared to more expensive solutions.
Also, in comparison to many of the top privileged access management vendors, ManageEngine only offers PAM360 as on-premises software. ManageEngine PAM3602 does not support cloud-native environments, data container systems like Kubernetes, or Linux.
Basic features included:
- Password vaulting & rotation: Secures passwords and integrates with Active Directory and LDAP for credential management.
- Session monitoring & recording: Monitors user activity with session shadowing and session recording.
- Approval workflows: Use ticketing and approval systems to control access to privileged accounts.
- Automated compliance reporting: Provides pre-built reports to assist with regulatory compliance (e.g., PCI DSS, HIPAA).
- Integration with ITSM/DevOps: Works with tools like ServiceNow, Ansible, and Jenkins for access automation.
Missing features compared to competitors like BeyondTrust:
- Session management: While PAM360 supports session recording, it lacks live session monitoring, session playback controls, and real-time threat detection offered by BeyondTrust.
- Comprehensive cloud support: BeyondTrust provides robust cloud-native PAM features, including Cloud Access Security Broker (CASB) functionalities, which PAM360 does not.
- Enterprise reporting/analytics: BeyondTrust offers more detailed, customizable compliance and activity reports with user behavior analytics.
Strengths
- Cost-effective PAM solution: Provides essential PAM features at a lower cost than high-end competitors.
- Comprehensive features: Includes credential vaulting, session recording, and approval workflows.
- Strong directory integration: Integrates well with Active Directory and LDAP for seamless account management.
- DevOps & ITSM support: Works with Ansible, Jenkins, and ServiceNow for integration into automation and incident management workflows.
- Licensing flexibility: Licenses are based on admins, not assets, making it cost-effective for smaller teams.
Weaknesses
- Clunky interface: The user interface is outdated and not as intuitive as competitors.
- API limitations: The API is poorly documented, making automation and integration challenging.
- Slow session playback: Session replay can be slow, especially during periods of heavy usage.
- Cloud version issues: The cloud-hosted version has performance problems and potential security concerns.
- Inconsistent support: Support quality can be slow, especially for technical issues or complex integrations.
StrongDM
Strong DM Architecture9
StrongDM is notably more intuitive and easier to onboard compared to CyberArk, with BeyondTrust falling somewhere in between.
Administrative tasks are straightforward, and vendor support typically meets service-level expectations. Communication around updates, new features, and security vulnerabilities is consistent and transparent.
However, scalability becomes more challenging in larger deployments, especially for organizations managing thousands of endpoints or complex multi-cloud environments where centralized policy enforcement and performance monitoring demand additional configuration and oversight.
Below are some highlighted technologies that StrongDM supports:
Source: StongDM10
Strengths
- Agentless, proxy-based architecture: Unlike CyberArk or BeyondTrust, StrongDM doesn’t require agents on target systems. Its proxy model connects users directly through existing tools (CLI, RDP, SSH) while maintaining full audit visibility.
- Developer & DevOps friendly: StrongDM is designed for automation-first teams, offering APIs, CLI tools, and SDKs for embedding access control into CI/CD pipelines without the complexity of legacy PAM deployments.
Weaknesses
- API dependence: Continuous connectivity to the StrongDM API is required for access to managed resources, which can introduce reliability concerns in restricted or offline environments.
- No native machine identity management: Lacks built-in capabilities for handling non-human or service accounts, limiting its automation scope for machine-to-machine authentication.
- Limited decretless architecture: Although it supports ephemeral access, StrongDM still aligns partly with traditional credential models, relying on stored passwords, SSH keys, and secrets vaults in certain cases.
- No native cloud console workflows: Does not yet support direct integration with cloud provider consoles (e.g., AWS, Azure, GCP) for access workflows; administrators are required to provision and rotate cloud access keys manually.
WALLIX
Best for organizations looking to secure privileged access across traditional IT and hybrid infrastructures.
While many PAM platforms emphasize DevOps and cloud-native integrations, WALLIX maintains a security-first, infrastructure-centric approach. Its focus is on privileged session management, credential vaulting, and visibility rather than full-stack automation or CI/CD orchestration.
