Browser Fingerprinting: Techniques, Use Cases & Best Practices

Online user data can be a great source for businesses to understand their target audience and improve their engagement with their potential and existing customers. Browser fingerprinting is one of the user identification methods used by websites for various purposes, such as web personalization, fraud detection, targeted advertising, etc. However, prior to leveraging the technology, we recommend getting an in-depth understanding of it since it has implications for user privacy.
For that purpose, we have curated this article to explain the concept of browser fingerprinting, how it works and how you can fight back against browser fingerprinting
What is browser fingerprinting?
Browser fingerprinting, also known as online fingerprinting, is a tracking technique initiated by websites to collect innocuous data from their visitors’ IP addresses.
What kind of information is gathered?
When you visit a website, your device sends a connection request to the target site to display the website’s content. The target site can access and collect information sent by your browser about your device. Websites can gather much information about a user’s device with browser fingerprinting technology to tailor recommendations to their visitors. A website, for example, may be able to collect the following information about you without your consent depending on your browser type:
- Web browser (Chrome, Mozilla, Firefox, etc.)
- HTTP header (information regarding your browser and operating system)
- Preferred language
- Timezone
- Screen resolution
- Plugins and extensions
If the website you visited uses fingerprinting technology, it will be able to detect and track your browser. When you return to the same website, it may remember your digital fingerprinting and identify you as a returning visitor. You can find out what is in your browser fingerprint and how unique your browser fingerprint is by visiting amiunique.org. As you can see, mine is unique within amiunique.org’s database (see Figure 1).
Figure 1: Example of a browser’s fingerprint
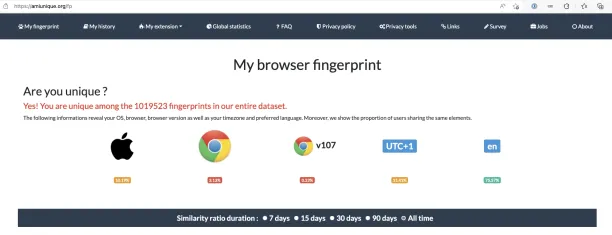
By scrolling down on amiunique.org, you can see how much data your browser shared about you (e.g. your OS, browser version etc.) without you providing any consent.
How does browser fingerprinting work?
With each connection request to a website, you make your device information available to the target website. Assume you use your mobile phone to visit an eCommerce website. Your browser sends a connection request to the target web server when you click on the link to visit the eCommerce website. Then, the web server will gain access to a small piece of data on your device, such as IP address, browser type, user agent, and much more. In this case, your user agent will inform the web server that you are making a connection request from your mobile phone using Safari. The website will display its content based on the user agent information provided.
The website tracks your behaviors and activities as you navigate the website’s pages to analyze your use of the website. Each time you visit the eCommerce website, your device will be identifiable based on your browser fingerprinting by the website.
What are the different fingerprinting methods?
1. Canvas Fingerprinting
Canvas fingerprinting is a type of browser fingerprinting used to track online users. Canvas fingerprinting forces users’ devices to draw a hidden image to extract a digital fingerprint without their knowledge (see Figure 2). This fingerprinting method mostly uses the HTML5 canvas element to reveal information about users’ machines, such as operating systems, browser types, and much more. When a user visits a webpage, the browser renders the image/text content on the page to display the content automatically.
Figure 2: Demonstrates the process of canvas fingerprinting
For example, if the website you visit uses canvas fingerprinting technology, the website will instruct your browser to draw an invisible image or text. In doing so, the HTML5 canvas element will reveal information about your machine, such as background color settings, font size/style, graphics card, and other distinctive features (see Figure 3). Since different devices render images differently, canvas fingerprinting will analyze how the device rendered the image/text to assign each user’s device a unique ID.
Figure 3: An example canvas font fingerprinting script
2. WebGL Fingerprinting
WebGL fingerprinting technique, like canvas fingerprinting, is used to expose information about devices’ graphics drivers and screen resolution by forcing browsers to render an image or text. This technique distinguishes users based on their graphics drivers and screen resolution, and creates unique fingerprinting.
3. Audio Fingerprinting
Audio fingerprinting tests how your device plays sound (see Figure 4). Audio fingerprinting works similarly with canvas and WebGL fingerprinting. Since each device produces a unique set of sound waves, audio fingerprinting can identify users based on the audio signals produced by their devices, such as sound hardware and software.
Figure 4: Workflow for browser fingerprinting
Top 3 use cases of browser fingerprinting
1. Online Fraud Detection
Websites can detect fraudulent user behavior using browser fingerprinting technology. When a website detects fraudulent user activity, it adds extra authentication steps to the login process to prevent unauthorized access and theft of legitimate users’ accounts.