WALLIX Bastion can be deployed on-premises or in the cloud (AWS, Azure, GCP), but lacks native support for container orchestration platforms like Kubernetes or modern secrets management pipelines.
Strengths
- Agentless deployment: WALLIX uses an agentless approach, reducing complexity during deployment and minimizing maintenance overhead compared to agent-based PAM systems.
- Strong session management: Provides session recording, live monitoring, and playback capabilities. Admins can supervise or terminate sessions in real time to ensure policy compliance.
- Compliance-ready auditing: Designed with compliance standards in mind, including GDPR, ISO 27001, and NIS2.
Weaknesses
- Limited cloud and container support: Lacks native integrations for Kubernetes, Docker, and major cloud platforms (AWS, Azure, GCP).
- Limited API and DevOps Integration: Compared to tools like CyberArk or StrongDM, WALLIX provides fewer automation and API capabilities.
- Smaller ecosystem support: WALLIX has fewer third-party integrations and a smaller partner ecosystem compared to major vendors such as BeyondTrust, CyberArk, or Okta.
Okta Privileged Access (ASA)
Okta ASA is best for cloud-native organizations that need secure, identity-driven SSH/RDP access across multi-cloud environments. The platform integrates directly with Okta’s identity and access management (IAM) ecosystem, enabling centralized control and visibility.
However, it lacks full PAM breadth (like credential vaulting, session playback, and database access), so enterprises seeking a complete privileged access platform will likely need to pair it with a traditional PAM tool such as BeyondTrust or CyberArk.
Strengths
- Cloud-Native Architecture: Best for multi-cloud and hybrid infrastructure, supporting AWS, Azure, GCP, and on-premises environments without requiring agents or complex network tunnels.
- Ephemeral credentials: Instead of storing static passwords or SSH keys, it issues short-lived, per-session credentials, reducing credential sprawl and minimizing attack surface.
- Deep Okta integration: Natively integrates with Okta Identity Cloud, inheriting its MFA, SSO, and policies.
Weaknesses
- Limited scope: It does not natively manage privileged access to databases, web applications, Kubernetes clusters, cloud consoles (like AWS Management Console or Azure Portal), or network devices.
- No central credential vault: Since it uses ephemeral certificates, it lacks a traditional password or secrets vault.
Keeper PAM (Keeper Security)
Keeper PAM is a cost-effective, easy-to-manage, cloud-based privileged access management solution for small to mid-sized teams that need secure credential storage, session control, and centralized user management without the overhead of complex deployment.
The solution builds on Keeper’s long-standing password manager platform, expanding it with role-based access controls (RBAC), auditing, and secrets management for IT and DevOps teams.
We tested Keeper PAM, focusing primarily on RDP session management. Below, see our experience with Keeper PAM:
Admin console overview:
When logging into the Admin Console, you’re greeted by a clean dashboard that gives a high-level overview of user activity, security posture, and system health.
The Dashboard provides oversight of the following:
- Top Events and link to Timeline Chart
- Security Audit Overall Score
- BreachWatch Overall Score
- User Status Summary
The Admin tab is where most configuration and user deployment tasks are handled. From here, administrators can manage Nodes, Users, Roles, Teams, and Two-Factor Authentication (2FA) settings, providing centralized control over access policies and organizational structure:
Role-based access controls:
Keeper PAM includes Role-Based Access Controls (RBAC) that allow administrators to define enforcement policies based on each user’s job responsibilities while delegating specific administrative permissions when needed.
These enforcement policies cover a wide range of configuration categories, including:
- Login Settings
- Two-Factor Authentication (2FA)
- Platform Restriction
- Vault Features
- Record Types
- Sharing & Uploading
- KeeperFill
- Account Settings
- Allow IP List
- Keeper Secrets Manager
- Transfer Account
Configuring enforcement policies for roles:
To configure enforcement policies, navigate to Admin, Roles, select a role, and click Enforcement Policies. A configuration dialog will appear, allowing specific rules to be applied. Once policies are defined, click Done to finalize and enforce them across all users assigned to that role.:
Deploying Keeper:
Business customers can add users through manual invitations, bulk imports, or provisioning methods, depending on organizational needs.
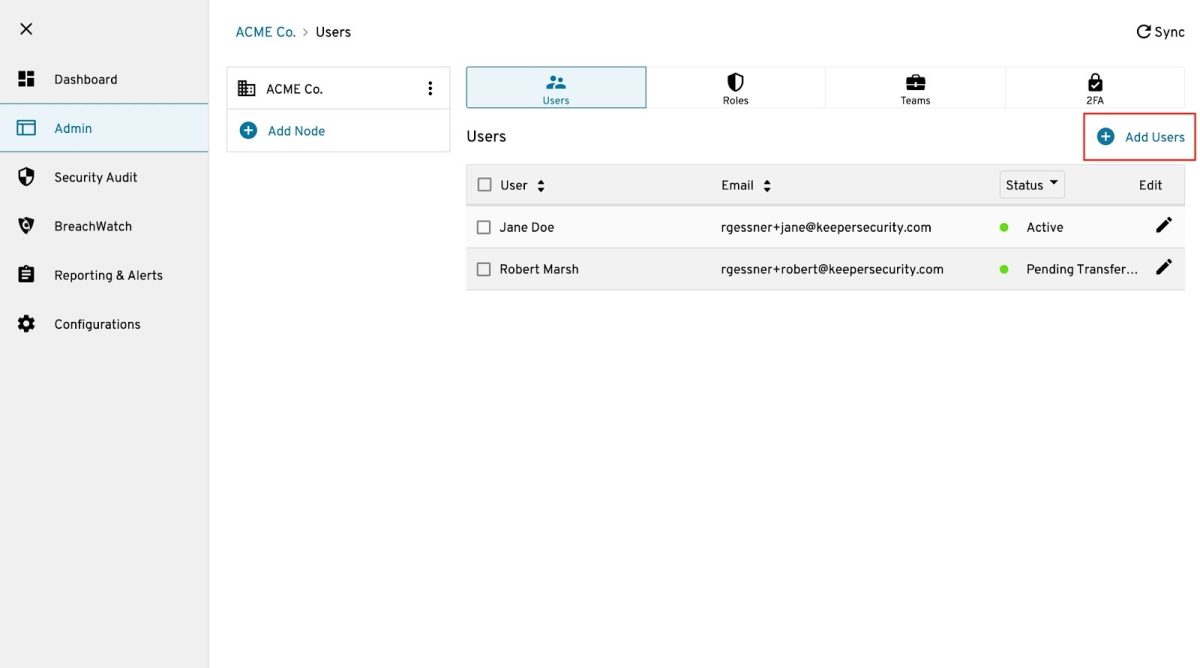
For manual user provisioning: You can invite users individually by navigating to add users, selecting the desired node, and entering the user’s full name and email address.
Also, for bulk user import: For larger deployments, admins can import users in bulk using a CSV file, automatically sending setup invitations to each user. Once users are added, Keeper automatically sends an email invitation prompting them to set up their account and complete onboarding.
Keeper Teams plan
For teams, it offers a Team module, which gives users the ability to share the records and folders within their vaults with logical groupings of individuals. To do that, you need to set Team Restrictions (edit/viewing/sharing of passwords) and add individual users to the team:
To create a team, select the node you want to associate it with, enter the team name, and click Add Team:
Once created, you can configure team-level restrictions, such as:
- Disabling record re-shares
- Preventing record edits
- Applying a privacy screen for sensitive data
It’s important to note that Keeper implements Least-Privileged policies, so when a user is a member of multiple roles or teams, their net policy is most restrictive or least privileged.
Keeper Enterprise
While our testing focused on Keeper for smaller teams, the Keeper Enterprise edition builds on these capabilities with additional compliance and multi-platform support.