Real-world browser printing example:
For instance, browser fingerprinting is used to authenticate users when they login to an online banking system. Wachovia, a financial services company, created unique fingerprinting for their customers’ devices to verify their identity with a unique identifier and block malicious users.
2. Tailored content recommendations
It’s possible to delete cookie history and block them on your web browsers. Web browsers such as Google, Firefox, Safari, and Microsoft Edge enable users to disable cookies in their web browsers. Unlike cookies, it is hard to block browser fingerprints. That’s why browser fingerprinting is a more effective technique for advertising to track users’ behaviors and activities across the web.
Websites use fingerprinting to track and analyze visitors’ activities and behaviors to create personalized experiences based on visitors’ behaviors and activities. For example, when you request a website to display its content, the website can reveal your geo-location by tracking your IP fingerprinting. This enables eCommerce sites to recommend locally relevant content and nearby stores to their online visitors. Websites can access the following information about their visitors using browser fingerprint technology:
- A user’s current location.
- The type of device the user uses, such as a desktop, tablet, or mobile phone.
- Traffic source, Traffic source, users can reach your website through different ways such as direct, social media, referral, and paid traffic.
Real-world browser fingerprinting example:
Canvas fingerprinting techniques are used by 10%1 of the Alexa top-100K websites for anti-ad fraud and potential cross-site tracking. The research team used FP-INSPECTOR to detect browser fingerprinting behaviors on the top 100K Alexa websites.
Figure 5: Distribution of Alexa top-100K websites that use browser fingerprinting technology
3. Bot detection
Websites use browser fingerprinting to protect themselves from malicious bots. Browser fingerprinting examines the HTTP headers sent by the browser to distinguish web bot traffic from regular browser traffic.
Browser fingerprinting technology analyzes client-side signals to identify web crawlers based on bot detection attributes such as the number of requests, frequency of requests, unusually high pageviews, long session durations, etc. It gathers the fingerprint of a suspicious browser and compares it to regular browsers to detect web bots based on fingerprint comparison.
Sponsored
Bright Data’s Web Unlocker enables individuals and businesses to overcome the challenge of browser fingerprinting by masking clients’ original device fingerprints and IP addresses. It helps businesses in their data collection processes by preventing scrapers from being detected.
Rotating proxy servers can also help users change the perceived origin of a web request. Check out quick summary of the top proxy server providers.
Is browser fingerprinting legal?
Privacy regulations such as GDPR and CCPA do not explicitly address online fingerprinting. However, there are regulations to track Internet users’ activities. Any information associated with an identifiable individual is subject to the GDPR. The EU’s General Data Protection Regulation (GDPR) requires companies to receive users’ consent before tracking their online activities. Tracking and collecting online users’ activity is harmless and legal as long as you do not collect and process personally identifiable information without the user’s consent.
However,
- Websites not subject to CCPA or GDPR may be collecting this data without user consent
- Websites subject to GDPR may collect some of this data under “legitimate interest” provision if they argue that they need it to operate the website. Legality of such an action would depend on how critical that data is for the business’ operations.
How can you avoid browser fingerprinting?
1. Anonymize your browser
The possibility of being recognized and tracked by websites increases as the level of browser uniqueness increases. It is difficult to avoid browser fingerprinting. However, you can lower your browser’s uniqueness.
For example, when you connect to a website, your machine sends an HTTP header-encoded connection request to the web server to disable the content. These headers contain machine-specific information such as your user agent (browser name, version, etc.), location, language, time zone, browser plugins, and other browser properties. We recommend that you anonymize or lower your browser uniqueness to avoid being easily identified by websites.
2. Leverage proxies
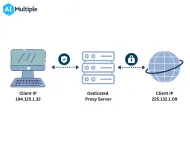
You can use a proxy server or a headless browser to make you anonymous while browsing. Shared proxies, for example, are a highly anonymous option for combating browser fingerprinting technology. Since multiple users share the same IP address with you simultaneously, being detected by website servers is hard. It blends your machine in with the machines of many other users (see Figure 5). Websites will have difficulty targeting your machine because you use a less unique configuration.
Figure 5: Representation of a shared proxy server process
Further reading
- Headless Browsers in Web Scraping: Best Practices & Use Cases
- Firewalls vs Proxy Servers: Overview, Techniques and Benefits
Also do not forget to check out data-driven list of web scrapers,
If you have any further questions about browser fingerprinting, reach out to us:
External Links
- 1. Iqbal, Umar; Englehardt, Steven; Shafiq, Zubair(2021). “Fingerprinting the Fingerprinters: Learning to Detect Browser Fingerprinting Behaviors“. IEEE Computer Society Digital Library. Retrieved November 18, 2022

Comments
Your email address will not be published. All fields are required.