It provides enterprise-grade risk analytics:
It provides Keeper is SOC 2 Certified, ISO27001 Certified, FedRAMP. See its security audit score dashboard:
Keeper Enterprise also provides multi-platform access, offering full functionality across Windows, Mac, Linux, iOS, Android, and all major web browsers (Chrome, Edge, Firefox, Safari). You can enforce platform restrictions, for example, limiting access to specific OS environments or disabling browser-based logins for high-security users.
Strengths
- Seamless deployment and updates: Keeper offers fully cloud-native deployment with automatic vault and client updates, reducing maintenance overhead for administrators.
- Agentless architecture: Requires no local agent installation.
- Extensive plugin and SDK support: Keeper provides plugins and APIs that enable integration with CI/CD tools, DevOps pipelines, and identity platforms.
Weaknesses
- Limited desktop stability: Certain features (e.g., RDP and tunnel connections) perform inconsistently on desktop apps compared to the web interface.
- Restricted coverage: Focuses primarily on credential management and secrets storage, lacks broader PAM capabilities like dynamic JIT access or full session proxying.
SailPoint (PAM Module)
SailPoint’s Privileged Account Management (PAM) Module extends its core Identity Governance and Administration (IGA) capabilities to cover privileged accounts.
Best for large enterprises already invested in SailPoint’s ecosystem that need centralized identity governance, compliance reporting, and access certifications tied directly to privileged access.
Strengths
- Comprehensive governance integration: Natively connects PAM data to identity governance, enabling full visibility of privileged accounts across systems.
- Access recertification: Automates access reviews and compliance reporting for privileged accounts.
Weaknesses
- Costly licensing: Expensive compared to dedicated PAM vendors, especially for organizations not already using SailPoint IdentityIQ.
- Limited PAM depth: Lacks deep session recording, credential vaulting, or just-in-time (JIT) access capabilities found in platforms like CyberArk.
Core capabilities of PAM vendors
All reviewed PAM solutions include core PAM features. These include:
- Identity-based access controls: Integration with enterprise directories such as Active Directory, LDAP, or SSO platforms to centralize user authentication and access enforcement.
- Multi-Factor Authentication (MFA) and Single Sign-On (SSO): Built-in or integrated support for MFA and SSO to strengthen authentication and simplify user access across systems.
- Privileged credential vaulting: Secure, encrypted storage for privileged account passwords, SSH keys, and API secrets.
- Session recording and monitoring: Full visibility into privileged activity, with the ability to record, audit, and replay administrative sessions for compliance and forensic review.
- Access request and approval workflows: Request-based access with approval mechanisms.
Summary
- For small to mid-sized orgs with a few admins: Choose per-admin or per-asset licensing models (e.g., ManageEngine PAM360, Keeper, StrongDM). These provide core PAM capabilities: credential vaulting, rotation, and access workflows.
- For large enterprises or regulated sectors: Consider vendors like CyberArk or BeyondTrust. While they cost more, these platforms deliver JIT access and deeper compliance auditing needed in industries with strict governance and reporting mandates.
- For cloud-native or DevOps-focused teams: Look at usage-based or subscription PAMs such as Okta ASA or StrongDM, which integrate seamlessly with CI/CD pipelines.
Reference Links
Cem's work has been cited by leading global publications including Business Insider, Forbes, Washington Post, global firms like Deloitte, HPE and NGOs like World Economic Forum and supranational organizations like European Commission. You can see more reputable companies and resources that referenced AIMultiple.
Throughout his career, Cem served as a tech consultant, tech buyer and tech entrepreneur. He advised enterprises on their technology decisions at McKinsey & Company and Altman Solon for more than a decade. He also published a McKinsey report on digitalization.
He led technology strategy and procurement of a telco while reporting to the CEO. He has also led commercial growth of deep tech company Hypatos that reached a 7 digit annual recurring revenue and a 9 digit valuation from 0 within 2 years. Cem's work in Hypatos was covered by leading technology publications like TechCrunch and Business Insider.
Cem regularly speaks at international technology conferences. He graduated from Bogazici University as a computer engineer and holds an MBA from Columbia Business School.

Be the first to comment
Your email address will not be published. All fields are required.